Tldr: EigenLayer is a generalized middleware protocol built on top of ethereum that introduces a new yet significant primitive called restaking. This primitive allows users that stake ETH on consensus layer to restake their ETH on Eigenlayer and extend crypto economic security for the protocols built on EigenLayer. Therefore, one could say that by restaking on the EigenLayer the crypto economics can be aggregated and leveraged.
What is an Eigen Layer? A Brief Introduction
As defined by the founder of EigenLayer, it is a new crypto-economic primitive in the blockchain world which has leveraged the concept of restaking. At the ground level, this is a middleware that consists of smart contracts deployed on the base of the Ethereum chain that enables ETH stakers to restake their ETH. This means that the L2 protocols can rent the security of ethereum by integrating the EigenLayer. Thus, they can avoid the huge cost and complexity of running their own validator set.
In essence, the EigenLayer is a middle point where ethereum stakers can validate the new software models within the Ethereum ecosystem.
Until now, the ethereum security has been extended to smart contract protocols only. Inherently, it was very difficult to anchor this security to distributed systems like sequencers, bridges, and data availability layers. To do that, the developer must go through the cumbersome process of bootstrapping their trust network to get any security. Arguably, this was the most mundane obstacle for every small innovation in distributed systems. However, the EigenLayer has come to the rescue for all developers to fulfill the promise of decentralized economic trust.
The EigenLayer aims to provide three fundamental trust assumptions that developers can use by paying a small fee to build their base distributed systems.
- Decentralized Trust: Borrowing the trust from decentralized and isolated network operators.
- Economic Trust: Lending the trust from individual stakers making commitments by providing financial stake.
- Ethereum Inclusion Trust: The trust of the L2s blocks being included fairly as per the rules defined by ethereum consensus they are running.
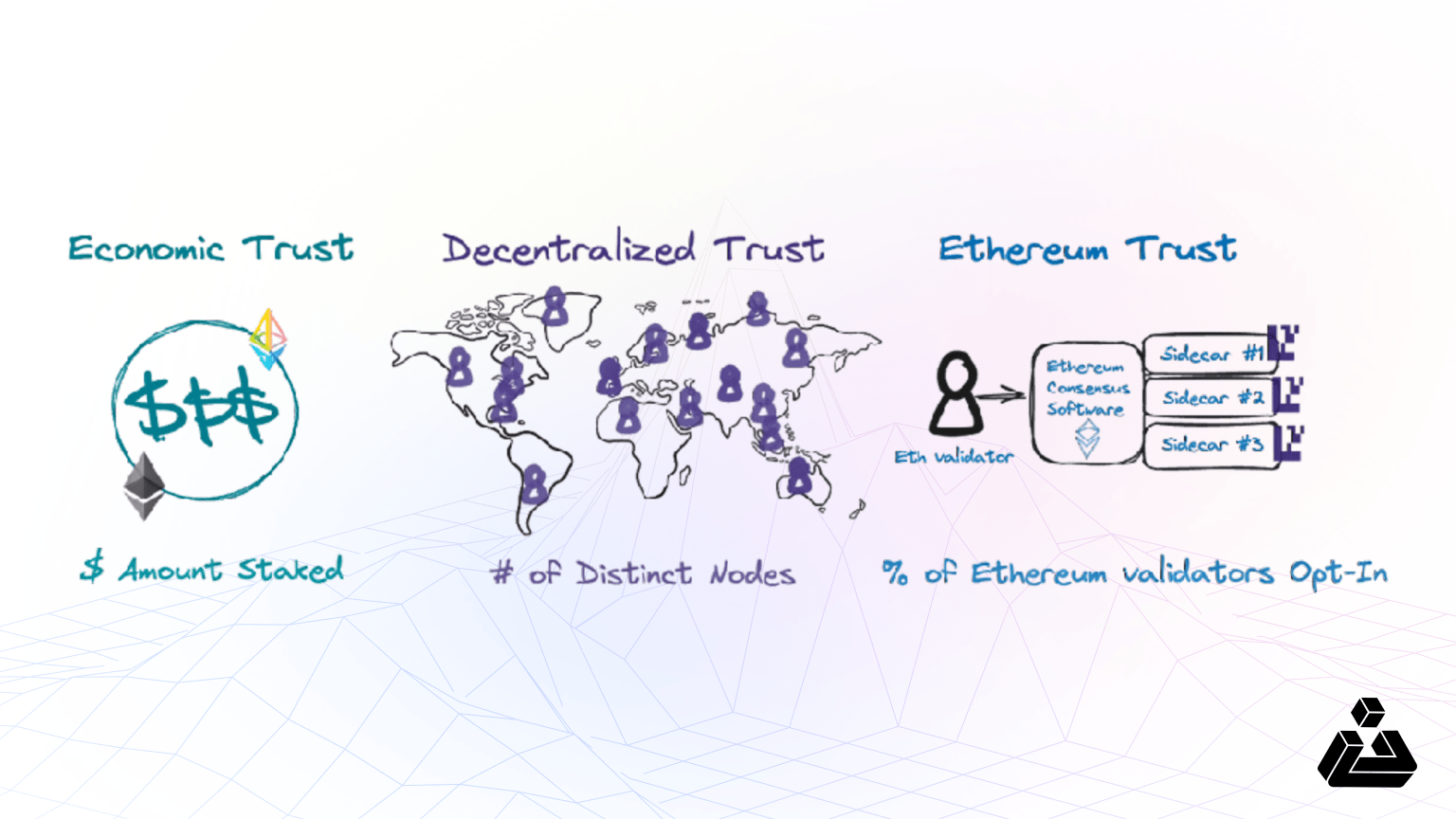
Source: https://www.blog.eigenlayer.xyz/the-three-dimensions-of-programmable-trust/
Restaking in Eigen Layer
The restakers in EigenLayer are ethereum stakers who are committed to following the ethereum rules to validate its chain. The EigenLayer expands this scope for restakers, where they can run extra node software to validate oracle networks and other distributed system applications. They pledge their staked ETH or ETH liquid staking tokens (LSTs) to the ecosystem and in return, receive the rewards for their commitment. These use cases are usually called Actively Validated Services. Among many, the first of them in the testnet stage is EigenDA. This AVS is a decentralized data availability layer designed to enhance Ethereum’s network scalability and efficiency.
