Euler Finance is a decentralized finance (DeFi) platform that enables users to lend, borrow, and leverage their digital assets. It functions as a permissionless and trustless lending market built on the Ethereum blockchain, aiming to create an open, transparent, and efficient financial ecosystem. Users can deposit their assets into the platform, receiving interest-earning tokens (ETokens) in return, while borrowers can take out loans in the form of Debt Tokens (DTokens) against their deposited collateral.
The platform’s innovative features and decentralized architecture have made it an attractive choice for DeFi enthusiasts, but its complex smart contract system has also exposed vulnerabilities that can be exploited by malicious actors. In this hack analysis, we will delve into the Euler Finance hack, where attackers exploited a health score flaw and a lack of liquidity checks to manipulate the system and profit from it.
Hack Impact
The Euler Finance hack had a devastating impact on the platform and its users, with approximately $197 million worth of assets stolen, including ETH, WBTC, USDC, and DAI. This placed Euler Finance at number 6 on the leaderboard of the largest DeFi hacks. The platform’s total value locked (TVL) dropped from $264 million to just $10 million.
The exploit not only had a direct financial impact on the affected users but also undermined the trust and confidence in the platform and its security measures. Many other DeFi projects had funds tied up in the protocol, and they experienced losses as well. Some of the affected projects include Angle Protocol, Balancer, Temple DAO, Idle DAO, Swissborg, Yield Protocol, Yearn, Inverse Finance, and others.
Health Score, Liquidation Checks, and Over-leveraged Minting:
In the context of Euler Finance, the health score is a measure of the solvency of a user’s position on the platform. It compares the value of the user’s eTokens (collateral) to their dTokens (debt). A healthy position would have a higher value of collateral compared to the debt. This ensures that the user can repay their debt and maintain the security of their assets. If the health score drops below a certain threshold, the user’s position may become subject to liquidation.
Liquidation checks are mechanisms put in place by the DeFi platform to monitor the health score of users’ positions and initiate liquidation when necessary. When a position becomes under-collateralized, the platform can liquidate the user’s collateral to recover the debt. This process usually involves selling the collateral at a discount to incentivize liquidators to participate and facilitate the recovery of the debt.
Over-leveraged minting refers to a situation where a user borrows more assets than their collateral can support, creating a highly leveraged position. In this scenario, the user’s health score would be low, and their position would be at risk of liquidation. Over-leveraging can lead to rapid liquidation events, especially during periods of market volatility, when the value of the collateral might fluctuate significantly. This increases the risk for both the borrower and the platform, as it may become difficult to recover the full value of the outstanding debt.
Euler Finance Hack Explained with a Simplified Bank Analogy
To help non-technical users understand the Euler Finance hack, we will use a bank analogy. This explanation aims to simplify the complex DeFi concepts and make the attack more accessible to everyone. In this scenario, the attacker initially takes a loan (akin to a flash loan in DeFi) from a third party.
The Attack
Borrowing from the bank
Imagine a person (the attacker) goes to a bank and takes a loan of $100, providing collateral worth $100 (similar to depositing DAI and receiving eDAI tokens).
Over-leveraging
Now, the attacker repeatedly uses the borrowed money to take additional loans, increasing their debt while providing more collateral each time (akin to over-leveraging their position in the Euler Finance platform). They do this multiple times, reaching a total debt of $1,000 and collateral worth $1,000.
Partial loan repayment
At this point, the attacker decides to pay back a portion of the loan (equivalent to donating eDAI tokens to the Euler Finance reserves). They repay $100, leaving them with $900 of debt and $1,000 worth of collateral.
Under-collateralized and triggering liquidation
However, by repaying this portion of the loan, the attacker becomes under-collateralized. In a real bank scenario, this could lead to the bank seizing the collateral to cover the remaining debt. In the Euler Finance platform, this triggers a liquidation process.
Liquidator steps in
Now, another person (the liquidator contract) sees this opportunity and offers to buy the collateral at a discounted price, say 20% less, from the bank (or in this case, the Euler Finance platform). The liquidator pays $800 to acquire the collateral, which they believe can be sold for more than what they paid.
Selling collateral at a profit
The liquidator then sells the acquired collateral at a higher price, benefiting from the difference. In the Euler Finance hack, the attacker exploited a vulnerability that allowed them to artificially increase the value of the collateral, which led to a higher profit when the liquidator (a contract controlled by the attacker) sold it. After making a profit, the attacker repays the initial loan (the flash loan) to the third party.
In summary, the attacker used a series of transactions to over-leverage their position, manipulate the system, and profit from the liquidation process.
Euler Finance Hack: A Technical Breakdown
The attacker exploited a vulnerability in the protocol by using two smart contracts: one to create an over-leveraged position (violator) and another to act as a liquidator. This detailed technical explanation will outline the steps taken by the attacker to exploit the system and profit from the vulnerability.
