Deus DAO, a platform offering a framework for optimistic on-chain digital derivatives, has experienced its third major hack across multiple chains, including Arbitrum, BSC, and Ethereum. The recent security breach resulted in token holders losing approximately $6.5 Million, and the DEI stablecoin depegging by over 80%. This event brings into question the trustworthiness of the thrice-hacked protocol, raising concerns for users and investors alike. Despite being a major player in the DeFi space, Deus DAO’s continuous security issues highlight the importance of robust smart contract audits and monitoring systems.
Hack Impact
The Deus DAO hack had significant financial consequences, with users collectively losing around $6.5 million across Arbitrum, BSC, and Ethereum chains. Furthermore, the hack caused the DEI stablecoin to depeg by more than 80%, destabilizing its value and potentially shaking investor confidence.
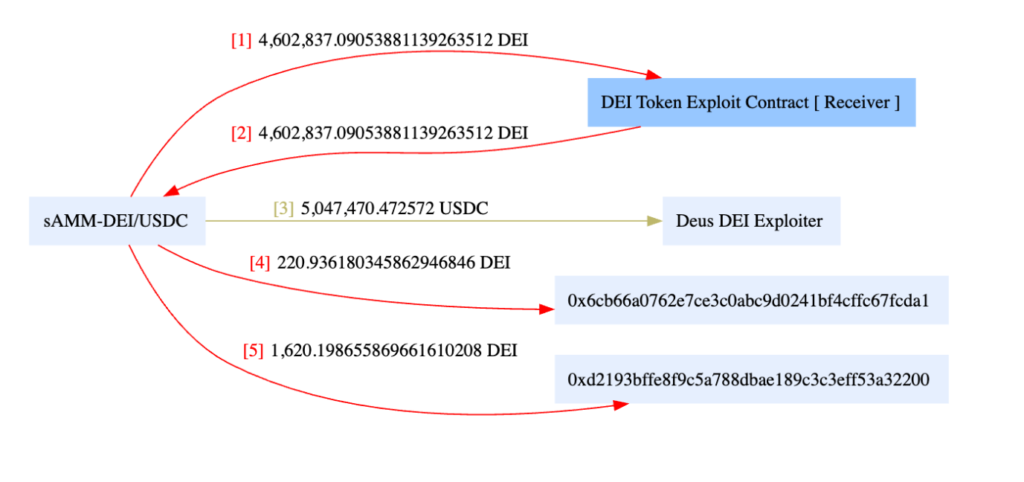
A simple implementation error in the DEI token contract, introduced during an upgrade last month, caused the vulnerability. This error allowed the attacker to manipulate DEI holders’ approvals and transfer assets directly to their own address. The losses were approximately $5 million on Arbitrum, $1.3 million on BSC, and $135k on Ethereum. Although some whitehat hackers have managed to return over $600k in USDC to a recovery multisig, doubts remain about the effectiveness of returning funds to a team responsible for such a trivial bug.
Deus DAO: Hack Explained
Approve Function
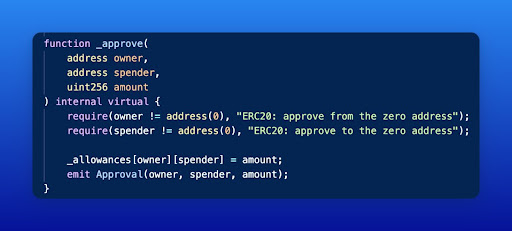
In ERC20 token contracts, the approve() function allows one account (the spender) to spend a certain amount of tokens on behalf of another account (the owner), and uses the mapping _allowances[owner][spender] to store the approved amount of tokens for a specific owner-spender pair.
Imagine the approve() function as allowing someone to take a certain amount of candies from your candy jar.
BurnFrom Function and Flipped Mapping Order Vulnerability
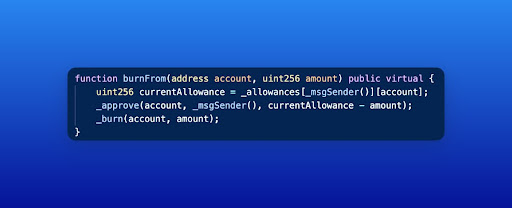
The burnFrom() function is responsible for burning a specified amount of tokens from a given account. In this case, the function reads the allowances mapping to ensure that the spender has enough allowance to burn the tokens from the owner’s account. However, there is a critical issue within the burnFrom() function.
The order of the mapping parameters has been flipped, causing it to read from _allowances[attacker][victim] instead of _allowances[owner][spender]. This flipped mapping order allows the attacker to manipulate the allowances and eventually gain control of the victim’s tokens.
Attacker’s Step-by-Step Process
Identifying a target
The attacker first identifies a victim account with a large amount of DEI tokens.
