Decentralized Finance (DeFi) represents a radical shift in the financial landscape by utilizing blockchain technology to offer financial services without traditional intermediaries like banks. The growth of DeFi has been remarkable, with the total value locked in these systems soaring about $700 million two years ago to reach an all time high, $179 billion by December 2021.
This rapid expansion underscores the potential of DeFi to revolutionize finance, but it also brings to light significant challenges, particularly in understanding and managing its security risks. As the ecosystem evolves, we face new complexities in grasping how DeFi operates and how to safeguard it against emerging threats.
This article will provide an in-depth look at DeFi, starting with its core principles and key components, such as stablecoins, decentralized exchanges, and other innovations. We’ll explore the major security challenges and optimization strategies within the DeFi landscape, and offer insights into ongoing research and future directions.
What is DeFi?
Technically speaking, Decentralized finance (DeFi) is an emerging financial technology based on secure distributed ledgers similar to those used by cryptocurrencies. DeFi operates through peer-to-peer financial networks, leveraging blockchain technology, advanced security protocols, and modern software and hardware. By using these innovations, DeFi eliminates the need for traditional intermediaries like banks, which charge fees for their services. The decentralized approach reduces costs and simplifies transactions by removing middlemen.
As CoinDesk aptly describes it, DeFi is an:
“an umbrella term for a variety of financial applications in cryptocurrency or blockchain geared toward disrupting financial intermediaries.”
In essence, DeFi leverages blockchain to create an open, permissionless financial ecosystem where users can engage directly with financial services, bypassing conventional gatekeepers.
To gain a comprehensive understanding of DeFi, read more here.
We’ll briefly cover some primitive concepts so they can aid you in grasping the key security challenges in DeFi.
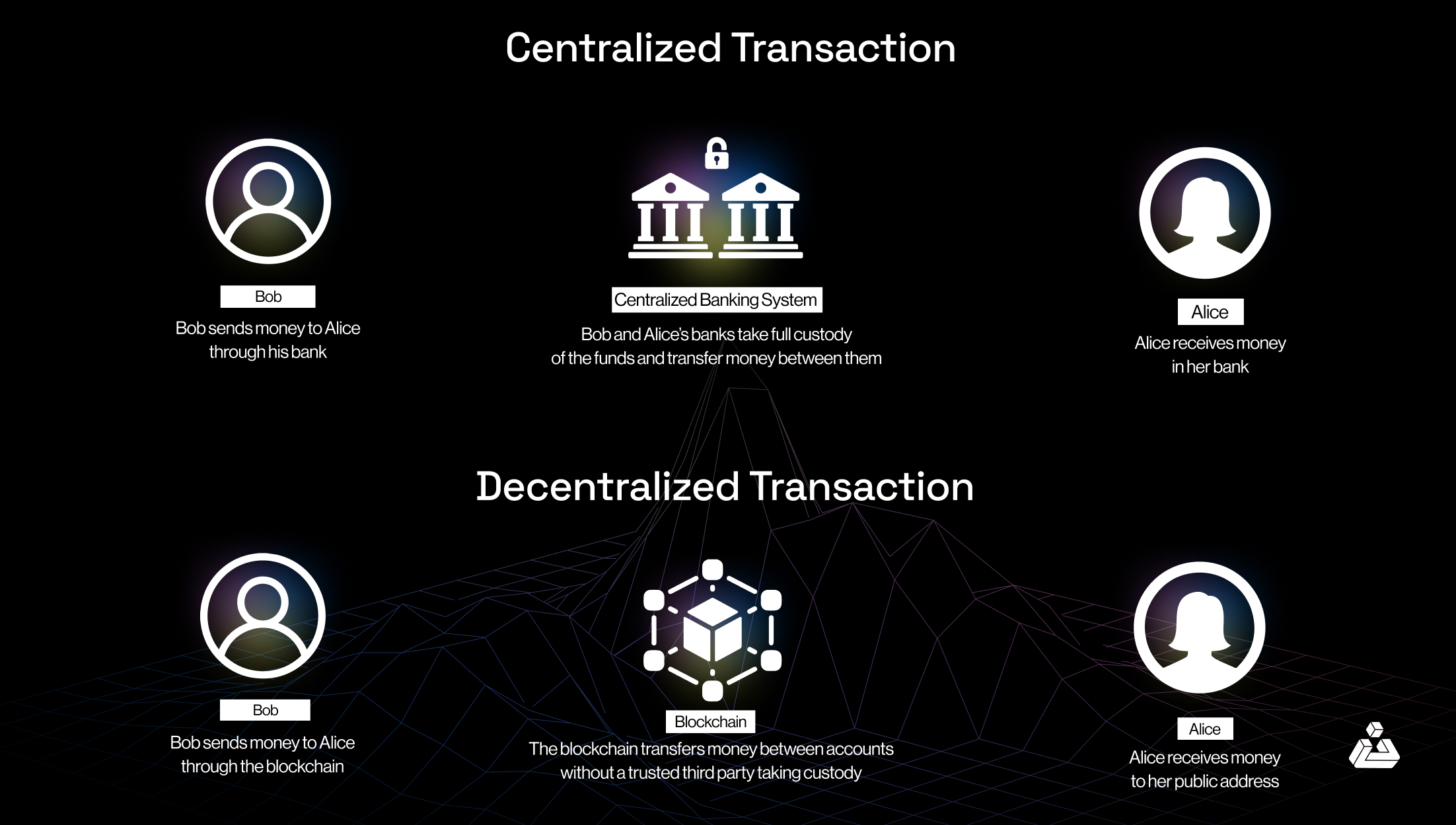
DeFi Properties
DeFi, in its ideal form, exhibits four properties. DeFi is:
-
Non-custodial
Participants have full control over their funds at any point in time
-
Permissionless
Anyone can interact with financial services without being censored or blocked by a third party
-
Openly auditable
Anyone can audit the state of the system, e.g., to verify that it is healthy
-
Composable