The stakers also help in empowering the latency of ethereum using the EigenLayer. To explain this, let’s consider the example of Ethereum’s clock speed, which is limited to 2 epochs per 12 mins finality period. So if a primitive on EigenLayer requires a high finality period then if enough stakes are present on the EigenLayer, the clock speed of native network can be increased. This superfast finality chain verifies ZK proofs and arrives at consensus within seconds. In terms of economic trust, if an operator deviates maliciously from the intended behavior then an observer can create an objective on-chain proof to slash the malicious validator.
Eigen Layer Slashing Conditions
Optimistic Claims
If the value staked on an EigenLayer is high for a particular objective claim then those claims can be treated as a correct claim and later can be slashed if proved wrong. One example of this is the light client bridges. If a staker runs a light client of many other chains off-chain and makes claims about the canonical fork of the other chain on Ethereum. The input is acted upon immediately without any latency and later slashed if wrong.
Arbitrary Slashing
EigenLayer extends the integrated protocol’s slashing conditions. For example, rollups are limited to fraud proofs for state execution by design. However, on an EigenLayer, if a staker double-signs, it would be considered a slashable violation, hence extending the top protocol security. Cool, right?

To thoroughly understand the programmable trust brought by the EigenLayer, you may refer to this article.
How to be a Restaker in Eigen Layer
Beacon Chain Stakers
Users who have staked ETH directly on the beacon chain can participate in the network via EigenPod. An EigenPod is a contract, deployed by each staker, that enables native restaking by configuring the beacon chain withdrawal credentials to the EigenPod addresses.
Liquid Stakers
Users who have the liquid staking on other platforms can stake their LST directly to the EigenLayer protocol. Liquid staking is generally a process which allows users to restake their LSTs and remain liquid by minting a wrapped token that encompasses both yield layers and the underlying asset.
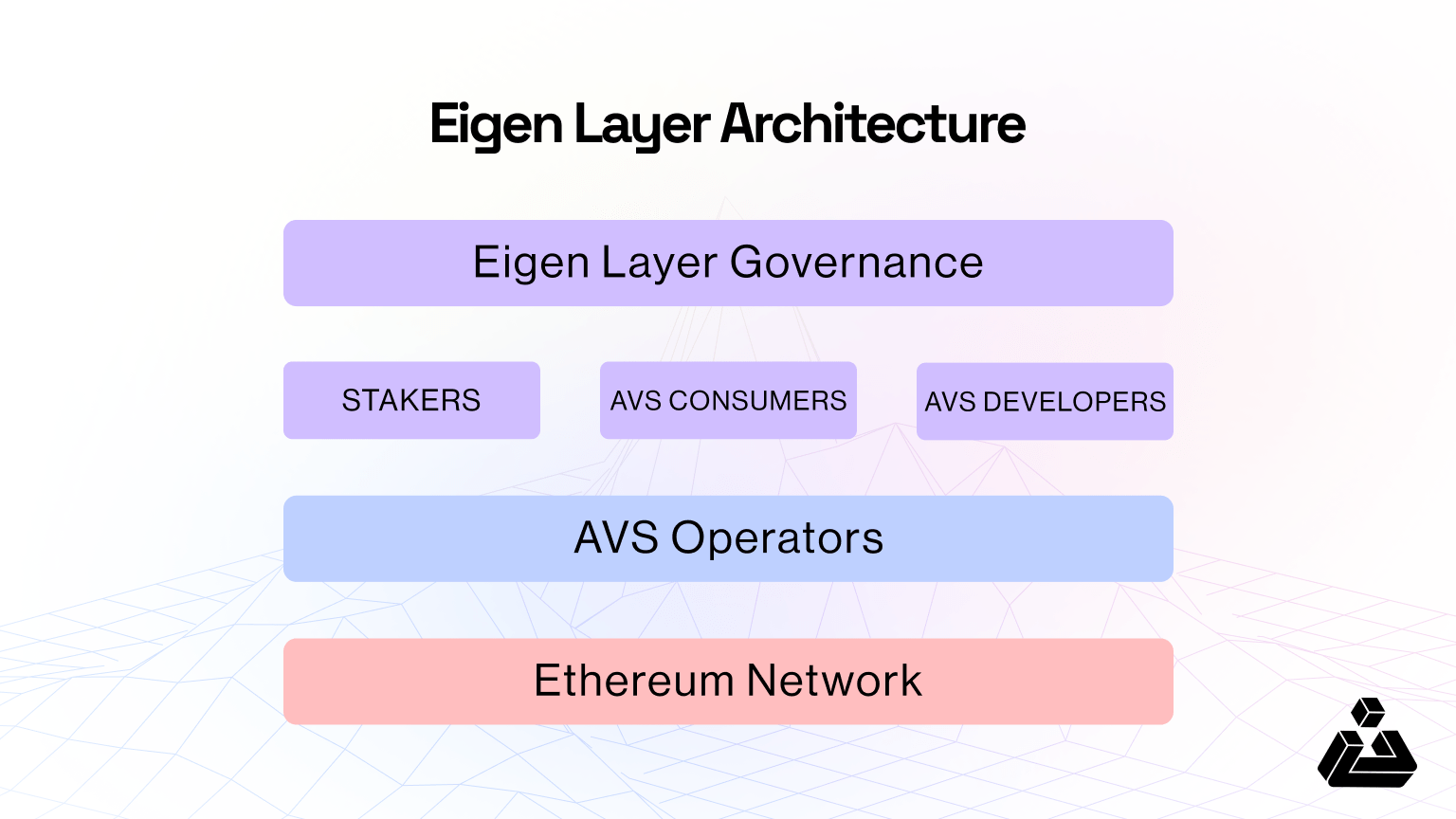
Apart from stakers there is another major role in securing the network called operators. These are an entity who helps run AVS software built on top of EigenLayer. They enroll in EigenLayer, enabling restakers to delegate their stakes to them, then opt in to provide various services (AVSs) built on top of EigenLayer. Operators may also be Stakers; these are not mutually exclusive. The restakers and operators both are responsible to validate transactions similar to ethereum validators.
