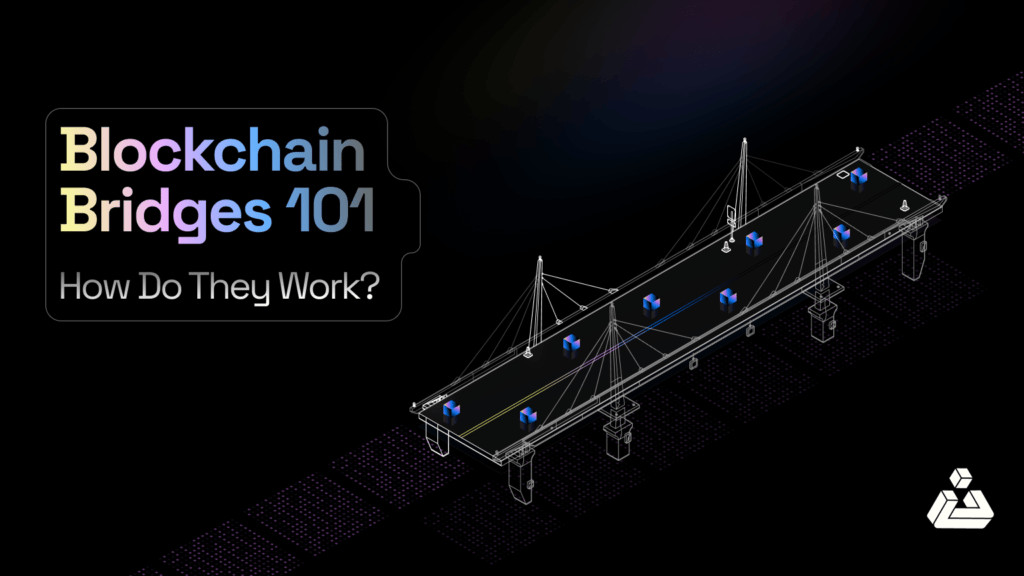
Blockchain bridges are platforms that facilitate the transfer of assets and data from one blockchain ecosystem to another. They can be decentralized, centralized, or even hybrid. These bridges enable the communication and interaction between different blockchain networks, allowing for the seamless transfer of assets and data across various platforms.
Why use Blockchain Bridges?
The concept of blockchain bridges initially confused me. ‘Why have a bridge when every blockchain is different for a reason so why connect them?’
But all this confusion goes away if you just imagine each blockchain are cities. Each city has a different infrastructure and uniqueness. If coins are people, by not having bridges we will have the problem of fragmentation. This is why blockchain bridges are essential. But there are many more reasons,
- Interoperability: Bridges allow people and goods to travel between cities. The same goes for blockchain bridges, they enable different blockchain networks to communicate and exchange data and assets, facilitating cross-chain transactions and opening up new opportunities for decentralized applications.
- Access to a broader range of services and assets: Just like visiting different cities, which lets you access different shops, restaurants, and services, bridges let you access a wider range of blockchain-based services and assets.
- Leveraging each other’s strengths: Cities can specialize in different areas, like manufacturing or tourism. Similarly, blockchains can leverage each other’s strengths, such as security or scalability.
- Increased liquidity: Bridges can increase liquidity in a city by attracting more people and businesses, just like they can increase liquidity in the blockchain ecosystem by connecting different user bases.
- Reduced transaction costs: Bridges can reduce the cost of travel between cities by providing more efficient routes, just like they can reduce transaction costs by eliminating the need for intermediaries.
- Improved user experience: Bridges make it easier and faster to travel between cities, just like they make it easier and faster to transfer assets between blockchains.
- Increased adoption: Bridges can encourage more people to visit and live in different cities, just like they can encourage more users to adopt and use different blockchains.
- New use cases and applications: Bridges can enable new travel routes and businesses between cities, just like they can enable new use cases and applications that were previously not possible due to isolated blockchains.
I hope with this we have a clearer understanding of the need for blockchain bridges.
How do Blockchain Bridges Work?
Blockchain bridges work by creating a connection between different blockchain ecosystems. This connection can be achieved through various methods, such as:
- Smart contracts: These self-executing smart contracts on both blockchains manage the locking and transfer of assets.
- Cryptographic algorithms: Secure algorithms ensure the integrity and authenticity of transferred assets.
- Specialized protocols: Bridges often rely on custom protocols designed for specific cross-chain interactions.
Once the bridge is established, users can transfer assets between blockchains. There are two primary methods used by blockchain bridges to facilitate asset transfer:
Wrapped Assets Method
- This method involves locking the native asset on the source blockchain and issuing a corresponding “wrapped” asset on the target blockchain.
- The locked asset is essentially held in escrow by the bridge, ensuring its equivalent value is maintained.
- This method is often used for bridging popular assets like ETH, BTC, and stablecoins.
Liquidity Pool Method
- This method utilizes pre-funded pools of assets on both the source and target blockchains.
- Users can bridge assets by drawing from the pool on the target chain, with the bridge replenishing the pool from the source chain’s pool.
- This method can be more efficient for bridging smaller or less popular assets, as it avoids the need for individual locking and minting.
Benefits of Blockchain Bridges
Blockchain bridges offer several benefits, including:
- DeFi Growth: Bridges empower users to access and optimize DeFi protocols across multiple networks, maximizing yield opportunities and diversifying risk.
