Hundred Finance, a prominent entity in the decentralized finance (DeFi) space, facilitates borrowing and lending of cryptocurrencies. It emerged from the DeFi boom of 2020, allowing users to leverage their crypto assets to earn yield and borrow assets in a secure and efficient manner. The platform is built to function seamlessly in a multi-chain environment, highlighting its adaptability in the rapidly evolving crypto landscape. It first launched for testing on Ethereum’s Kovan testnet in mid-2021, and following successful trials, it was launched on the Ethereum mainnet.
Hack Impact
On April 15th, 2023, Hundred Finance was hacked, resulting in a loss of approximately $7.4 million USD in various cryptocurrencies. The attacker exploited an integer rounding vulnerability in the platform’s contract logic when a market was empty. The attack affected 180 individual wallets. In response to the hack, Hundred Finance paused markets, alerted the community, began tracking the hacker, and issued a $500k USD open bounty for information leading to the hacker’s arrest and the return of all funds.
Step 1: Using Flashloan
Firstly, the attacker took advantage of a feature called ‘Flashloan‘. Flashloans are unique to blockchain and allow a user to borrow a large amount of assets with zero upfront collateral, but with the caveat that they must return it within the same transaction. The attacker successfully initiated a flash loan to borrow 500 WBTC (Wrapped Bitcoin).
Step 2: Minting and Exploiting Empty Pool
Upon observing that the hWBTC lending pool was devoid of activity (no one was lending or borrowing), the attacker saw an opportunity. They deposited the borrowed WBTC into the empty hWBTC pool, ‘minting’ hWBTC tokens in the process.
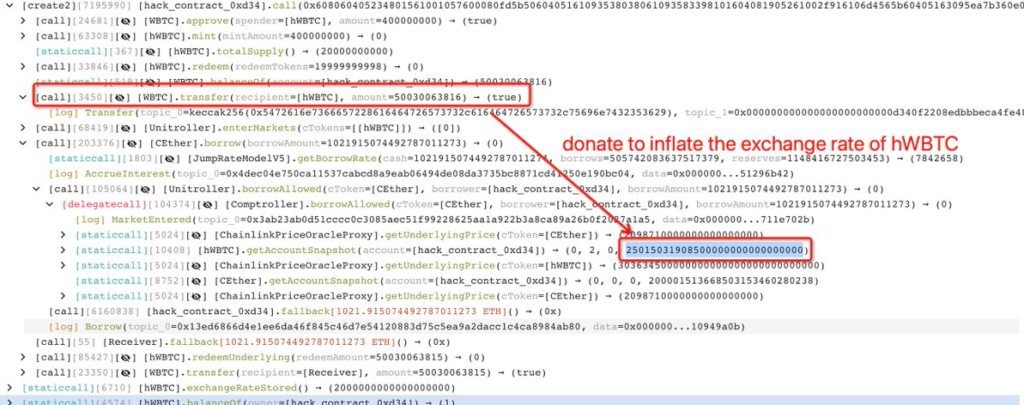
Step 3: Manipulating Exchange Rate
With the hWBTC tokens in hand, the attacker cleverly exploited the protocol’s exchange rate function. They deposited 4 WBTC into a custom-crafted smart contract and received an inflated amount of hWBTC tokens in return. Why? Because the exchange rate was abnormally high due to the fact that the hWBTC pool was previously empty.
Step 4: Inflating Collateral Value
Next, the attacker returned 500 WBTC to the original hWBTC pool, causing a dramatic surge in the value of hWBTC tokens. Since they were the only ones holding hWBTC, this effectively inflated their collateral value in the pool.
Step 5: Borrowing More Assets
The attacker capitalized on this artificial collateral value and borrowed 1021.91 ETH. This was a considerable sum of ETH, borrowed at a significantly lower cost than it should have been. The key to this step was the manipulation of the exchange rate and collateral value in the previous steps.
Step 6: Covering Tracks and Making Profit
Finally, the attacker repaid the initial flashloan with a tiny fraction of the borrowed ETH, keeping the majority of the assets. This was all done in a single transaction, thus satisfying the flashloan’s conditions and avoiding any trace of debt.
This clever yet malicious exploit hinges on a specific vulnerability in the redeemUnderlying function of the protocol’s smart contract. This function had an integer rounding error that presented itself when a market was empty, a condition the attacker used to their advantage.
Transaction Analysis
Exploiter’s Address: 0x155da45d374a286d383839b1ef27567a15e67528
This is the address used by the attacker to execute the exploit and receive the stolen WBTC and ETH. By examining the transaction history of this address, we can trace the steps taken by the attacker, including the preparation for the exploit and the subsequent token swaps.