The Attack
Flash loan and initial deposit
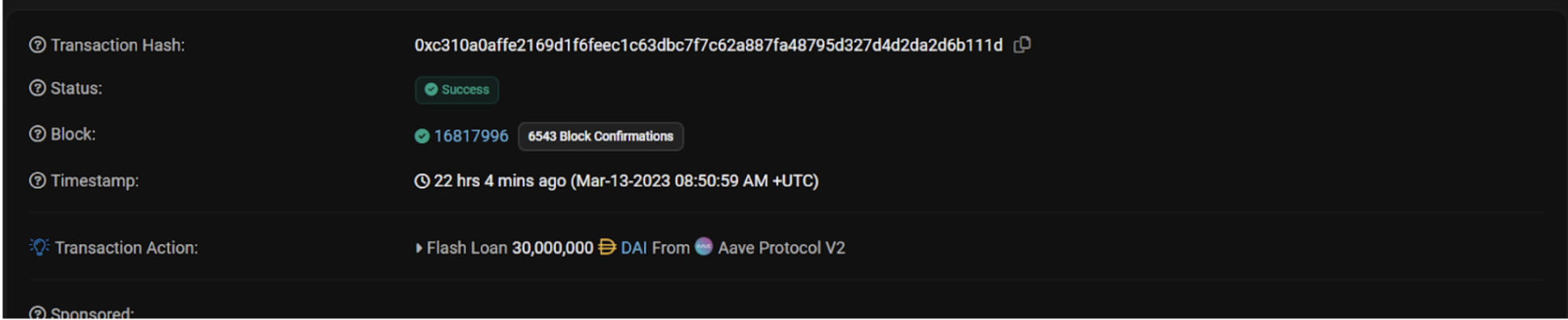
The hacker created three contracts: a primary contract and two others for violation and liquidation. They obtained a flash loan of 30 million DAI from Aave and sent it to the violation contract.
Depositing DAI and leveraging
The hacker deposited 20 million DAI into Euler Protocol and received approximately 19.6 million eDAI in return. They then leveraged the 19.6 million eDAI to borrow around 195.6 million eDAI and 200 million dDAI.
Partial repayment and leveraging again
The attacker used the remaining 10 million DAI from the flash loan to repay some of their debt, reducing the balance to 190 million dDAI. The health score of the borrowing account was now within the acceptable range. The hacker then borrowed another 195.6 million eDAI and 200 million dDAI.
Donating to reserves and triggering under-collateralization
The hacker donated 100 million eDAI to the Euler protocol reserve using the violation contract, by calling the donateToReserve function. This donation caused the account to become under-collateralized, allowing the liquidator to step in.
Liquidation, discounted purchase of collateral, and skewed exchange rate
The liquidation contract, controlled by the attacker, successfully executed the liquidation call on the account with a low health score. This triggered the maximum 20% liquidation discount, allowing the attacker to acquire dDAI tokens at a favorable rate of 1.25 eDAI per dDAI. The attacker received 310 million eDAI and 254 million dDAI as a result.
Moreover, the attacker took advantage of the skewed eDAI to DAI exchange rate of approximately 0.97 eDAI per DAI, caused by the artificially increased total borrows during the liquidation process. This favorable rate allowed the attacker to convert their eDAI tokens back to DAI at a more profitable rate, ultimately generating a substantial profit from the exploit.
Repaying the flash loan and profiting from the attack
The attacker repaid the 30 million DAI flash loan to Aave and made a profit of about 8.7 million DAI from the exploit.
Exploiting other assets
The attacker used a similar approach to exploit other assets, including WETH. They borrowed 20,895 WETH as a flash loan from Aave, deposited 13,930 WETH into the EToken pool, minted ETokens, paid 6,965 WETH to improve the health score, minted 13,930 WETH, and donated 69,650 WETH. The liquidation contract received 28,994 WETH, and after repaying Aave, the attacker made a profit of 8,099 ETH (worth approximately $135,630,71).
In conclusion, the attacker exploited a vulnerability in the Euler Finance protocol by using multiple smart contracts to manipulate the system, create over-leveraged positions, donate to reserves, trigger under-collateralization, and profit from the liquidation process with discounted rates and skewed exchange rates.
A Closer Look at the Flawed Liquidity Check
Euler Finance’s donateToReserves function is designed to enable users to deposit funds into the reserved address. When calling this function, users hold both Debt Tokens (DToken) and Equity Tokens (EToken). The vulnerability in this function arises from the lack of proper liquidity checks, which allows users to under-collateralize their leverage by donating their EToken to the reserve while their DToken remains unchanged. This ultimately creates a form of technical bad debt that the hacker exploited.
