The term “flash loan attacks” has likely flashed across your screen at least once by now, as these attacks have become increasingly notorious. A flash loan attack can drain millions of dollars from decentralized vaults in a single transaction, drawing heightened attention from players in the Decentralized Finance (DeFi) space.
As the name suggests, flash loans are instantaneous, occurring entirely within an atomic transaction that ensures all actions—borrowing, manipulating, and repaying—must either succeed as a whole or fail without any changes to the state of the blockchain.
In this article, we’ll break down what flash loans are, delve into how flash loan attacks work, explore related case studies, and finally, examine the associated risks and methods of prevention.
What Are Flash Loans?
A flash loan is a type of uncollateralized loan offered by some DeFi platforms. Unlike traditional loans, flash loans are executed and repaid within a single blockchain transaction, eliminating the need for collateral. If the loan is not repaid by the end of the transaction, the blockchain reverses the entire process, ensuring the lender does not lose any funds.
Flash loans can be used for legitimate purposes such as arbitrage trading, which is profiting from price differences between exchanges, but they are also often exploited for malicious purposes, as seen in flash loan attacks.
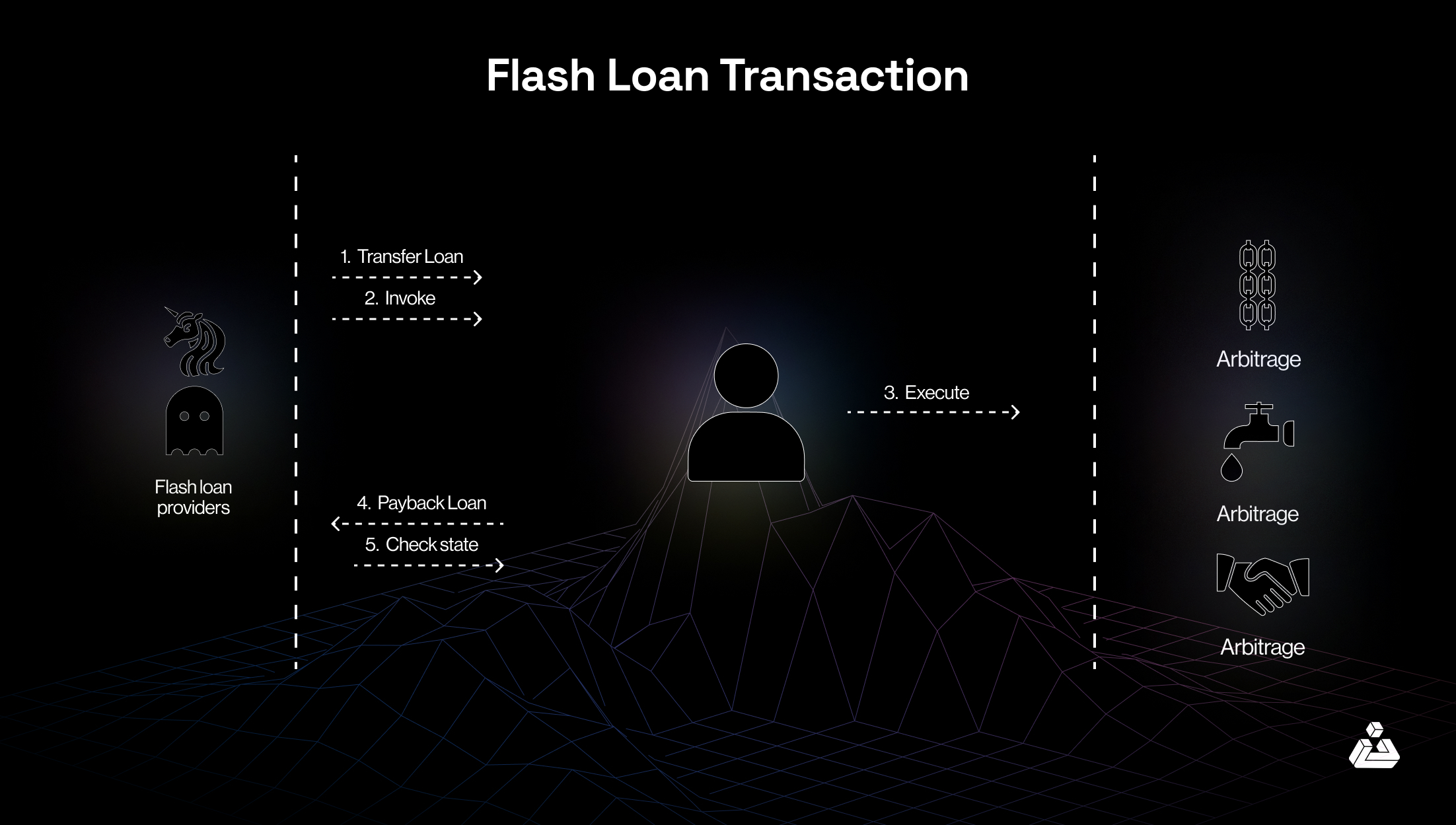
Let us walk you through the flash loan transaction process featuring Alice.