Its financial services can be arbitrarily composed such that new financial products and services can be created (similar to how one is able to conceive new Lego models based on a few basic building blocks)
Core components of DeFi
-
Smart contracts
Smart contracts are self-executing agreements with the terms directly written into code. They automate transactions and enforce rules without intermediaries, ensuring that transaction either completes fully or fails entirely, maintaining a consistent state. These contracts operate on blockchain networks, such as the Ethereum Virtual Machine (EVM), which processes transactions and updates the state based on predefined conditions. For example, a lending protocol might use a smart contract to automate lending processes.
-
Tokens
In DeFi, tokens are digital representations of assets on a blockchain. They can include native cryptocurrencies, like Ether (ETH) on Ethereum, or tokenized assets such as real estate or stocks. Tokens facilitate various DeFi functionalities, including trading, lending, and staking. For instance, DAI is a stablecoin token issued by MakerDAO that maintains a stable value relative to the US dollar and is used for decentralized lending and borrowing.
-
Decentralized Applications (dApps)
DApps are applications that operate on a blockchain or peer-to-peer network, leveraging decentralization to offer services that are more transparent, secure, and resistant to censorship than traditional applications. These applications interact with smart contracts to perform complex financial operations without a central authority.
Types of DeFi Platforms
-
Lending & Borrowing Platforms
Decentralized lending and borrowing platforms empower users to lend and borrow digital assets without traditional intermediaries. Through smart contracts, these platforms automate the process of setting interest rates and managing collateral. Users who lend their assets earn interest, while borrowers must provide collateral, which the smart contract holds until the loan is repaid. This system ensures transparency and efficiency in financial transactions. Examples of such platforms include:
-
Bridges
Blockchain bridges are systems that enable the transfer of assets and data between different blockchain networks. They can be categorized into decentralized, centralized, or hybrid types. By connecting various blockchain ecosystems, these bridges facilitate smooth interactions and exchanges of assets and information across distinct platforms. Examples of Bridges include:
To learn more about Blockchain Bridges, read here.
