Kokomo Finance, a lending protocol that had recently launched on Optimism, rug pulls users and disappears with approximately $4 million worth of tokens. The project’s token, KOKO, had only been launched less than 36 hours before the rug. The rug occurred through changes made by the project’s deployer address, which rugged Wrapped Bitcoin deposits. The project deleted its website, Twitter, GitHub, and Medium soon after.
Hack Impact
Kokomo Finance has taken off with approximately $4 million worth of user funds, leaving users unable to withdraw their funds. The project rugged Wrapped Bitcoin deposits, leaving almost $2M of tokens in its pools on Optimism.
Background
The KOKO Token deployer, with address 0x41BE, created a malicious cBTC contract. They modified the reward speed and paused borrowing. Next, they replaced the implementation contract with the malicious one using the function below. Another address, 0x5a2d, approved the cBTC contract to spend 7010 sonne WBTC. After the implementation contract was switched to the malicious cBTC contract, the attacker used the 0x804edaad method to transfer sonne WBTC to address 0x5C8d. Finally, the address 0x5C8d swapped 7010 sonne WBTC for 141 WBTC (~4M) in profit.
Code
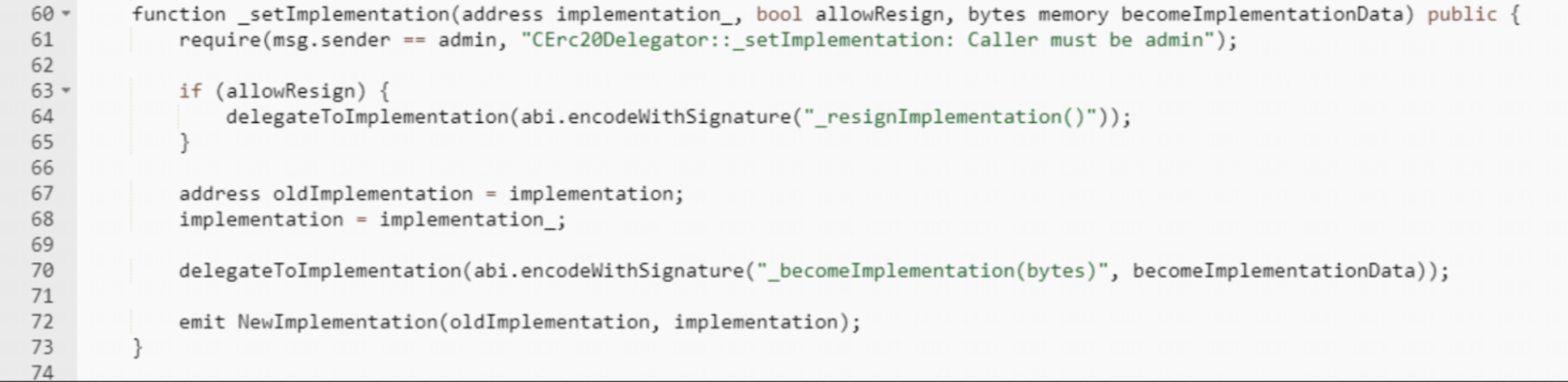
Steps to reproduce
- The attacker deployed a contract called cBTC, then changed its implementation to a malicious contract. The attacker then called the 0x804edaad method to transfer tokens to a different address and ultimately swapped those tokens for profit.
Transaction Analysis
The four addresses currently hold the stolen funds:
- 0x8C0eCD7BACCed114729F8269B459E0A4D5e95C3b 50 BTCB ($1.4M)
- 0xB74C5e41E748BaBC32ce33813549E2503CDaB762 40 BTCB ($1.1M)
- 0xC2AE8D3b0fb159cCD331a01A8C3632B95dB23CF5 32 BTCB ($0.9M)
- 0x88340ff2292506D0D93934CbBFEA5ED1804CDa0d 20 WBTC ($0.6M)
Rugpull Indicators
Here are some indicators to look for in a smart contract that may indicate it could be a rug pull:
- Anonymous or unknown team: A team that is anonymous or unknown should be a red flag. Why? as they may not have any reputation to uphold and can disappear easily.
- Unaudited code: A smart contract that has not been audited or reviewed by reputable third-party auditors increases the risk of vulnerabilities and potential exploits.
- Centralized control: A smart contract that gives excessive control to the owner or a small group of individuals can lead to potential misuse of funds or a rug pull.
- Lack of transparency: A rug pull often involves a lack of transparency or information on the project, such as unclear tokenomics or a lack of information on the team or project roadmap.
- Unrealistic promises: Projects that make unrealistic promises of high returns or quick profits without a clear explanation of how these returns will be generated should be approached with caution.
- Lack of liquidity: If a project has low liquidity or a small number of holders, it may be easier for a rug pull to occur as there may not be enough holders to prevent a large-scale dump.
- Sudden changes or delays: A sudden change in the project roadmap or significant delays in project milestones without proper communication to investors can be a warning sign of a potential rug pull.
Conclusion
Kokomo Finance’s rugpull highlights the need for thorough security audits and proper measures in decentralized finance. The rug occurred via the deployer address. It’s crucial to audit and secure all protocol aspects.
Explore further Hack Analysis:
Hack Analysis on Euler Finance
DeFiGeek Community JAPAN Hack Analysis
Cream Finance Hack: What Motivates Hackers To Return Stolen Funds?































