Zunami Hack Analysis
Zunami is a decentralized protocol operating in the Web3 space, specializing in issuing aggregated stablecoins like UZD and zETH. These stablecoins are generated from omnipools that employ various profit-generating strategies. Recently, the protocol was exploited, resulting in a loss of $2.1M. The exploit specifically targeted Zunami’s UZD and zETH liquidity pools on the Curve ecosystem. This analysis delves into the impact and mechanisms for this kind of vulnerability.
Hack Impact
The Zunami Protocol experienced a severe price manipulation attack that led to a loss of approximately $2.1M. The attacker was able to exploit Zunami’s zETH and UZD liquidity pools on the Curve platform. This caused the zStables (zETH and UZD) to depeg dramatically – zETH by 85% and UZD by 99%.
The Hack Explained:
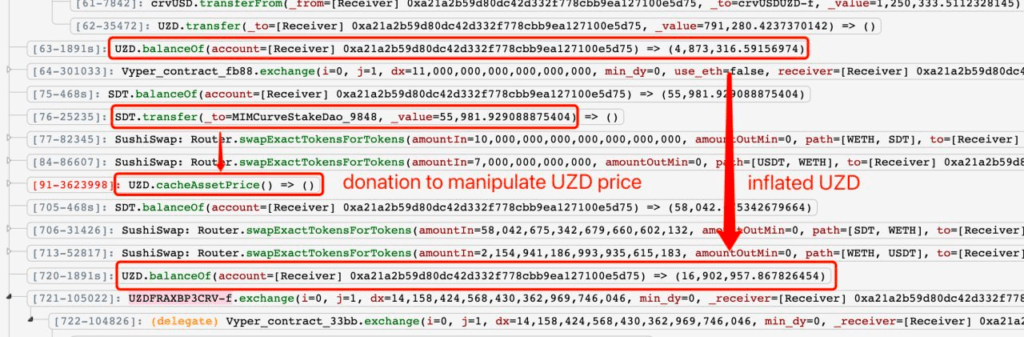
- Flash Loans: The attacker borrowed 7,000,000 USDT from Uniswap v3, 7,000,000 USDC, and 10,011 WETH from Balancer.
- Liquidity Manipulation: Using the borrowed 5,750,000 USDC, the attacker minted 5,746,896 Curve tokens (crvFrax). These were then swapped for 4,082,046 UZD and 791,280 UZD using 1,250,000 USDC in Curve Finance.
- Price Manipulation Step 1: The attacker swapped 11 WETH for 55,981 SDT in Curve and then donated all to the MIMCurveStakeDAO, initially inflating the SDT price.
