Various penetration testing mechanisms are used in the cybersecurity space, particularly in ethical hacking and for software testing. Amongst them, black box and white box penetration testing are the most widely recognized.
Penetration testing or, pen testing is a security exercise where a cyber-security expert attempts to find and exploit vulnerabilities in a computer system. The purpose of this simulated attack is to identify any weak spots in a system’s defenses that attackers could take advantage of.
In this article, we will explore black-box and white-box penetration testing, compare their key differences, and examine how both black-box and white-box testing are applied in blockchain and dApps. Finally, we’ll review some best practices for effective testing.
Research on Blockchain Testing
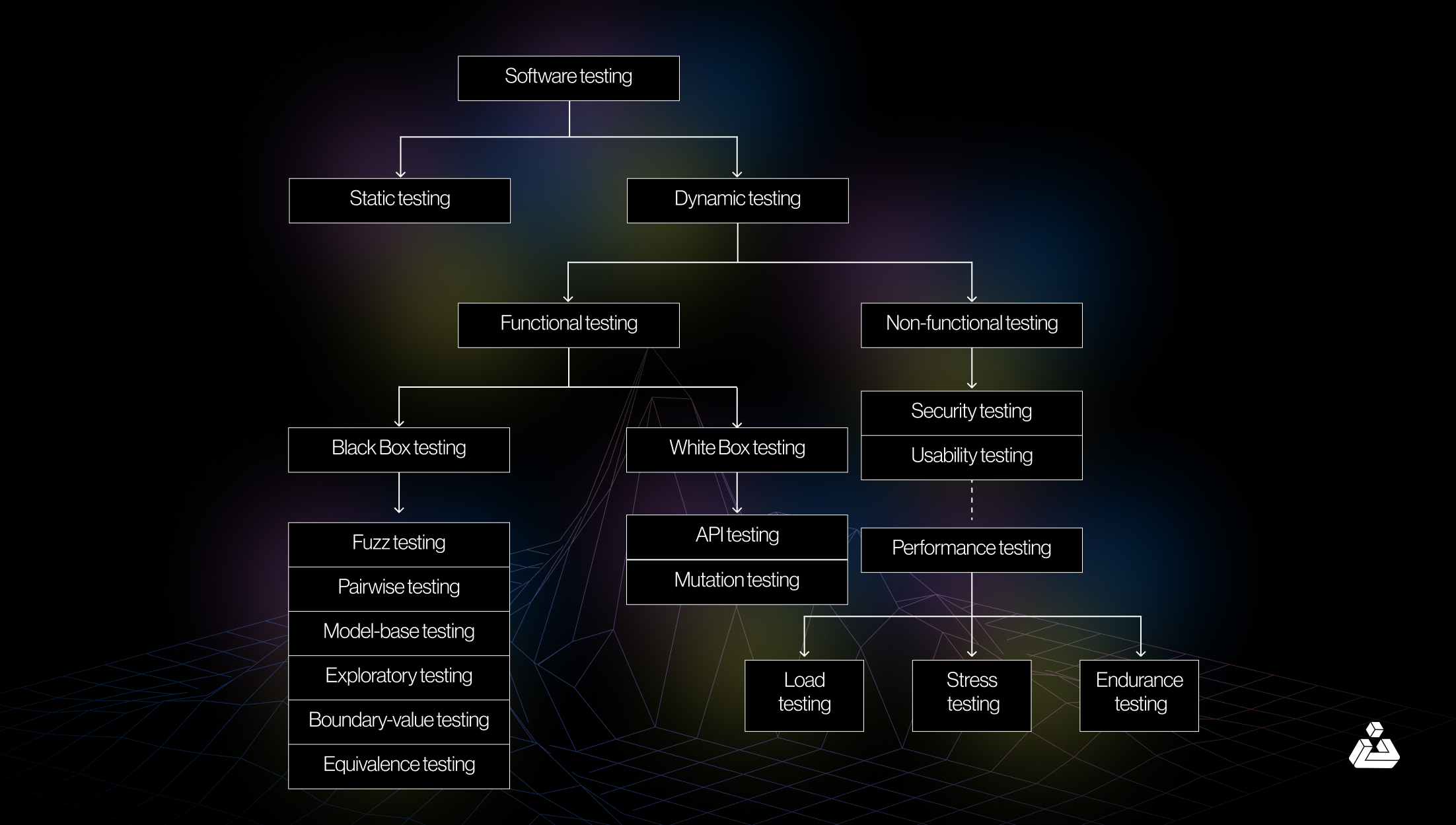
Black Box Penetration Testing
In black box testing, the tester examines the functionality without knowing the internal workings or architecture. The tester is focused on user requirements or has an outsider perspective, just like the attacker, using public information to exploit the software without knowing the internal code or functionality.
