Social Media – an array of platforms that came to life to connect people from all around the world. People started connecting throughout the globe, developing mutual interest over the course of time. As the internet and the social media platform went through tailored stages, custom build functionalities broke through and gave every user a new paradigm to explore. The world witnessed how social media became a vital part of everyone’s daily routine. But as everything has a good perspective, a bad perspective does follow along. Social media, serving as the hub of globalization, brings with it diverse types of issues that extend beyond its confines to broader concerns known as cybersecurity issues. Among the most alarming and concerning of these are data breaches and consumer privacy.
Social Media & Data Breaches:
Over the preceding decades, the hype and usage of social media platforms have become a common tool for connectivity, business, sharing content, news, and information.
But the extraordinary use of social media has allowed it to look into its user’s lifestyles by tracking their behavior. Social networking companies’ livelihood is harvesting users’ buyer journey and their interest in different content pages/celebrities. The way they respond to a sponsored post or what type of content they are into such as a video post allure them more or a static post? Even their characteristics. All of these piles up to form a good amount of data which these companies use to manipulate people through their advertising and cause data breaches against consumer privacy.
About 45% of the world’s population, or roughly 3.48 billion people, use social media networks. Many connections can reveal vulnerabilities, causing severe damage if data is misused. Looking at the United States, unauthorized users hacked only 13% of American social media accounts in 2021.
Hacks often lead to malware and forced shares, tricking people into sharing their bank details or transferring money. Social media accounts hold vast personal information, attractive to third parties for personalized ads. Cyberattackers target this information, resulting in billion-dollar hacks annually.
Approaches Being Immensely Used For Data Breach:
With the dawn of the sun each day a new case comes to the limelight indicating that a new hack or breach is causing the loss of billions or even the lives of innocent people.
Let’s discuss some approaches that are quite common and have numerous examples, yet people still fall into the same traps and become another example. Let’s dive in!
Knowledge Discovery of Data:
Whenever someone enters the space of social media, he/she makes an account. To activate that account the user gives the platform personal information such as their birth date, geographical location, personal interests, and in some cases the contact details also. This information is stored on the network and used for data mining. Data mining is basically where the companies used to store data and custom campaigns according to the customer’s likes and preferences. Companies use this data for breaches and have reached the extent of selling it to third-party companies without the users’ consent. This action counts as a breach of consumer privacy.
Phishing Attacks:
A phishing attack is a method that is a common tactic that cybercriminals use. The attack lures people into providing personal and sensitive information. Often posing as a social media platform, the attacks are in the form of email or text messages. The attacker acts as a legitimate source and lets people fall into the trap.
Attackers share sensitive information, such as bank information, credit card details, passwords, etc.
In August of 2019, Instagram went through a phishing attack. The attackers send phishing emails to users, indicating that someone has just logged into their account from another device. The email includes a link to a copycat Instagram website controlled by the hackers, designed to save all the user’s login information. It also contains a code that the email claims will confirm the identity of the user.
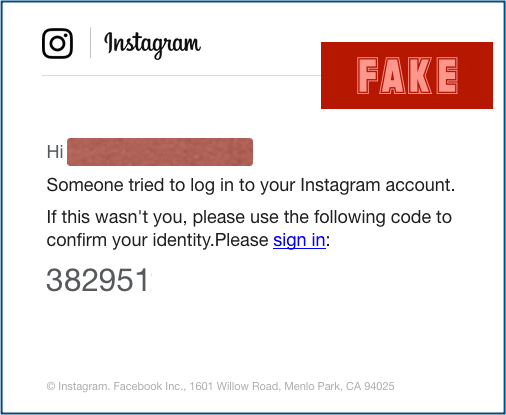
Since the website was fake the attackers used it.CF domain (the country code top-level domain for the central country republic). But a lot of the users can’t easily identify that.
Malware Sharing:
Designers of malicious software aim to penetrate the host’s system, thereby granting attackers easy access to the host’s data, including email, social media accounts, and various platforms connecting the host to the world. These kinds of attacks could also lead to worse consequences such as extorting money or bank account details, along with false advertisements through social media channels.
Social media channels are an easy delivery system for distributing malware among different people. Once the cyber attackers get access to the account the whole contact list of the host is mostly under the same attack. Resulting in another form of a consumer privacy breach.
The Curse Case Of Mia Ash:
On January 13, 2017, a purported London-based photographer named Mia Ash started a malware campaign. She targeted people from the Middle East and North Africa (MENA). LinkedIn was the platform she chose to target as it is considered to be used by professional people and establish connections for business purposes. Keeping that agenda in mind she started reaching out to people.
She reached people out in the name of a survey regarding her photography business. To make it real she shared a document that contained micro links having PupyRAT, an open-source cross-platform remote access trojan (RAT). Further analysis revealed a well-established collection of fake social media profiles that appear intended to build trust and rapport with potential victims. The connections associated with these profiles indicate the threat actor began using the persona to target organizations in April 2016.
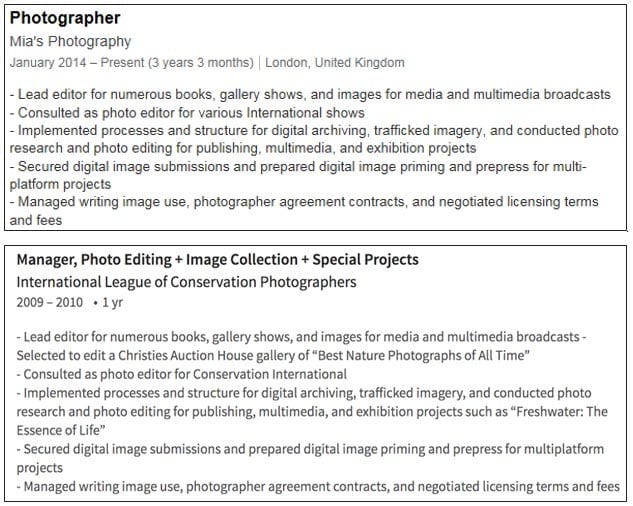
The above one is the job description Mia Ash was using to lure people into the attack whereas the second job description is originally used.