-
Request a Flash loan
Alice visits the DeFi lending platform, Aave, and requests a flash loan of 1,000 ETH. No collateral is needed since the loan will be repaid within the same transaction.
-
Execute Arbitrage or Smart Contract Manipulation
With the borrowed ETH, Alice buys a cryptocurrency that is undervalued on one decentralized exchange (DEX) and sells it on another DEX where the price is higher, making a quick profit due to the price discrepancy.
-
Repays the loan
Before the transaction is finalized, Alice repays the 1000 ETH plus any fees back to the lending platform.
-
Keeps the profit
Alice pockets the profit she made from the arbitrage trade after repaying the loan, all within a single transaction block.
How Does a Flash Loan Attack Work?
In the above scenario, Alice uses flash loans legitimately, but if she had exploited a smart contract vulnerability or manipulated market price, it would be considered a flash loan attack.
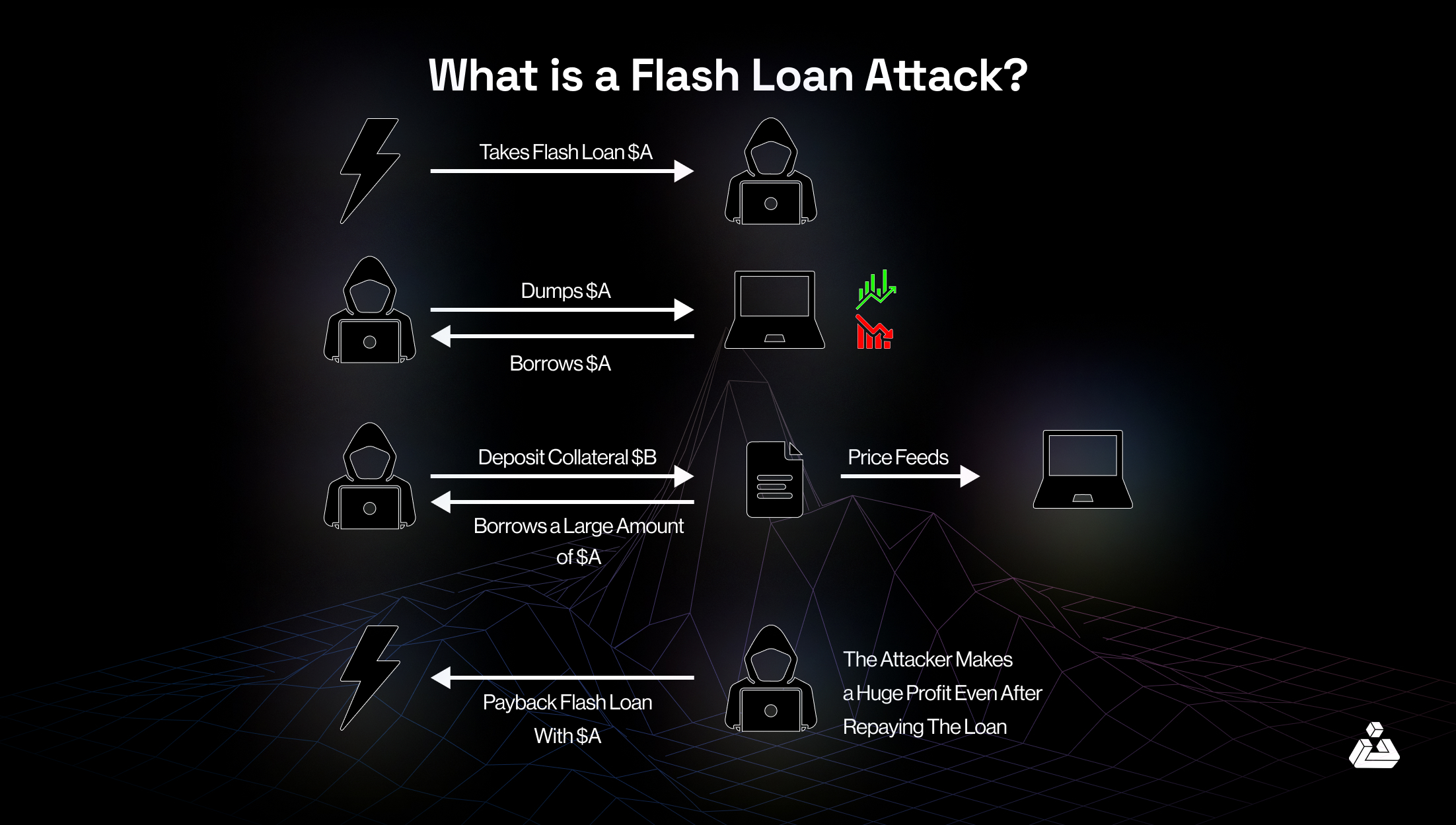
Let’s see how this attack takes place and assume that Bob is the bad guy here. So, he uses this three-step process which allows him to exploit the DeFi system without risking any collateral, highlighting the vulnerabilities inherent in flash loans.
-
Borrowing
Bob takes out a flash loan from a DeFi platform like Aave, borrowing a large sum of money, 10,000 ETH without any collateral.
-
Manipulating
Using the borrowed ETH, Bob executes a large trade that temporarily inflates the price of a target cryptocurrency. Let’s say he manipulates the price of Token X from $1 to $2 by creating artificial demand through his large purchase.
- Buys: Bob purchases 10,000 Token X for 10,000 ETH (at $1 each).
- Sells: After the price increase, he sells 10,000 Token X for 20,000 ETH (at $2 each).
-
