BonqDAO, a decentralized lending platform on the Polygon network, experienced a major security breach on February 2, 2023. It allows users to borrow by locking tokens in a Trove. This smart contract is user-controlled. Users can mint BEUR, a stablecoin pegged to the Euro.
The attack exploited a vulnerability in how BonqDAO integrates the Tellor Oracle system to obtain token price information. By manipulating the price of AllianceBlock’s WALBT tokens, the attacker managed to steal 100 million BEUR stablecoins and 120 million Wrapped AllianceBlock Tokens (WALBT). This article will provide an in-depth analysis of the hack. The article further details the impact it had on both the platform and its users.
Hack Impact
The hack had a profound impact on BonqDAO, the affected tokens, and the DeFi ecosystem at large. The attack affected the following key areas:
Direct Losses
The attacker was able to steal 100 million BEUR stablecoins and 120 million WALBT tokens. The stolen funds were converted into other cryptocurrencies and laundered through Tornado Cash. Tornado cash is a privacy tool for Ethereum transactions which makes it harder to trace and recover the stolen assets.
Token Price Drop
The news of the hack led to a significant decline in the value of the affected tokens. Bonq Euro (BEUR), a stablecoin pegged to the Euro, fell to an all-time low of $0.15 on February 3, which is a severe depreciation for any stablecoin. Additionally, the AllianceBlock Token (ALBT) experienced a major hit as collateral damage from the attack.
Understanding Tellor Oracle
Tellor is a decentralized Oracle protocol that provides an immutable, open, and permissionless network for data reporting and validation. It enables anyone to provide data and allows everyone to verify its accuracy. In the context of BonqDAO, Tellor is used as a price oracle to obtain token price information.
To become a reporter for the Tellor Oracle, a user needs to stake a certain amount of TRB tokens. Once the required stake is deposited, the user is eligible to report data using the submitValue function. However, it is important to note that if a user reports invalid or malicious data, their staked amount may be slashed as a penalty. This mechanism encourages accurate reporting and helps maintain the integrity of the data provided on the network.
The submitValue function, as seen in the code snippet below, is part of the TellorFlex contract:

This function allows the reporter to submit a value to the Tellor Oracle network. In summary, the Tellor Oracle allows anyone to become a reporter by staking a certain amount of TRB tokens. All they have to do is submit data using the submitValue function. This function ensures that only users with a sufficient stake can report data, and the slashing mechanism discourages the submission of invalid data, maintaining the integrity and accuracy of the data provided on the network
Breaking Down the Attack: Exploiting BonqDAO
Step 1: Staking on TellorFlex Oracle
The attacker began by staking 10 TRB (Tellor’s native tokens) on the TellorFlex oracle allowing them to become a reporter. This is a necessary step for anyone who wants to submit a new data point to the Tellor Oracle. The staking serves as collateral, meaning if the submitted data is found to be incorrect or malicious, the stake can be forfeited.
Step 2: Manipulating the price of WALBT tokens
The attacker submitted a false price for WALBT tokens, setting it at 5,000,000 USD. This is much higher than the actual price. The Tellor Oracle, which is used by BonqDAO to get price information, accepted this manipulated price.
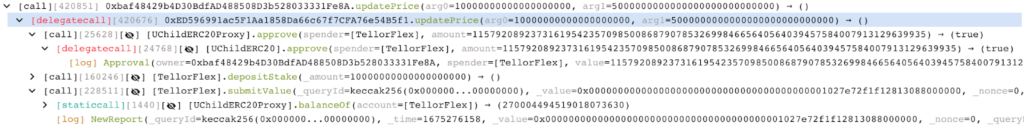
Step 3: Creating a Trove and borrowing BEUR tokens
With the manipulated price in place, the attacker created a Trove within the BonqDAO platform. A Trove is a smart contract that allows users to lock up their tokens as collateral and borrow other tokens against it. The attacker deposited a small amount of WALBT tokens (0.1 WALBT) into the Trove. Due to the inflated price, they were able to borrow $100 million worth of BEUR tokens, which are stablecoins pegged to the Euro.
Step 4: Converting BEUR tokens to other cryptocurrencies
The attacker then used Uniswap, a decentralized exchange, to swap the borrowed BEUR tokens for other cryptocurrencies like USDC, a stablecoin pegged to the US Dollar.
Step 5: Creating a second Trove and manipulate the price again
The attacker created a second Trove with WALBT tokens and deposited 13.2 WALBT tokens into it. Then, the attacker staked another 10 TRB on the TellorFlex Oracle. However, this time submitted a much lower price for WALBT tokens (0.0000001 USD).
Step 6: Liquidating Troves at a low token price
With the low WALBT token price in place, the attacker proceeded to liquidate multiple Troves of WALBT tokens. Liquidation in this context means repaying the borrowed BEUR tokens and getting the locked WALBT tokens back. Since the WALBT price was now extremely low, the attacker could repay the borrowed BEUR tokens with a minimal amount of WALBT tokens, effectively stealing a large amount of WALBT tokens in the process.
