Safemoon is a decentralized finance (DeFi) project with over 2.5 million holders and more than $50 million locked in liquidity. It features a deflationary utility token, SAFEMOON, and has a fully diluted market capitalization of over $1 billion, according to CoinMarketCap. On March 28, 2023, Safemoon was hacked, and the attacker drained the SFM/BNB pool, resulting in a loss of $8.9M worth of ‘locked LP’.
Hack Impact
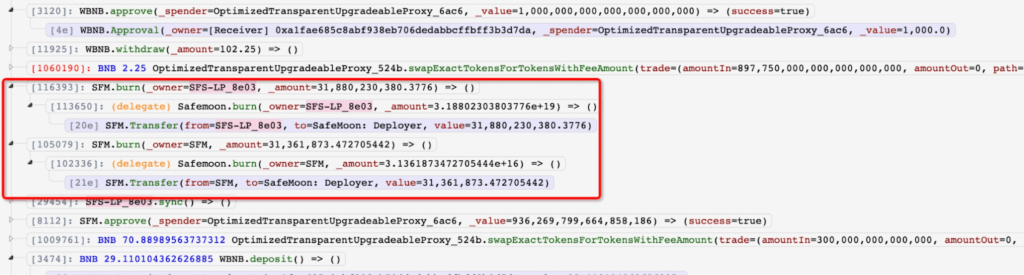
Safemoon suffered an attack in which the SFM/BNB pool was drained, resulting in a loss of $8.9M worth of ‘locked LP’. The attack was carried out by exploiting a vulnerability in the new Safemoon contract that allowed anyone to burn SFM tokens from any address, thus inflating the price of SFM tokens in the pool. The attacker was able to drain the pool of BNB liquidity by selling previously acquired SFM tokens into the artificially inflated pool, resulting in a profit of 28k BNB. The hacker has claimed to return the funds, but there are doubts about their trustworthiness.
Background
The vulnerability exploited in the Safemoon hack was introduced in the project’s latest upgrade, which took place approximately six hours before the attack. The upgrade included a new implementation of the token contract, which mistakenly left the burn function as publicly callable. The code for the function is as follows:
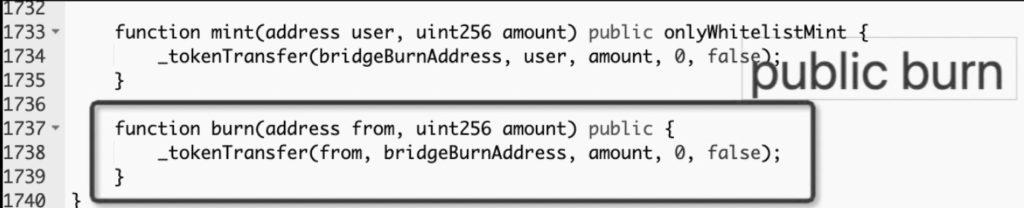
The function transfers the specified amount of SFM tokens from the specified address to the bridgeBurnAddress, effectively burning them. However, the mistake in the implementation made anyone call it and burn tokens from any address.
Steps to reproduce
- The attacker used the public burn function to burn SFM tokens,inflating the price of SFM tokens in the pool. The attacker then sold previously acquired SFM tokens into the skewed pool, causing it to lose BNB liquidity.
Transaction Analysis
The attacker exploited the burn function, and the majority of the funds were transferred to 0x237D where they remain at the time of writing. The exploit transaction can be traced using the transaction hash: 0x48e52a12…, and the attacker’s address is 0x286e09932b8d096cba3423d12965042736b8f850.
Conclusion
Safemoon’s hack serves as a reminder of the risks involved in deploying new features into the main net without proper security checks. Projects need to ensure that their smart contracts are secure and audited to prevent such exploits from happening. Security audits can be conducted by third-party audit firms such as Blockapex, which specializes in auditing smart contracts and DeFi protocols.
Also read :
Hack Analysis on DeFi Geek Community Japan
Cream Finance Hack: What Motivates Hackers To Return Stolen Funds?