Repaying
Bob repays the flash loans within the same transaction block, returning 10,000 ETH along with fees, of around 10 ETH. He profits from the price difference caused by this manipulation
- Total Earnings: 20,000 ETH from selling.
- Total Paid Back: 10,010 ETH (loan + fees).
- Profit: 20,000 ETH – 10,010 ETH = 9,990 ETH profit.
Below are the reasons why flash loan attacks are malicious:
-
Stealing Funds
Attackers can withdraw large sums from protocols, effectively stealing assets.
-
Market Manipulation
They create unfair trading conditions by artificially affecting cryptocurrency prices, leading to user losses.
-
Exploiting Vulnerabilities
Attackers take advantage of weaknesses in smart contracts, causing significant financial damage.
-
Undermining Trust
These attacks erode user trust in DeFi platforms, discouraging participation and destabilizing markets.
Case Studies of Flash Loan Attacks
Flash loan attacks are most common in the DeFi world.
-
Yield Protocol Attack (December 2023)
Vulnerability Explanation: Yield Protocol was targeted despite shutting down in December 2023 due to regulatory pressures and market demand. A vulnerability was discovered in the smart contracts on the Arbitrum blockchain. This weakness allowed the hacker to exploit the pool token balance and total supply, making it possible to withdraw extra tokens using flash loans.
Attack Explanation: The attacker utilized flash-loaned assets to manipulate the token balances and withdraw funds. By creating a situation where the pool balance and total supply were disrupted, they were able to siphon off funds from the protocol, causing a total loss of over $181,000. Although Yield Protocol had warned users to exit their positions before closing, some funds were still left vulnerable.