Step 7: Moving the stolen funds
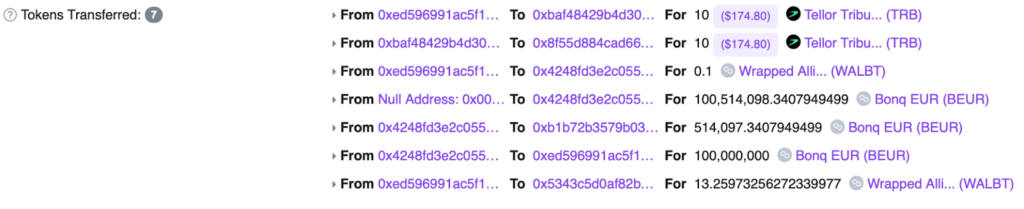
After successfully stealing 113.8 million WALBT tokens and 98 million BEUR tokens. The attacker began moving the funds out through Tornado Cash, a privacy tool for Ethereum transactions. This allowed them to launder the stolen funds and make it harder to trace.
The attacker exploited the vulnerability in the integration of the Tellor Oracle systemhis allowed them to manipulate the price and ultimately steal a large amount of tokens.
Mitigation Strategies and the Dangers of Instant Price Usage
To prevent similar vulnerabilities from being exploited in the future, several mitigation strategies can be implemented to secure the price oracle integration within DeFi platforms like BonqDAO.
Use Time-Weighted Average Price (TWAP)
Instead of relying on instant prices, DeFi platforms should use the Time-Weighted Average Price (TWAP) over a predetermined period. This approach minimizes the risk of price manipulation. How? by averaging out the price fluctuations and provides a more accurate representation of the token’s value.
Multiple Price Oracle Sources
Integrating multiple price oracle sources can help minimize the impact of a single oracle failure or manipulation. By aggregating data from different sources, the platform can cross-verify the accuracy of the price data and ensure a more reliable feed.
Monitor for Suspicious Price Changes
Implementing real-time monitoring systems to detect sudden and significant price changes can help in identifying potential price manipulation attempts. By setting up alerts for abnormal price fluctuations, the platform can take corrective actions and prevent further exploitation.
In the case of BonqDAO, the reliance on instant prices from the Tellor oracle made the platform susceptible to price manipulation. By using the latest price data without allowing time for validation and scrutiny by other network participants, BonqDAO exposed itself to the risk of accepting false price information. This vulnerability enabled the attacker to manipulate the price of WALBT tokens and exploit the platform, causing significant financial losses. Implementing the above-mentioned mitigation strategies can help platforms like BonqDAO to better secure their price oracle integrations and prevent future attacks.
Transaction Analysis
Attacker’s Address: 0xcAcf2D28B2A5309e099f0C6e8C60Ec3dDf656642
Attacker’s Contract: 0xed596991ac5f1aa1858da66c67f7cfa76e54b5f1
TellorFlex Contract: 0x8f55D884CAD66B79e1a131f6bCB0e66f4fD84d5B
BONqDAO Contract: 0x4248fd3e2c055a02117eb13de4276170003ca295
Attack Transaction 1: 0x31957ecc43774d19f54d9968e95c69c882468b46860f921668f2c55fadd51b19
Attack Transaction 2: 0xa02d0c3d16d6ee0e0b6a42c3cc91997c2b40c87d777136dedebe8ee0f47f32b1
After the successful execution of both transactions, the attacker was able to steal 113.8 million WALBT tokens and 98 million BEUR tokens. They then proceeded to convert the BEUR tokens into stablecoins like USDC using Uniswap, totaling around $534K.The attacker moved the funds to the Ethereum blockchain and started to launder their gains through Tornado Cash, a privacy solution. This allowed them to obscure the origin of the funds, making it more difficult for anyone to trace their movements.
Conclusion
The BonqDAO hack serves as a stark reminder of the risks involved in decentralized finance and the need for stringent security measures to protect users’ funds. By exploiting a vulnerability in the price oracle integration, the attacker was able to manipulate the price of the WALBT token. This cause significant financial losses for the BonqDAO platform and its users.
This incident highlights the crucial role that thorough, smart contract audits play in safeguarding DeFi platforms. By conducting a comprehensive audit of the smart contracts involved, potential vulnerabilities and weaknesses can be identified and addressed before an attacker can exploit them. For a reliable and professional smart contract audit, consider partnering with BlockApex.io, a leading provider of security solutions for blockchain-based projects. Through rigorous examination and assessment, BlockApex.io can help ensure that your smart contracts are secure, protecting your platform and users from potential hacks and exploits.