Benefits of EigenLayer
EigenLayer is a novel concept which has redefined the paradigm of security, economic efficiency and performance. It has harnessed multiple domains in which few include.
Provider of Sovereignty
Protocols that want to inherit the security of ethereum have to adhere to the set of rules defined by ethereum and incorporate their rules accordingly. This limits the innovation and serves a lack of sovereignty for the protocols. This was the factor which has derived many developers to shift their focus from ethereum to other customizable chains such as cosmos. EigenLayer mitigates this problem and grants sovereignty to the protocols themselves.
Support Trust in Other protocols
Mostly the protocols depend on various other protocols for certain functions, with an example being oracles. However, these different functionality protocols might be built on chains other than Ethereum, which translates to a lower level of security. Hence, this poses a security risk to users because the protocol’s security is only as good as the security of the weakest component.
Liquidity Fragmentation
By utilizing the staking tokens, the EigenLayer solves the fragmentation problem and leverages the security of already-stacked tokens making the decentralized system more efficient.
Revenue for Stakers
With EigenLayer stakers could earn additional rewards by security of more networks without requiring to stake more tokens.
Risks and Considerations of EigenLayer
Yield Risks
In a few cases the EigenLayer stakers might look for the highest yield to maximize the profit. However, this may lead to protocols increasing the yield to attract the stakers, thus lower yield for protocol users.
Slashing
The biggest risk of the EigenLayer is the potential slashing of stakers on the consensus layer. This can impact the eth stakes on ethereum as well. So for example if a staker behaves maliciously all of his stakes will be slashed including the ones on ethereum.
Conclusion
EigenLayer presents an innovative approach to restaking. The designed architecture of EigenLayer will help multiple parties in the ethereum ecosystem, including developers working without limiting the base layer innovation. More importantly, we can predict that the blockchain landscape will become robust given the improved security and innovation that can be brought to the market. This will be a great driving force in attracting more users to come and participate in the ecosystem.
Read More:
How Can A VPN Protect You From Spying?
A Security Framework For Blockchain Applications
Web 2.0 Security Vs Web 3.0 Security: An Innovative Adaptation?