Conclusion: While Yield Protocol had ceased operations, the remaining funds were stolen due to a flaw in the smart contracts, and it’s unclear whether the funds will be recovered.
-
Euler Protocol Attack (March 2023)
Vulnerability Explanation: Euler Finance users borrow and lend using two token types: eTokens (collateral) and dTokens (debt). A hacker exploited a flaw in the eToken function, leading to incorrect conversions of borrowed assets into collateral. They used two entities—a front-running bot and a personal wallet—with initial funding from Tornado Cash for gas fees and contract creation.
Attack Explanation: The hacker took a $30 million DAI flash loan from Aave, deposited $20 million into Euler to get eDAI tokens, and borrowed 10 times the deposited amount. They used $10 million to partially repay the debt and continued manipulating the platform until the flash loan was closed.
Conclusion: Euler lost around $197 million in DAI, wBTC, stETH, and USDC. Its native token, EUL, dropped over 45%.
Read More: Euler Finance Hack Analysis
-
CREAM Finance Attack (October 2021)
Vulnerability Explanation: CREAM Finance’s yUSDVault had a significant flaw related to how token values were calculated, specifically allowing the attacker to double the perceived value of vault shares (crYUSD).
Attack Explanation: The attacker took out flash loans from MakerDAO and Aave, deposited DAI and ETH into Curve’s yPool, and minted crYUSD tokens. By manipulating the yUSDVault’s token supply and inflating their value, the attacker was able to increase the vault’s perceived value dramatically. They redeemed yUSDVault tokens to manipulate the vault’s valuation further, eventually draining $130 million from the platform.
Conclusion: The attacker managed to manipulate the value of yUSDVault tokens by reducing the total supply and depositing enough funds to double the perceived value. This allowed them to walk away with $130 million in assets from CREAM Finance.
Read More: Cream Finance Hack Analysis
Risks Associated with Flash Loan Attacks
Flash loan attacks pose significant risks to the crypto and DeFi space. Investors often lose money when attackers manipulate token prices and sell off assets quickly, driving market prices down. Vulnerabilities in smart contracts such as flaws in token balance mechanisms or price oracles, can be easily exploited, leading to system collapses or severe damage.
In some cases, these attacks also expose sensitive user data, further compounding the risks for DeFi users. Beyond direct financial impacts, flash loan attacks undermine confidence in the crypto space, leading to decreased investments and slowing overall industry growth.
Repeated incidents contribute to market manipulation, creating volatility that harms regular investors. These attacks not only hurt individual participants but also pose a long-term threat to the growth and stability of the entire DeFi ecosystem.
Prevention of Flash Loan Attacks
-
Use Decentralized Oracles for price data
Instead of relying on a single DEX for price feeds, DeFi platforms should opt for decentralized oracles like Chainlink and Band Protocol. Alpha Homora learned this after a flash loan attack and launched their Alpha Oracle Aggregator to improve security.
-
Force Critical transactions to span two blocks
Dragonfly research suggests requiring flash loan transactions to be processed over two blocks instead of one, reducing the chance of single-block attacks. However if not designed well, attackers could still exploit both blocks and this method could affect user experience, as transactions would not be instant anymore.
-
Monitoring systems with flash loan attack detection tools
Delays in identifying exploits can let attacks escape. OpenZeppelin’s Defender tool allows DeFi projects to monitor unusual activity in real-time, giving teams like Synthetix, Yearn, and Opyn to neutralize attacks more quickly.
Conclusion
Flash loan attacks pose a serious and constant threat to platforms and investors alike, undermining the security and trust within decentralized finance. However, implementing vigilant monitoring systems, decentralized price oracles, and best practices can help minimize the risk.
As the DeFi space continues to grow, we at BlockApex believe that taking proactive steps, combined with continuous improvements in security protocols, will be critical in safeguarding the ecosystem from such malicious exploits.
Protect your project from flash loan attacks with a smart contract auditing service. Mitigate weaknesses in your smart contract and improve its functionality with double line-to-line code analysis and a separate review by a lead auditor.