-
Decentralized Exchanges (DEX):
Decentralized exchanges (DEXs) facilitate cryptocurrency trading directly from users’ wallets without the need for a centralized intermediary. DEXs operate using smart contracts to match buyers and sellers, ensuring transparency and reducing reliance on central authorities. They offer a more decentralized alternative to traditional exchanges, maintaining the ethos of decentralization by allowing peer-to-peer trading.
-
Yield Farming and Liquidity Mining:
Yield farming and liquidity mining involve providing liquidity to DeFi platforms in exchange for rewards. Users contribute assets to liquidity pools or lending protocols and earn returns in the form of additional tokens or fees. These practices incentivize participation in DeFi ecosystems, allowing users to maximize their yield by leveraging various protocols. Examples include:
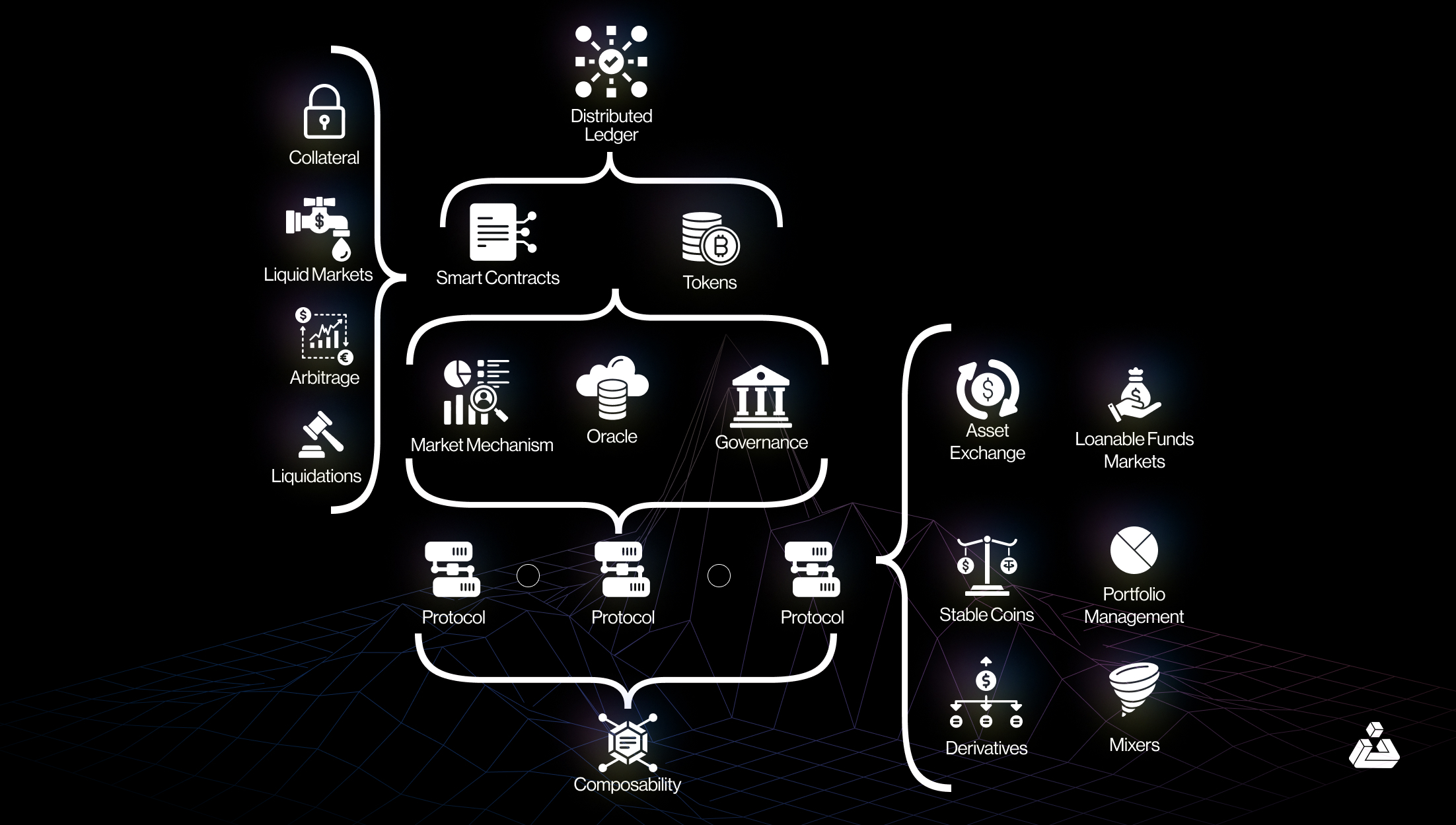
A conceptual overview of the different constructs within the DeFi ecosystem
DeFi Security
Before we highlight both the solutions and risks, we aim to shed light on DeFi Security and its associated technical and economic aspects. DeFi security is vital for ensuring the integrity and functionality of decentralized financial systems, which are vulnerable to a range of attacks. Technical security primarily focuses on safeguarding protocols from direct vulnerabilities and exploits in the code. For eg: sandwich attacks involve exploiting the order of transactions to profit at the expense of others, a direct technical exploit that manipulates transaction sequencing to steal assets. Another example is Miner Extractable Value (MEV), where miners reorder transactions to extract additional value, signifying the need for secure transaction processing mechanisms.
Economic security, on the other hand, addresses vulnerabilities arising from market manipulation and incentive structures. Economic exploits, such as manipulating asset prices over time to trigger liquidation events, leverage market dynamics rather than code flaws. Governance Extractable Value (GEV) poses risks when governance mechanisms are manipulated for personal gain, potentially undermining the protocol’s stability.