The Central Threat Unit (CTU) researchers observed these kinds of malware attacks beforehand and saved a lot of people from becoming a victim of them.
Botnet Attack:
Bots on social media are another common way for attackers to get access to the victim’s device. Bots on social media are automated accounts that create posts and also are automated to follow new people whenever a new term is mentioned. A large group of bots makes a botnet. These bots and botnets are a great source to steal data, send spam messages and also launch distribution of denial of service attacks (DDoS). These DDoS attacks help cybercriminals to hack the consumers’ devices and penetrate them resulting in access to their contacts and much more.
Consumers’ Privacy – A Global Issue?
The information stored on social media channels is vulnerable to attack, solely inducement being the network is not secure enough. Typically all the platforms existing on the internet have privacy policies that are disclaimed the purported as a waiver once users consent to them. But often these policies are hard to intercept, vaguely designed, and also difficult to impossible to implement. All the components add to make these policies pretty useless.
Data collection is an essential part of the social media advertising model. The users are shown customized and tailored ads. These ads are customized through the data the companies purchase as a third party.
A lot of incidents happened with social media giants which made people suspicious about their privacy. Countless incidents occurred, some of them as follows.
Facebook Fooled The Common Man:
To survive in the market and make the most out of social media platforms companies buy users’ data, completely banishing the consumer privacy protocols. That data is then used to attract customers on social media platforms according to their interests and likes.
Mark Zuckerberg – the founder and CEO of Facebook has unlimited times alleged for data breach cases. Facebook promised to protect the users’ data but failed to do so.
In 2014 Facebook announced that they are acquiring WhatsApp – a very strong social media network that people use to communicate with their loved ones, friends, and people who matter to them. One of the main reasons WhatsApp also is a top-rated app for users is because of its privacy policies i.e end-to-end encryption. In 2012, the founder of WhatsApp stated that “[w]e have not, we do not and we will not ever sell your personal information to anyone.”
On this, the EPIC urged that this merger should not be done. But later it was approved after both the companies promised that they would never breach their consumer privacy policy, it will remain intact. But in 2016 Facebook and WhatsApp came forward with some former changes completely denying their statements published at the time of the merger, the changes that included some features related to business, and also statements that proved that Facebook would acquire personal information of WhatsApp users.
On this, the European Union fined Facebook $122 billion for deliberately representing false information about the company’s ability to integrate the personal data of WhatsApp users.
The Verdict:
It is high time and vital for data security firms to be aligned with the government and lawsuits to take action against it. If giants like Facebook are using these kinds of tactics it would be impossible for smaller firms and companies to enter such a competitive market where supremacy and monopoly are with those who breached the consumer privacy protocols.
Yahoo Exposed by Reuters:
Yahoo – a multi-million dollar company faced probably the largest data breach in history. Over 500 million users’ information was exposed to the world.
But the story doesn’t end here; further investigation found that Yahoo was voluntarily scanning users’ emails and handing the data over to the NSA. Yahoo’s CEO, Marissa Mayer, not an IT professional, personally conducted this intrusive act.
In response to Reuter’s detailed exposé which explained the whole thing on 4th October 2016, Yahoo only issued this statement. “Yahoo is a law-abiding company, and complies with the laws of the United States.”
This defensive and unapologetic response from such a company only sparked a lot of criticism and shame for the company. Further Alfredo Lopez at Counterpunch explained that:
“They didn’t just review the emails, they built a special program to do it and never let their users know they were doing that. It might seem logical — after all, you don’t let the person who you’re spying on know you’re spying — but very few Yahoo users are the subject of investigations.”
This attitude and violation of consumer privacy laws brought light to the fact that even these kinds of firms are doing this. How can they even ask for trust in them?
Vizio Sees Us Through Their Smart TVs:
A very famous electronic brand Vizio still exists in the market which was once very popular as it sells Smart TVs and other devices for comparatively lower prices than Sony, Toshiba, etc. Although the quality was somewhat the same.
The twist in the story emerges when investigators discover that Vizio watches its customers through the smart TV and other devices as people use them. It also turns out that they also track the users’ buyer’s journey and share that with companies that serve out targeted ads.
Companies like Google also engage in similar activities, but the issue that made it a big deal with Vizio was the company’s failure to obtain consent from buyers to share their information. Combining these 2 causes made Vizio violate the Video Privacy Protection Act which states that, “Vizio knew that it was disclosing: 1) a user’s identity; 2) the identity of the video material; and 3) the connection between the two — that the given user had ‘requested or obtained’ the given video material.”
The question here arises would we ever be able to watch our smart TVs or other electronic devices the same way? Won’t we always have a fear or risk in mind that we are being watched and all our private information is being sent to a third party?
In a Nutshell:
As it’s the era of technology, every other person has access to each and everything. Due to this kind of availability some cybercriminals and firms take advantage of it. The increasing no. of users on social networks or even the internet is making them more powerful, due to data accumulation. This data in the name of better targeting their marketing efforts is sold. Selling and availability of data then open doors for cybercriminals to carry out unethical deeds and make millions out of it!