Approving the victim
The attacker approves the victim’s account for a large amount of tokens using the approve() function. This is like giving someone permission to take a large amount of candies from your candy jar.
Exploiting the BurnFrom function
The attacker calls the burnFrom() function with the victim’s address as the account and 0 as the amount. The flipped mapping order causes the allowances to get updated incorrectly, as the smart contract reads _allowances[_msgSender()][account] instead of _allowances[account][_msgSender()]. Due to this, the contract believes that the attacker has control over the victim’s withdrawal limit (allowance).
Resetting the allowance
Inside the burnFrom() function, the _approve() function is called again with the remaining allowance value (currentAllowance – amount). However, due to the flipped order, the allowance mapping is now set as _allowances[victim][attacker]. This means that the victim’s account has given the attacker an allowance to spend a large amount of tokens from their account, just like mistakenly giving someone permission to empty your entire candy jar.
Transferring tokens
Now that the attacker has been granted a large allowance from the victim’s account, they can call the transferFrom() function to transfer the victim’s tokens to their own account. The smart contract believes the attacker has the right to do so and allows the transfer, resulting in the theft of the victim’s funds.
Transaction Analysis
Attacker’s Addresses
Arbitrum: 0x189cf534de3097c08b6beaf6eb2b9179dab122d1
BSC: 0x5a647e376d3835b8f941c143af3eb3ddf286c474
Ethereum: 0x189cf534de3097c08b6beaf6eb2b9179dab122d1
The attacker used these addresses to execute the hack on different blockchains and receive the stolen DEI tokens. By examining the transaction history of these addresses, we can trace the steps taken by the attacker, including the preparation for the attack and the subsequent token transfers.
Attack Transactions
Arbitrum: 0xb1141785…
BSC: 0xde2c8718…
Ethereum: 0x6129dd42…
These transactions showcase how the attacker exploited the vulnerability in the DEUS DAO smart contract to steal DEI tokens. By analyzing these transactions, we can observe how the attacker manipulated the approve() and burnFrom() functions.
Funds Flow
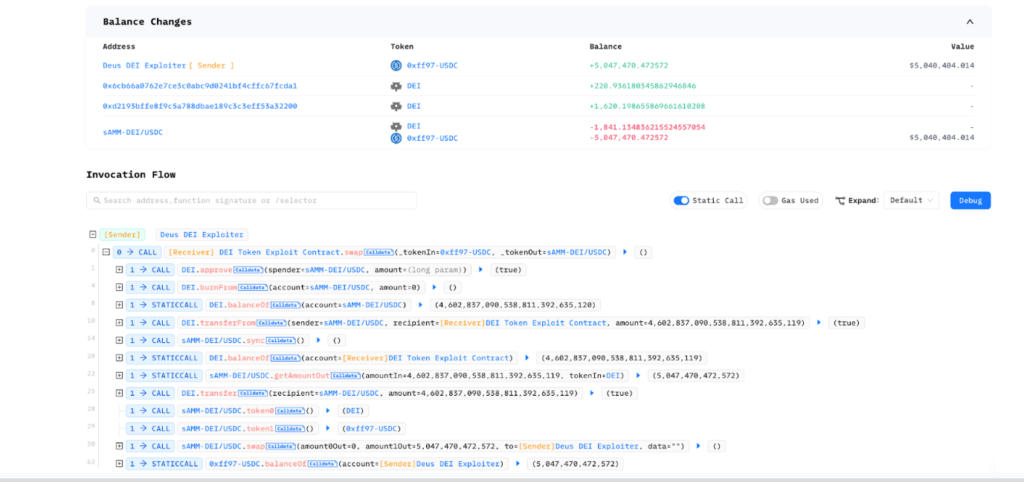
Conclusion
The DEUS DAO hack highlights the importance of thorough security measures when developing and deploying smart contracts in the decentralized finance ecosystem. This particular exploit was a result of a simple yet critical vulnerability in the burnFrom() functions, which enabled the attacker to manipulate allowances and steal millions of dollars worth of DEI tokens from unsuspecting users.
As DeFi platforms continue to grow in popularity, it is crucial for developers and project teams to prioritize the security of their smart contracts and to learn from incidents like the DEUS DAO hack. Implementing strong technical mitigations, conducting comprehensive audits, and engaging the community can significantly reduce the risk of security breaches and ensure a safer environment for users.
In light of this incident, we strongly recommend that projects have their smart contracts audited by reputable security firms like BlockApex.io. Conducting a thorough audit with experienced professionals can identify and address vulnerabilities before malicious actors can exploit them, ultimately protecting the integrity of the platform and the assets of its users.
By taking these important steps, DeFi platforms can continue to innovate and thrive while ensuring the security and trust of their users.
Also, read
Curve Finance Hacked, $570k Stolen!
Cream Finance Hack: What Motivates Hackers To Return Stolen Funds?