- Price Manipulation Step 2: The attacker swapped an additional 10,000 WETH for 58,043 SDT and exchanged 7,000,000 USDT for 2,154 WETH in Sushiswap, further escalating the SDT price manipulation.
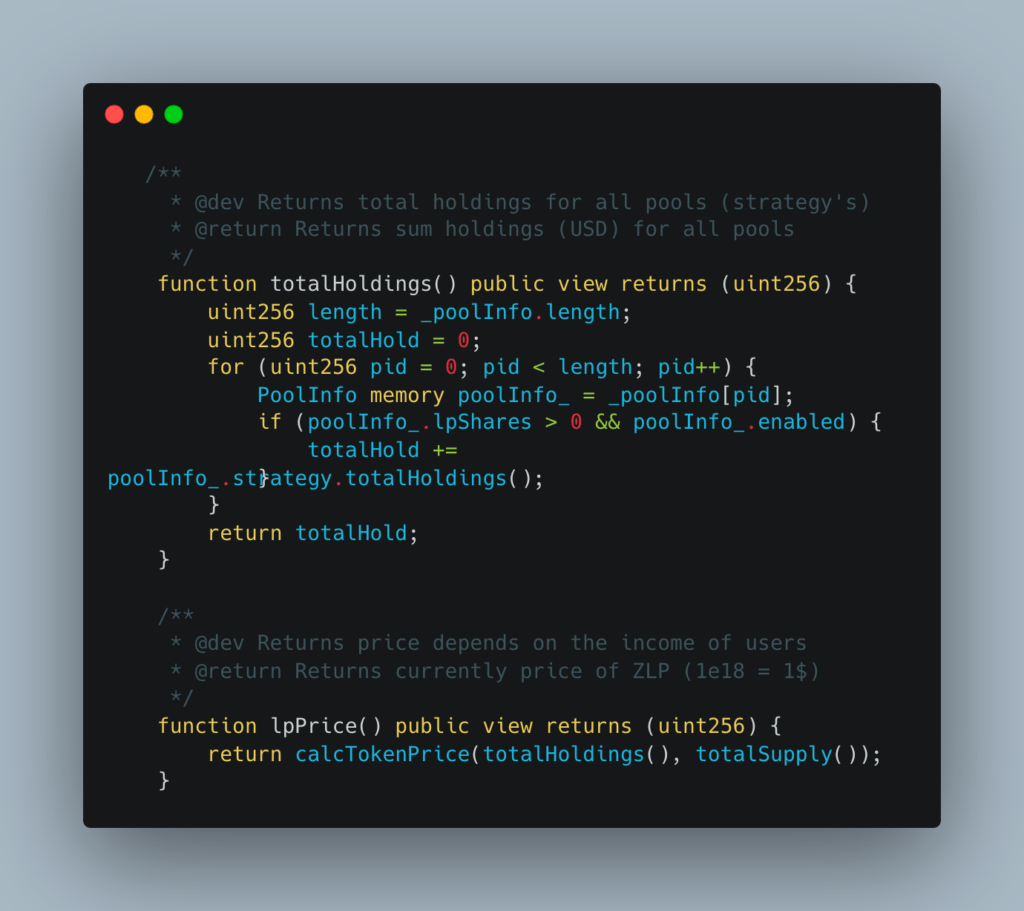
- Flaw in totalHoldings Function: The attacker manipulated the flawed totalHoldings function in strategies like MIMCurveStakeDao. This manipulation involved artificially inflating sdt and sdtPrice, leading to incorrect liquidity pool (LP) price calculations.
- Cache Manipulation: The attacker then cached this manipulated price into the UZD contract via the cacheAssetPrice function, inflating their balance in the UZD contract.
- Profit Realization: Finally, the attacker reversed all operations that manipulated the UZD price and converted all the inflated UZD into a profit of approximately (~$2.1M at the time of the attack).
Transactions Involved
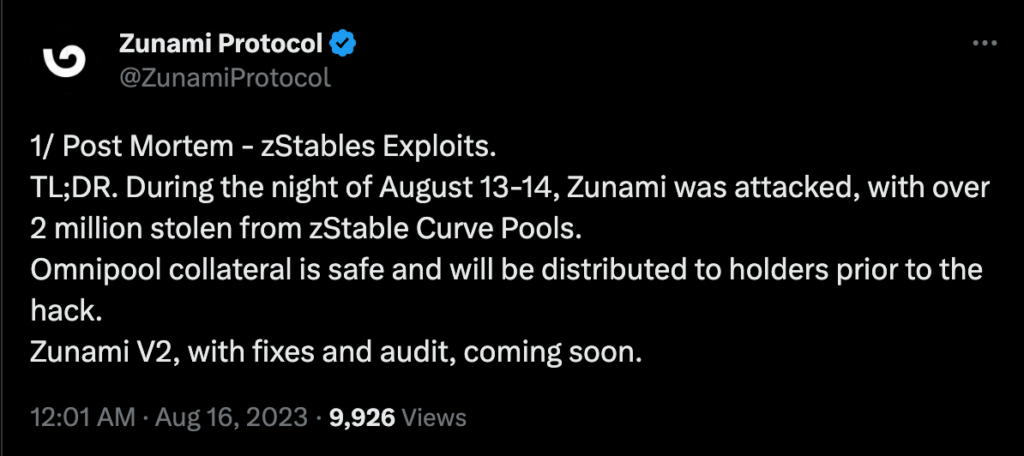
Protocol Response
Conclusion
The Zunami Protocol hack serves as a cautionary tale about the risks and vulnerabilities present in complex decentralized financial systems. The exploitation capitalized on multiple weaknesses in Zunami’s design, leading to a substantial loss of funds and trust. Given the growing number of such exploits, it’s imperative for projects in the DeFi space to take robust security measures seriously, undergoing rigorous audits from a reputed audit firm like Blockapex and implementing strong protective mechanisms to shield both their assets and their user base.
Explore further Hack Analysis: