Shezmu (SHEZMU) is a hybrid lending platform combining NFTs and yield-bearing tokens. It offers a Collateralized Debt Position (CDP) system, enabling users to use NFTs and yield-bearing tokens as collateral for loans, increasing asset liquidity. Shezmu also features a marketplace for “Guardians”—unique NFTs that can serve as collateral—and additional platforms, Agora for bonding and Oasis for DeFi services. Built on Ethereum, Shezmu benefits from secure, interoperable blockchain technology, with active community engagement through Twitter and GitHub. This multifaceted approach positions Shezmu as a distinctive player in the DeFi space.
Hack Impact
The Shezmu exploit on September 20, 2024, resulted in a significant financial loss due to a critical vulnerability in the protocol’s vault. The attack was facilitated by a flaw that allowed unrestricted minting of a collateral token, which could then be deposited to borrow ShezUSD. Using this vulnerability, the attacker was able to siphon approximately $4.9 million from the protocol. After negotiations, the attacker agreed to return the funds for a 20% bounty, resulting in the safe recovery of most stolen assets.
Shezmu Hack Explained
Step 1:Collateral Token’s Open Minting Functionality:
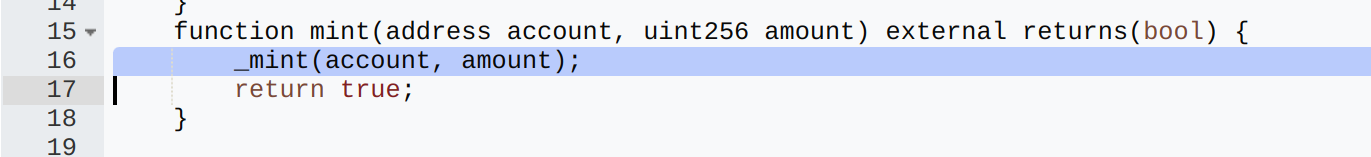
The collateral token contract (at address 0x641249db01d5c9a04d1a223765ffd15f95167924) included an open mint function, allowing any user to mint an arbitrary amount of tokens without restriction. This lack of access control meant that anyone could mint and accumulate large amounts of collateral.
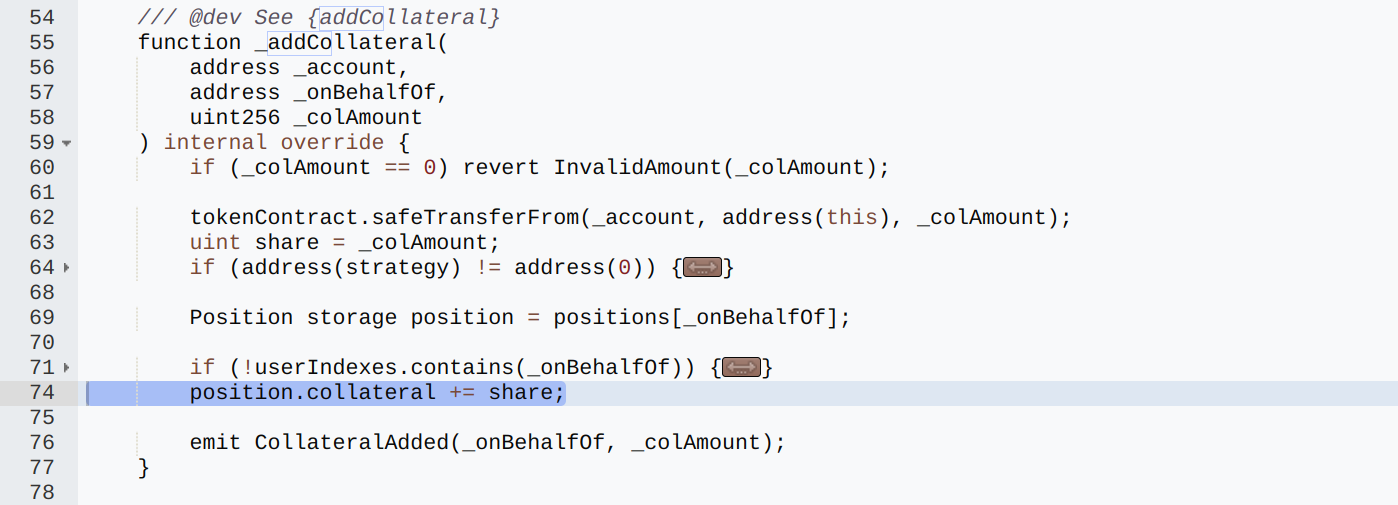
Step 2: Vault Acceptance of Collateral:
The Shezmu vault contract (0xa35f69899796ddbc4a8904511d2f1f040b779cb7) included an addCollateral function, which allowed users to deposit the minted collateral token into the vault. This function did not validate the origin of the minted collateral, thus allowing the attacker to deposit tokens they had minted themselves. This deposit increased their “shares” in the protocol, making them eligible to borrow ShezUSD against it.
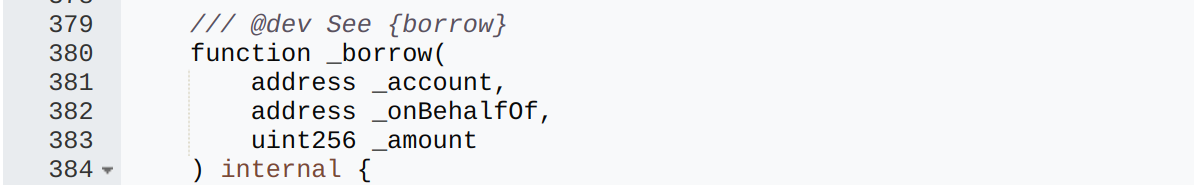
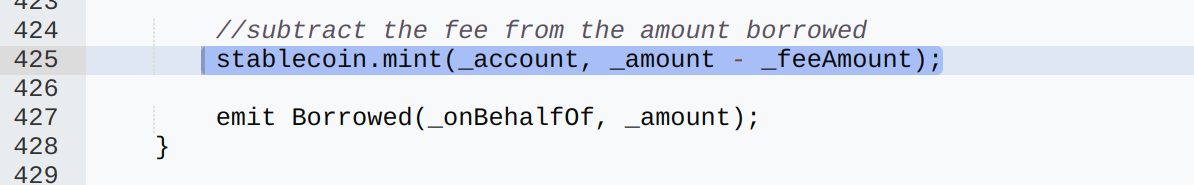
Step 3: Unrestricted Borrowing of ShezUSD:
The vault’s _borrow function allowed users to borrow ShezUSD against their collateral shares. Since the collateral token could be minted indefinitely, the attacker was able to deposit a large amount of self-minted collateral and, consequently, borrow ShezUSD in proportion to their deposited collateral shares. The vault had the authority (hasRole) to mint ShezUSD, which enabled the attacker to receive ShezUSD directly.
Simulate the Attack
To gain a deeper understanding of the Shezmu exploit, you can replicate the attack by following the proof of concept (PoC) available here. The PoC provides detailed, step-by-step instructions on how the vulnerability in the Shezmu Vault contract was exploited. By simulating the attack, you can observe the exploit process in action, providing valuable insights into how the attacker manipulated the vault and minted ShezUSD tokens, highlighting the exploit’s impact on the protocol.
Transaction Analysis
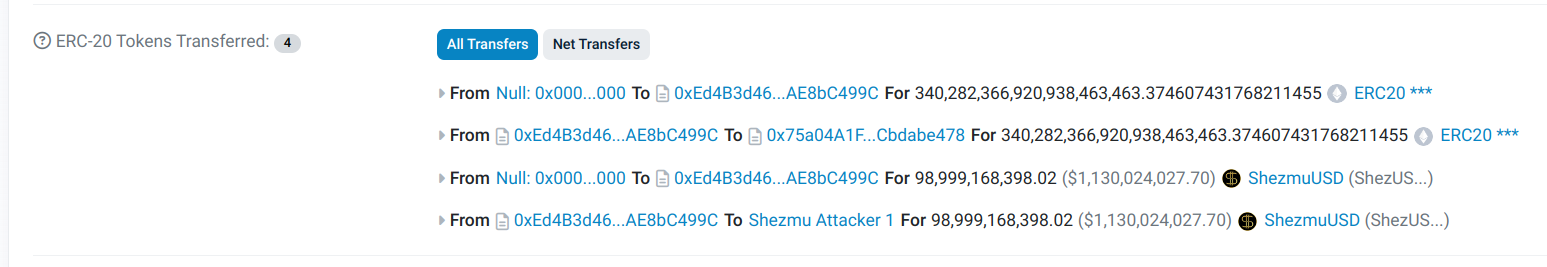
- Attacker Address: 0xA3a64255484aD65158AF0F9d96B5577F79901a1D
The individual responsible for initiating the exploit. This address is linked to the creation and execution of the attack. - Attack Contract Address: 0xEd4B3d468DEd53a322A8B8280B6f35aAE8bC499C
This contract, coded by the attacker, contained the logic necessary to exploit Shezmu’s system. It enabled the unauthorized minting and transfer of ShezUSD. - Minted Collateral Token: 0x641249db01d5c9a04d1a223765ffd15f95167924
The attacker first minted this collateral token, which was designed to be freely mintable by any address due to a flaw in the Shezmu protocol. - Collateral Vault Address: 0x75a04A1FeE9e6f26385ab1287B20ebdCbdabe478
Using the attack contract, the attacker then called the addCollateral function on this Shezmu vault address, assigning themselves collateral shares. - Borrow Function Execution:
Following the collateral addition, the attacker executed the borrow function on the Shezmu vault at the same address. This allowed them to mint a large amount of ShezUSD, which was directly sent to the attacker’s address. - Token Transfer to Attacker’s Address:
After minting ShezUSD, the attacker transferred these tokens to their primary address: 0xA3a64255484aD65158AF0F9d96B5577F79901a1D, consolidating the stolen funds. - Full Attack Transaction: 0x39328ea4377a8887d3f6ce91b2f4c6b19a851e2fc5163e2f83bbc2fc136d0c71
This single transaction encompasses the entire exploit sequence, from collateral minting to the final ShezUSD transfer to the attacker’s address.
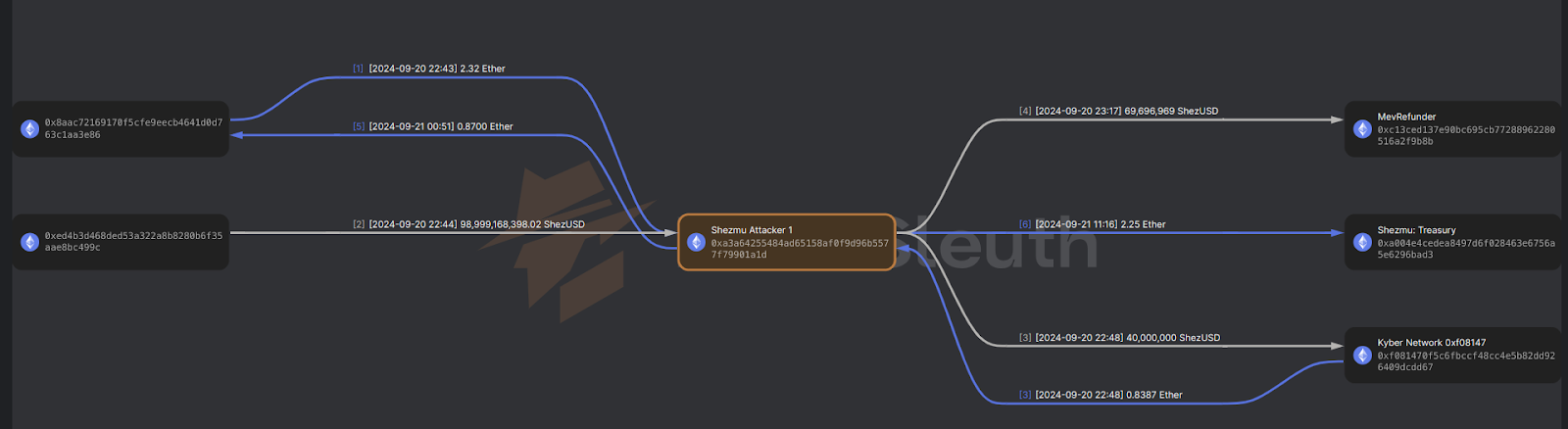
Funds Flow
The attacker minted 98,999,168,398.02 ShezUSD without collateral, transferring 69,696,969 ShezUSD to the MEV Refunder and 40,000,000 ShezUSD to Kyber Network. Ether conversions resulted in 0.8387 Ether routed through Kyber and 2.25 Ether sent to the Shezmu Treasury. By moving funds through various addresses and liquidity points, the attacker obscured the stolen ShezUSD and Ether trail. More details are available here.
Recommendations for Enhanced Security
-
Restrict Minting Access
- Implement strict access controls for collateral token minting. Only authorized entities should be allowed to mint tokens, preventing unauthorized users from generating tokens and accumulating excessive collateral.
-
Validate Collateral Origin
- Ensure the addCollateral function verifies the source of deposited tokens. Only accept collateral that is externally sourced and genuine, preventing users from depositing self-minted tokens.
-
Control ShezUSD Minting
- Add checks within the borrowing function to ensure that ShezUSD issuance is fully backed by validated collateral. This guarantees that only legitimate, collateral-backed tokens are issued.
-
Audit Key Functions
- Conduct regular security audits on minting and collateral-handling functions. These audits will help identify vulnerabilities early and prevent potential exploits.
Conclusion
The Shezmu Protocol hack highlights the critical need for rigorous security measures and thorough audits within DeFi platforms. While Shezmu was designed to offer innovative borrowing and collateral mechanisms, its vulnerabilities were exploited, resulting in a significant financial loss. This breach underscores the importance of robust access controls and validation checks to prevent unauthorized minting of tokens and ensure collateral integrity.
As the DeFi space continues to evolve, securing smart contracts and enforcing proper validation protocols must remain a priority. Implementing strict access controls, validating collateral sources, and conducting regular security audits are essential to safeguarding user assets and maintaining the integrity of the platform.
Organizations specializing in smart contract audits, such as BlockApex, play a pivotal role in identifying vulnerabilities before they can be exploited. The Shezmu Protocol hack serves as a crucial reminder of the need for ongoing vigilance, proactive security measures, and comprehensive audits to ensure the long-term security and success of decentralized financial systems.