In brief, in a black box penetration test, the tester has no prior knowledge at all and simulates real-life attackers’ approach. The testing verifies whether the application functions as intended by assessing how it handles expected and unexpected user actions, response times, and potential usability or reliability issues.
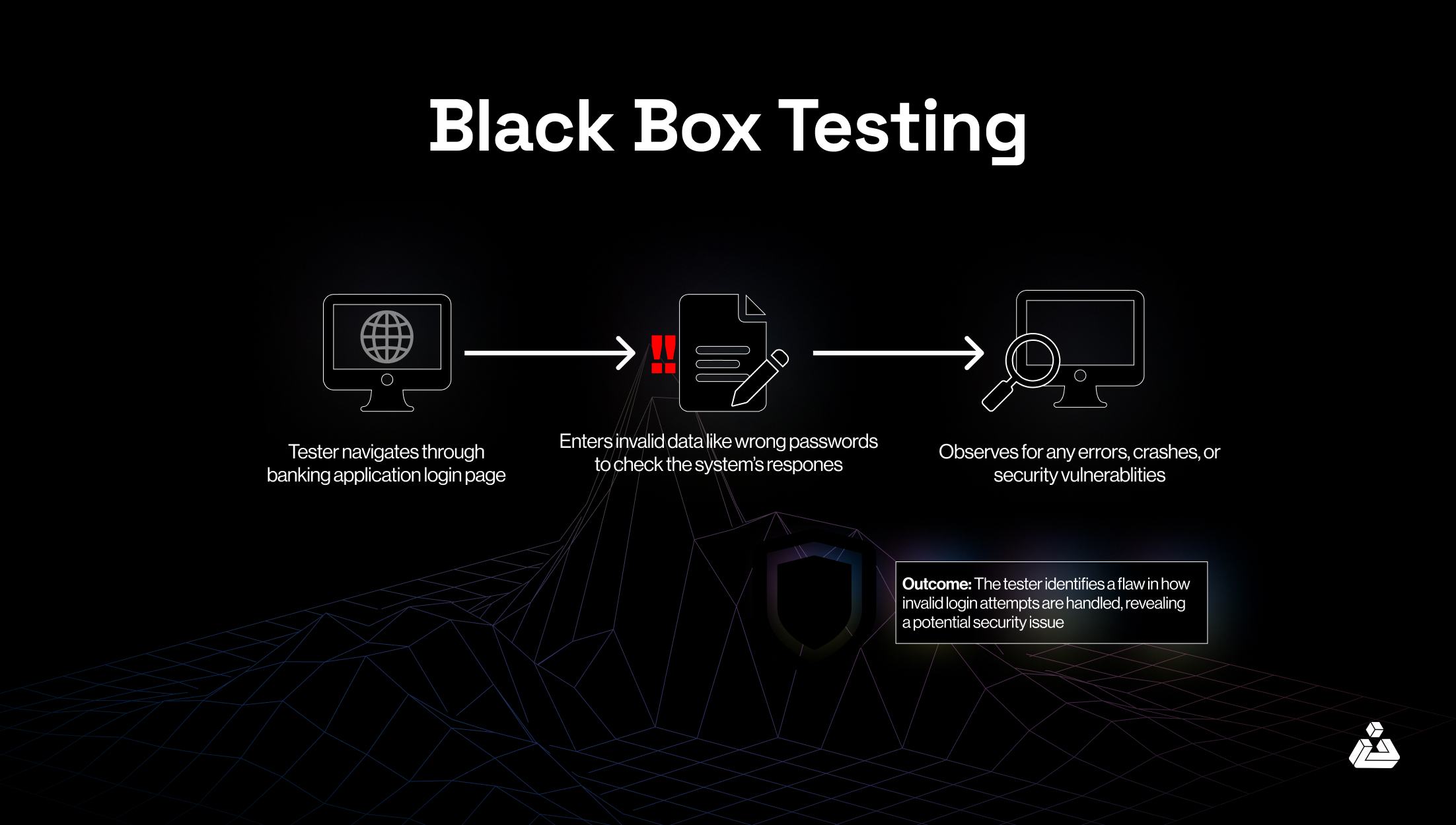
The process of black box testing is as follows, also depicted by an example in the infographic below:
- Examine the specifications and requirements of the software app
- Give valid and invalid inputs to check whether the system can process them correctly or detect errors
- Identify expected outputs for the inputs
- Compare actual vs. expected outputs
Black box testing techniques
Traditional testing techniques aim to validate that software meets functional requirements and behaves as expected, such common techniques are listed below:
-
Equivalence partitioning
It is used to divide input data into valid and invalid classes to reduce test cases. For eg: A banking app requires age input, classes are 0-17 (invalid), 18-65 (valid), and 66+ (valid). Test cases would include 15,30,70.
