Rari capital got hacked for around $79M through a classic re-entrancy attack. Rari is a fork of compound finance that had this bug fixed earlier. It is not the first time Rari capital has been a victim of a hack.
Pre-requisite
- Rari is a fork of compound finance & compound had a known issue of re-entrancy attack whenever CTokens were borrowed through borrow() function.
- This was patched by the Rari team by introducing a pool-wide re-entrancy guard on CTokens.
- There also exists a component called “comptroller” which is responsible for functions such as providing & withdrawing collateral by calling enterMarkets() & exitMarket respectively.
- The comptroller contract did not have re-entrancy checks in place. The attacker exploited through the exitMarket() function which makes the deposited asset no longer a collateral meaning it can be withdrawn at any time.
The Exploit
The attacker created 2 contracts.
There were 7 pools that were affected due to this exploit (8,18,27,127,144,146,156)
- https://etherscan.io/tx/0xa185f63b82cbb199a435399cfd414b89ebab91485d5034cdf8861a5f958259a4
- https://etherscan.io/tx/0xadbe5cf9269a001d50990d0c29075b402bcc3a0b0f3258821881621b787b35c6
- https://etherscan.io/tx/0x0f75349606610313cb666277eeda612e72be624cae061d017e503056bbf4d8e0
- https://etherscan.io/tx/0x0742b138a78ad9bd5d0b55221d514637313bc64c40272ca98c8d0417a519e2e4
- https://etherscan.io/tx/0x254735c6c14e4d338b1cc5bca43aab6b0f395ae06085013b1b2527180d270a31
- https://etherscan.io/tx/0xab486012f21be741c9e674ffda227e30518e8a1e37a5f1d58d0b0d41f6e76530
- https://etherscan.io/tx/0x9e4d4f4ebb45d1e03813d834494045c1b6ea2adbde1b89fbe24349846c223779
We will be focusing on this specific transaction to understand the hack.
https://etherscan.io/tx/0xadbe5cf9269a001d50990d0c29075b402bcc3a0b0f3258821881621b787b35c6
- Attacker took flashloan of 50,000 WETH & 80,000 WSTETH from Balancer vault

- The attacker deposited 80,000 WSTETH collateral into fWSTETH-146 pool.
- After depositing, the attacker borrowed 2397 ETH from fWSTETH-146 pool without updating the borrower’s record.
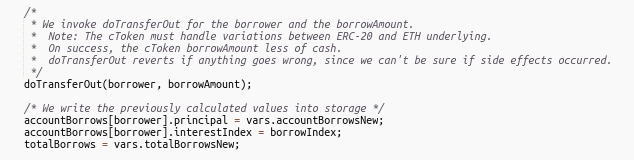
https://etherscan.io/address/0x49da42a1eca4ac6ca0c6943d9e5dc64e4641e0e3#code
- The pool triggers the fallback function of the exploiter contract while sending ether to the exploit contract where the attacker makes a re-entrant call to exitMarket() & withdraws his collateral of 80,000 WSTETH.
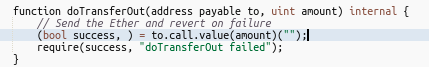
- The attacker receives 2397 ETH for free & transfers it to another contract for later claiming.
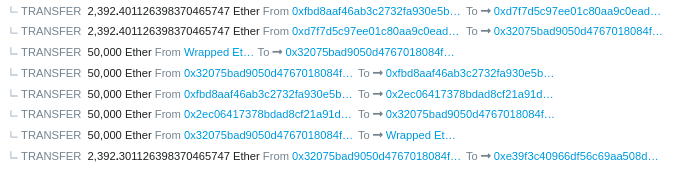
- The attacker repeats steps 1-4 until all borrowed amount is collected.
- The attacker applies the same strategy on 7 different pools & runs away with ~$79M of profit.
Hack Yourself!
Here is the Github repo that has POC for the hack.
Also, read
Harvest Finance Hack Analysis & POC.