Hack Transactions: 0x6e9ebcde… and 0x15096dc6…
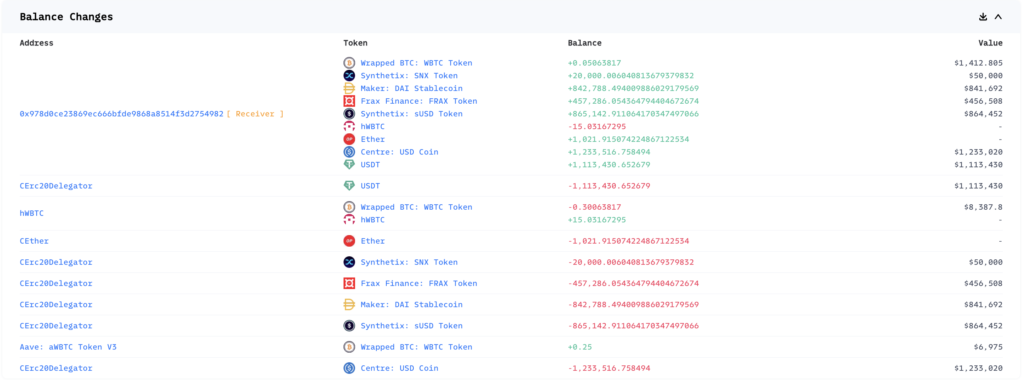
These transactions reveal how the attacker used to manipulate the exchange rate and redeem more tokens than initially deposited. The transactions expose that the attacker flashloaned 500 WBTC, donated large amounts of WBTC to manipulate the exchange rate and withdraw 1021.91 ETH and 500.3 WBTC.
Drained WBTC and ETH:
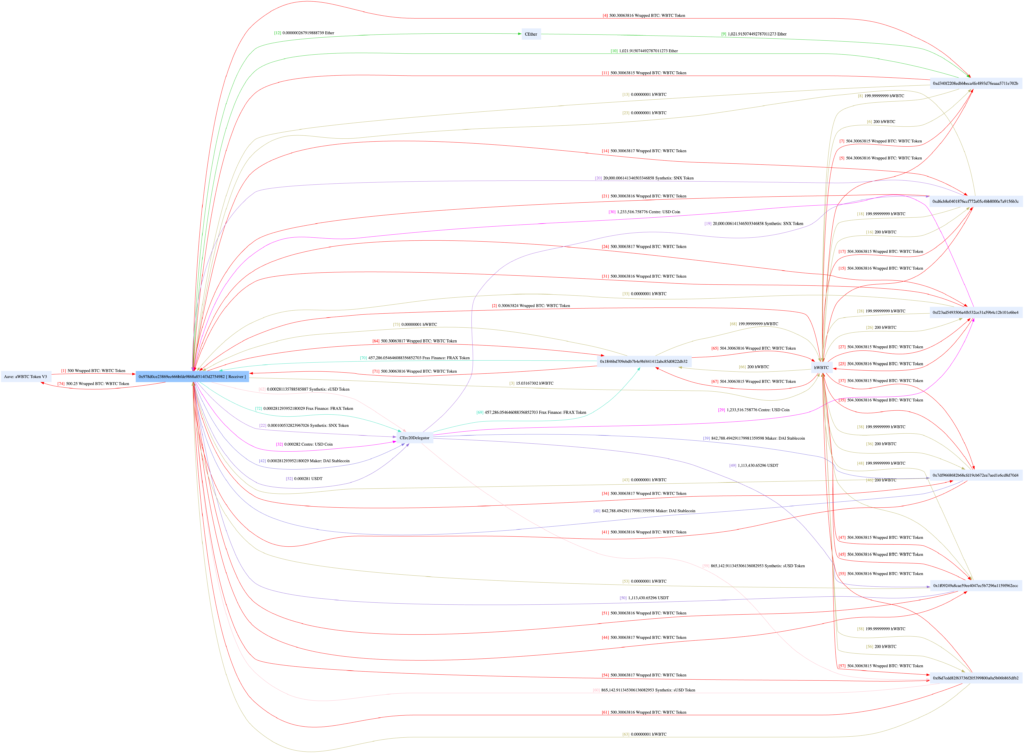
Following the successful exploit of Hundred Finance, the attacker drained 500.3 WBTC and 1021.91 ETH to their address. They then bridged most of the stolen funds to ETH where they were swapped for USDT and USDC, or deposited into Curve. The swap contributed to the temporary crash in the HND token price, which dropped around 50% following the exploit. At the time of writing, the hacker’s debank profile showed approximately $5.4M of assets on Ethereum and $0.9M remaining on Optimism.
Funds Flow
Conclusion
The exploit in Hundred Finance’s smart contract underscores the critical importance of robust security practices in the development and deployment of such contracts. Vulnerabilities can lead to significant losses and shake trust in the platform. By conducting rigorous testing, adopting secure coding practices, and enlisting the services of external auditing firms like BlockApex, developers can greatly enhance the security of their smart contracts, protect users’ funds, and maintain the integrity of their platforms.
Ultimately, security is not a one-time activity but an ongoing process of continuous improvement and adaptation to emerging threats. It’s crucial to stay informed about the latest developments in smart contract security and to update and improve security practices accordingly.
Also read,