DeFi Security Challenges
We are going to have a look at some major security challenges and their implications.
-
Smart Contract Vulnerabilities
Smart contracts are susceptible to bugs and exploits. Flawed code can lead to significant losses, such as the 2016 DAO hack where $50 million was stolen due to a coding error. Similarly, unaudited contracts are high-risk; the 2022 Ronin Network attack resulted in over $600 million in losses due to inadequate security audits.
-
Protocol Interactions
DeFi protocols often interact in complex ways, which can propagate vulnerabilities. For instance, the 2021 Cream Finance hack exploited cross-protocol vulnerabilities to steal $130 million. The bZx attacks of 2020 used flash loans to manipulate prices, causing over $50 million in losses.
-
Centralized Points of Failure
Despite DeFi’s decentralization, centralized components like oracles and admin keys pose risks. The March 2023 attack on the QuickSwap exchange exploited a Curve LP oracle vulnerability, leading to a $188,000 loss. Similarly, the 2022 BadgerDAO hack compromised an admin key, resulting in $120 million stolen.
-
Front-Running and Arbitrage Bots
Transaction transparency in DeFi can lead to front-running, where bots exploit pending transactions for profit. An example is the Merlin DEX hack, where bots manipulated LP tokens to drain funds. Arbitrage bots also exploit price discrepancies, destabilizing markets as seen in the Curve attacks.
-
Impermanent Loss
Liquidity providers face risks from price fluctuations within liquidity pools, which can lead to losses when withdrawing funds. This challenge is inherent in DeFi liquidity provision and affects user returns.
-
Lack of Regulation and Consumer Protection
The unregulated nature of DeFi means limited recourse for users affected by scams or failures. The 2022 Mirror Protocol hack, which resulted in $90 million in losses, exemplifies the lack of legal protections in the DeFi space.