-
Boundary value analysis
Tests values at boundaries of input ranges to find defects.
Example: Testing age with inputs like 17 (just under valid), 18 (valid), 65 (valid), and 66 (just over valid)
-
Use case testing
Tests based on real-world scenarios to ensure user requirements are met.
For example: A test case for logging into a banking app would check for successful login, failed attempts, and lockout mechanisms after multiple incorrect passwords.
Some common security testing techniques that aim to identify vulnerabilities and weaknesses in the application that could be exploited by attackers are:
-
Vulnerability Scanning
Automated scanning to identify known security weaknesses in applications.
E.g.: Running a tool that detects SQL injection vulnerabilities in a banking website’s input fields.
-
Fuzz Testing
Inputs random or unexpected data to find vulnerabilities or crashes.
Example: Send a string of random characters to a login form to check if it handles errors gracefully or crashes.
-
Brute Force Testing
Systematically tries all possible combinations to test the strength of authentication.
For example: Use a tool to try common passwords like “password123” and “123456” to gain unauthorized access to a user account.
White Box Penetration testing
White box testing is a software testing technique that involves examining the internal structures or workings of an application. If black box testing represents “unknown” internal software, then think of white box testing as “known”.
To describe it concisely, Testers have full knowledge of the system architecture, source code, and design documents, enabling them to create test cases based on code paths, conditions, and branches. This method ensures that all paths and logic of the code are tested.
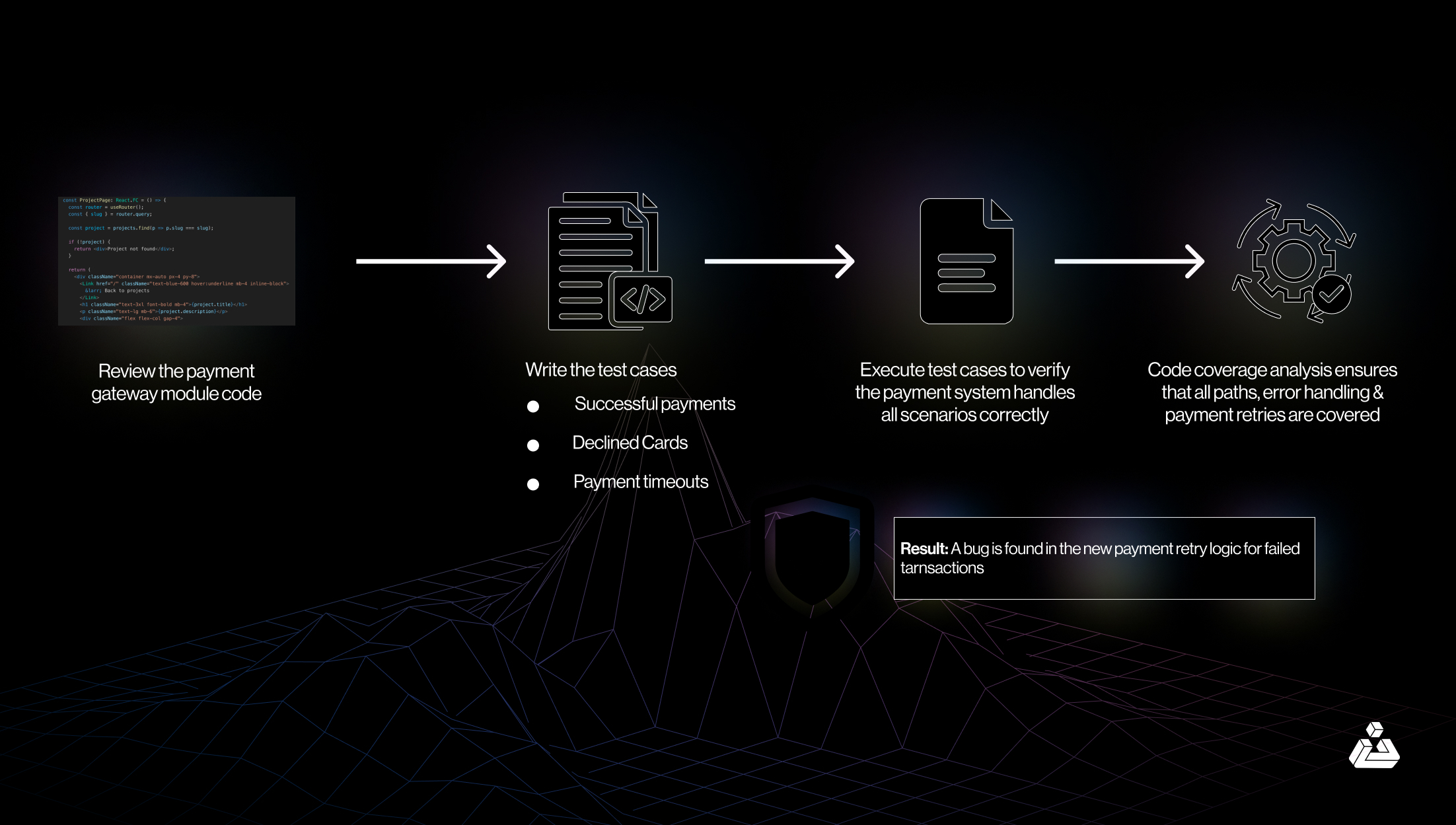