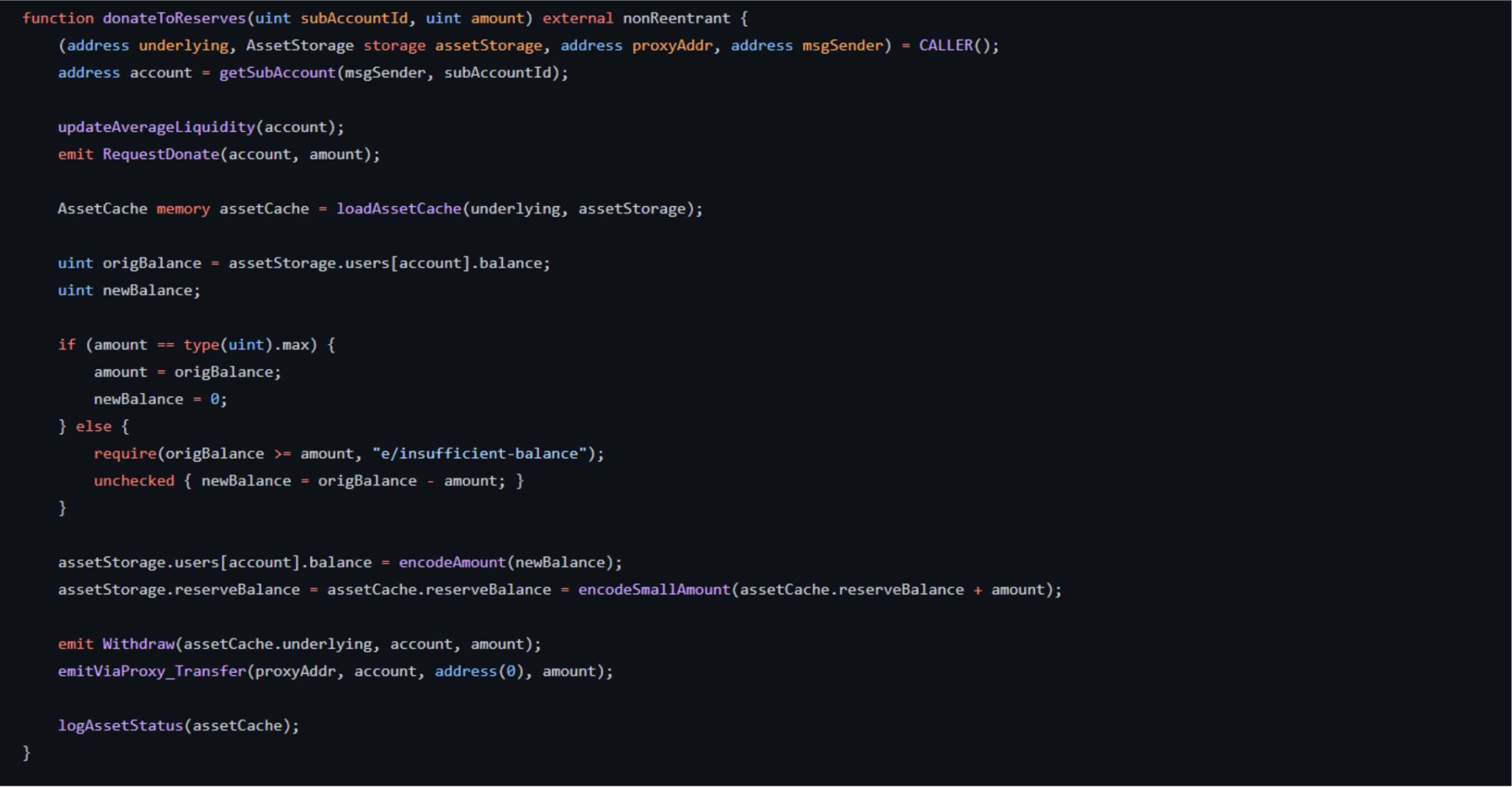
The main issue in this code snippet is the lack of a liquidity status check for the borrower. Consequently, the hacker’s liquidation contract was able to successfully withdraw from the protocol by exploiting this vulnerability, leading to the Euler Finance hack.
The Health Score Flaw
This flaw in Euler Finance occurs due to a design issue in the system used for assigning health scores to accounts. This flaw allows insolvent accounts to access collateral without repaying their outstanding debt. The underlying logic is that seizing a borrower’s entire collateral doesn’t guarantee solvency, so the remaining collateral should be sufficient. Unfortunately, this logic can be exploited by attackers who engage in under-collateralized leverage, creating a vulnerability in the system.
Transaction Analysis
Attacker’s address where the funds remain: 0xb66cd966670d962c227b3eaba30a872dbfb995db tx DAI: 0xc310a0af…
Conclusion
In conclusion, the attack on Euler Finance provides valuable lessons for projects in the DeFi space:
Thorough testing is crucial. The donateToReserve function in Euler Finance was not adequately tested (Github), particularly for scenarios such as donating after borrowing and the health score after donating. If the team had tested the function against all possible scenarios, the attack might have been prevented. This highlights the importance of comprehensive testing, especially when introducing new logic or functions to an existing codebase.
Continuous improvements and updates to smart contracts should be carefully tested and reviewed to ensure they do not introduce new vulnerabilities. By learning from this incident, projects can take steps to safeguard their systems and protect their users’ assets from potential exploits.
Explore further Hack Analysis:
Cream Finance Hack: What Motivates Hackers To Return Stolen Funds?