-
Composability Risks
Composability allows DeFi protocols to interact and build upon each other, creating innovative financial products. However, this interconnectedness also introduces risks where a vulnerability in one protocol can affect others. For example, a single exploit in a protocol’s smart contract could cascade through the ecosystem, leading to widespread financial damage.
-
Oracles
Oracles provide essential off-chain data to smart contracts but are vulnerable to manipulation and inaccuracies. Ensuring that oracles report correct data and incentivize honest reporting is a significant challenge. Improving oracle designs is critical in creating robust incentive structures, and evaluating the security of various oracle mechanisms, such as reputation systems.
-
Anonymity and Privacy
Balancing user privacy with preventing abuse is a critical issue. While privacy-preserving technologies like zero-knowledge proofs show promise, their high computational cost limits their adoption.
Effective governance in DeFi faces challenges like designing incentives, balancing stakeholder power, and protecting minority interests, while miner extractable value (MEV) can create inefficiencies and unfair advantages in markets. Program analysis tools, often limited by their inability to assess interactions between contracts, need advancement to handle the complexity of smart contracts. The biggest challenge across these areas is ensuring comprehensive security and fairness amidst evolving and intricate DeFi systems.
Human factor is also a prominent issue in DeFi Security as users often show negligence and lack awareness of best practices, like sending funds to incorrect addresses or using weak passwords, which can jeopardize DeFi security. Users can enhance safety by employing strong passwords, verifying addresses, enabling 2FA, and staying informed about potential threats.
Let’s move to best practices to avoid these issues and mitigate their implications.
Best Practices for DeFi Security
-
Rigorous Code Audits
Engage reputable third-party organizations for comprehensive smart contract audits. This ensures a thorough examination of the code for vulnerabilities, optimizes performance, and validates the platform’s security and reliability.
-
Bug Bounty Programs
Implement community-driven bug bounty programs to incentivize ethical hackers and developers. Offering rewards for identifying and reporting vulnerabilities enhances system resilience and improves security through diverse perspectives.
-
Insurance for DeFi Products
Utilize platforms like Nexus Mutual for insurance-like coverage against smart contract failures. This additional layer of security ensures user compensation in the event of unforeseen hacks or failures.
-
Layer-2 Scaling Solutions
Integrate layer-2 or off-chain solutions to reduce network congestion, lower gas fees, and improve transaction speed and reliability. This enhances user experience and minimizes transaction failures due to network issues.
-
Decentralized Governance
Adopt decentralized governance models to involve the community in decision-making processes. This approach mitigates risks associated with centralized points of failure and ensures collective oversight in protocol upgrades and security measures.
-
Two-Factor Authentication (2FA)
Implement 2FA on wallets to add an extra security layer, making it more difficult for unauthorized access even if passwords are compromised. Encourage users to use strong passwords and secure their wallets.
-
Risk Management Strategies
Promote DeFi portfolio diversification and sound risk management practices. Advise users to limit exposure with strategies like the 1% rule, stop-loss orders, and thorough research before investing.
-
Development of Robust Regulations
Regulatory compliance is a significant challenge for DeFi security. However, robust regulations are imminent, with global efforts underway. For instance, the European Union’s MiCA proposal and the U.S. Lummis-Gillibrand Act aim to address crypto oversight, consumer protection, and stablecoin regulation.
Conclusion
Decentralized finance (DeFi) will keep expanding and attracting more global interest. To sustain this growth, the DeFi sector must magnify and address the challenges it faces whilst enhancing security by implementing robust best practices and effective solutions, thereby maximizing protection for users’ funds.
At BlockApex, we’re dedicated to advancing the security of the Web3 space and bolstering trust in DeFi projects.
Our team utilizes cutting-edge techniques, industry best practices, and comprehensive tools to assess smart contracts across various domains and protocols. By adhering to industry standards, we ensure top-notch security and help you achieve your business objectives.
Contact us today to receive a quote for your smart contract security audit and enhance your project’s reliability!