The Process of white box testing is as follows, also depicted by an elaborated example in the infographic below:
- Review the source code
- Execute test cases to assess the flow and structure of code
- Perform code coverage analysis
White Box Testing Techniques
Here are some commonly used white box testing techniques using an e-commerce website example:
-
Statement Coverage
Statement coverage ensures every line of code is executed at least once.
Testing a discount function for an e-commerce site that calculates total price. All code statements, like checking for valid coupons and applying discounts, are executed during tests.
-
Branch Coverage
Branch coverage ensures all possible branches of decision points (if/else) are tested.
In a checkout process, you would test both the successful and unsuccessful paths of payment approval (i.e., test both when the payment is approved and when it’s declined).
-
Condition Coverage
Condition coverage tests each individual condition in the code (true/false outcomes).
For applying discounts, test both when a user is eligible for the discount (e.g., logged in with a coupon) and when they aren’t (e.g., not logged in or invalid coupon).
- Multiple Condition Coverage
Multiple condition coverage tests all possible combinations of conditions.
If free shipping is applied when cart value is above $100 and the user is a premium member, you test the four combinations:
(1) Cart > $100, premium member;
(2) Cart < $100, premium member;
(3) Cart > $100, non-premium member; and
(4) Cart < $100, non-premium member.
-
Basis Path Testing
Basis path testing creates a control flow graph to cover all possible independent paths in the code.
For a coupon code application system, test all possible paths: (1) valid coupon, (2) invalid coupon, (3) expired coupon, and (4) coupon already used.
-
Loop Testing
Loop testing focuses on validating loops in the code.