- Liquidity Liberation: Trapped assets gain freedom, injecting crucial liquidity into decentralized exchanges and fostering efficient price discovery across diverse token ecosystems.
- Innovation: Unfettered asset flow fuels the development of next-generation cross-chain applications and protocols, leading to unprecedented levels of collaboration and innovation within the cryptosphere.
Types of Blockchain Bridges
Blockchain bridges can be categorized into different types based on their functionality and model, these are:
-
Trusted Bridges
These bridges are controlled by a single entity, like Binance Bridge. When using a trusted bridge, users relinquish control of their assets to the centralized authority during the bridging process. This means placing trust in the entity’s integrity and security practices to ensure the safe handling of your funds.
Trusted bridges offer advantages like faster transactions and lower gas fees. However, they introduce a single point of failure, making them more susceptible to hacks and security breaches.
-
Trustless Bridges
Unlike their trusted counterparts, trustless bridges rely on algorithms and smart contracts for facilitation. This eliminates the need for a central authority, making them more secure and aligned with the core principles of DeFi. Users retain control of their funds throughout the bridging process but are also responsible for their own security.
While trustless bridges might be slower and incur higher fees, they offer enhanced security and decentralization.
-
Hybrid Bridges
Hybrid bridges in blockchain are a type of bridge that combines elements of both trusted and trustless bridges. In a typical hybrid bridge, a centralized intermediary may be used to verify transactions, but the transfer of assets is ultimately settled on a trustless, decentralized blockchain network.
Security Considerations
There are different types of attacks that can occur in blockchain bridges. Some of the most prominent ones are:
-
Custodian Attacks
Custodians are entities or mechanisms responsible for holding assets that are transferred across the bridge. Attacks can include:
- Key Compromise: If a custodian’s private keys are compromised, attackers can seize control of the assets.
- Malicious Custodian: A rogue custodian might collude to steal assets.
- Internal Fraud: Insiders within a custodial organization might execute fraudulent transactions.
-
Debt Issuer Attacks
Debt issuers are entities that mint tokens on the destination blockchain to represent the assets held by custodians. Attacks can include:
- Over-issuance: Issuing more tokens than the corresponding assets held in custody, leading to inflation and potential devaluation.
- Minting Vulnerabilities: Exploiting vulnerabilities in the smart contract responsible for minting tokens.
-
Communicator Attacks
Communicators are responsible for transferring messages or transaction details between blockchains. Attacks can include:
- Message Tampering: Altering messages during transmission to execute unauthorized transactions.
- Replay Attacks: Reusing valid data transmission messages to fraudulently initiate duplicate transactions.
- Denial of Service (DoS): Overloading the communicator with excessive traffic to disrupt operations.
-
Token Interface Attacks
Token interfaces are the smart contracts or systems that handle the wrapping and unwrapping of tokens. Attacks can include:
- Contract Exploits: Exploiting bugs in smart contracts to drain assets or mint tokens without proper backing.
- Reentrancy Attacks: Utilizing reentrancy bugs to repeatedly call the token interface and drain funds.
- Permission Mismanagement: Exploiting poorly managed permissions to gain unauthorized access.
-
Network Attacks
Network-level attacks target the underlying infrastructure supporting the bridge. Attacks can include:
- Sybil Attacks: Overwhelming the network with a large number of pseudonymous identities to disrupt consensus mechanisms.
- Eclipse Attacks: Isolating nodes from the rest of the network to control their view of the blockchain and manipulate transactions.
- Routing Attacks: Intercepting or manipulating the data packets during their transmission between nodes.
-
Front-end Attacks
Front-end attacks target the user interface and the interaction layer of the bridge. Attacks can include:
- Phishing: Creating fake interfaces to steal user credentials and private keys.
- Cross-Site Scripting (XSS): Injecting malicious scripts into the front end to execute unauthorized actions on behalf of users.
- Social Engineering: Tricking users into revealing sensitive information or performing actions that compromise their security.
To ensure the security of your blockchain bridges consider partnerships with security-focused blockchain consulting firms like Blockapex, you can significantly strengthen your bridge’s security posture and contribute to a safer and more resilient blockchain ecosystem.
Their increasing popularity has also made them a prime target for hackers. In just 2022, bridge hacks lead to more than $2Billion worth of losses.
Here are some of the top hacks and security concerns related to blockchain bridges:
- Wintermute Exploit: In August 2022, Wintermute, a cross-chain bridge, suffered a hack resulting in the theft of $100 million worth of cryptocurrency.
- Nomad Bridge Hack: In August 2022, the Nomad Bridge was hacked, resulting in the theft of $200 million worth of cryptocurrency.
- Ronin Bridge Hack: In March 2022, the Ronin Bridge was hacked, resulting in the theft of $540 million worth of cryptocurrency.
- PolyNetwork Hack: In August 2021, PolyNetwork, a cross-chain bridge, was hacked, resulting in the theft of $610 million worth of cryptocurrency.
- Wormhole Hack: In February 2022, Wormhole, a cross-chain bridge, was hacked, resulting in the theft of 120,000 wrapped Ethereum tokens worth $320 million.
Read More:
Advantages And Disadvantages Of Smart Contracts In Blockchain Technology
Top 10 Smart Contract Vulnerabilities List