In a product recommendation system, test the loop that suggests similar products after purchase. Ensure the system works with zero, one, and multiple product suggestions (testing the loop’s start, middle, and end conditions).
| Aspect | Black Box Testing | White Box Testing |
|---|---|---|
| Perspective | Evaluated from the end-user’s perspective. | Evaluated from the developer’s perspective. |
| Focus | Examines the application’s behavior. | Analyzes the performance and logic of the code. |
| Purpose | Validates functional requirements. | Validates the internal structure and logic. |
| How it works | Inputs are provided, and actual outcomes are compared with expected results. | Each code block is evaluated using test cases and coverage analysis. |
| Pros | Generally quicker and less expensive, promotes effective communication among modules, and does not require sharing of source code. | Provides more detailed insights, can be automated, and identifies hidden errors. |
| Cons | Results can be less clear and more abstract, often overlooking non-functional requirements. | Can be complex, requires specialized knowledge, and may involve higher costs. |
Since we now have a firm understanding of black box and white box penetration testing, we can see how it is applied in the blockchain like DApps (Decentralized Applications).
Black Box Testing for Blockchain/DApps
-
Using Fuzzing to Detect Weaknesses
-
- Inject random data inputs into smart contracts and DApp interfaces to find vulnerabilities.
- Example: Fuzzing a token minting function to discover unchecked integer overflows in the smart contract or fuzzing a DApp to uncover input validation weaknesses.
-
Running Attack Scenarios on DApps
-
- Simulate external attacks without internal knowledge, like replay attacks or unauthorized transactions.
- Example: Simulating replay attacks by re-submitting a previously signed transaction in a smart contract, or testing if a DApp processes duplicate or unauthorized requests without proper verification.
-
Evaluating Results from External Tests
- Compare expected vs. actual system behavior from attack simulations.
- Example: Assessing how a DApp and smart contracts handled fuzz testing and unauthorized input attempts
White Box Testing for Blockchain
-
Reviewing Smart Contracts Line by Line
-
- Thoroughly examine each line of code for errors or vulnerabilities.
- Example: Checking a token transfer function to ensure it properly validates sender/receiver details.
-
Running Tests for Vulnerabilities
-
- Execute predefined test cases to identify security flaws or weak spots.
- Example: Testing the contract for reentrancy issues or overflow vulnerabilities.
-
Analyzing Logic and Structure in Smart Contracts
-
- Validate that the contract’s logic and structure meet the intended functionality.
- Example: Ensuring a staking function properly locks tokens for a defined period.
Comparing black box and white box testing for blockchain security
| Aspect | Black Box Testing | White Box Testing |
|---|---|---|
| Perspective | External; simulates real-world attacks | Internal; reviews code structure |
| Pros | Faster; focuses on user interaction points | Deep analysis; identifies hidden code flaws |
| Cons | May miss internal logic vulnerabilities | Time-consuming; requires in-depth knowledge |
| When to Use | Ideal for testing DApp user interfaces, black box audit | Used for DApps, Crucial for smart contract audits like white box audit |
Best practices
The development of blockchain applications encounters some significant challenges, including a lack of established best practices, limited technological understanding, and the inherent complexity of the blockchain ecosystem. Insufficient guidelines can lead to ambiguities in architectural design and hinder effective collaboration among technical and non-technical stakeholders.
Additionally, the absence of specialized debugging and testing tools, coupled with the immutable nature of blockchain transactions, increases the risk of irreversible errors, making rigorous validation and verification of smart contracts essential. To address these issues, organizations should establish clear development guidelines and invest in specialized tools that facilitate testing and automation.
Implementing bug bounty programs can also enhance security, as they incentivize ethical hackers to identify vulnerabilities within blockchain applications, allowing companies to leverage the hacker community for ongoing improvements.
Comprehensive testing strategies that encompass performance, security, and dependability assessments are critical, along with fostering a culture of continuous learning to keep developers informed of the latest advancements. Finally, incorporating user-centric testing will help improve application reliability by addressing potential user errors and interactions.
Conclusion
Testing early acts as a shield against any real-world attacks or exploits much like an antivirus software or a firewall that prevents malicious actors from breaching your defenses or stepping in the territory.
BlockApex, a blockchain consulting company, is your Thor, a Marvel character known as a warrior protector. We vow to safeguard your assets through early testing techniques and assessments. Reach out to us today to secure your systems with our smart contract audit services!