Recently, there has been a clear surge in the contribution towards a decentralized form of the internet known as Web3. This has resulted in the popularization of blockchain technology and its many use cases. Blockchain-based systems are expected to be the driving force of this new era of the internet, due to the advantages they provide in terms of anonymity, trust management, and security.
However, despite its many benefits, it is imperative to note that this technology does not come with foolproof systems in place for cybersecurity; rather, this is an area that requires continual understanding by those working in the space. In an effort to contribute to this crucial cause, we have decided to launch a two-part series discussing both the problems of cybersecurity in blockchain systems as well as their possible solutions. Through this, we hope to educate cybersecurity engineers and other security professionals about the most principal problem areas, so they may use their knowledge to further improve these systems in the future.
Undoubtedly, the first step to achieving truly secure systems is to identify where the problem lies. This publication will attempt to achieve exactly this- pinpointing existing holes or gaps that can create the most risk for future users.
Importance Of Securing The Blockchain
A major pillar of blockchain technology is transparency. This means that any system built on blockchain is by definition public- a fact that introduces an entirely new set of vulnerabilities and threats. As a result, cleverly orchestrated hacks on blockchain solutions are not an uncommon feat. Even the biggest names in the field continue to suffer from attacks, resulting in losses equating to millions of dollars.
According to blockchain analytics firm Chainalysis, cryptocurrency-based crime hit a new all-time high in 2021, totaling $14 billion worth of illicit money over the year. If the adoption of blockchain technology increases in the coming years (as it is expected to with the advent of Web3), the opportunities for such crime may also increase. This makes the importance of securing blockchain even more significant.
Source: Crypto Crime Report 2022 by Chainalysis
Key Rudimentary Concepts
Before we dive into analyzing the most pressing security problems in blockchain today, it is important to have a substantial understanding of the security domain in general. Below are some basic preliminary concepts that play a major role in discussion related to security in blockchain-based systems.
The 5 Security Dimensions With Reference To Blockchain
Any discussion on security is incomplete without the understanding of the five pillars that are said to build up this field’s foundation.
These dimensions are stated to be confidentiality, integrity, availability, authenticity, and non-repudiation. Let us discuss each of them separately.
Confidentiality
The first dimension is confidentiality. This means that any information which is being exchanged or stored within a system is safe from unauthorized individuals, groups, or organizations. In other words, only those who are authorized to view that information have access to it. In blockchain-based systems, this is typically achieved with the help of asymmetric cryptography and key management techniques.
Integrity
If the first dimension was concerned with the privacy of data, the second has more to do with its overall accuracy. This involves making sure that an information system is not tampered with by any unauthorized entities, as this may result in the altering or destroying of data. In the blockchain, stored data is immutable and permanent. As this means that once data is added to the chain it cannot be modified or deleted by anyone, it is said to meet integrity requirements. However, this does not ensure that the entered data on-chain is accurate by design, and is an area that requires key focus by cybersecurity engineers in building future blockchain-based systems.
Availability
This dimension refers to the easy access of data for authorized users. This means that regardless of any mitigating external conditions, all information and resources should remain robust and fully functional at all times. Though this is commonly upheld in most on-chain solutions in the blockchain, off-chain solutions have been said to struggle with this. The off-chain availability problem has been cited as a current major challenge, particularly in state channel applications.
Authenticity
The fourth dimension is designed to prevent the impersonation of authorized users by putting in place certain security measures which verify users’ identity. In general applications, this includes the use of fields like usernames, passwords, emails, and biometrics. This security measure also takes into account the validity of transactions and messages. Blockchain-based systems design emphasizes anonymity, complicating the authentication process beyond simple email and biometric collection. Instead, cryptographic keys perform this role, using a data string to identify users and grant access to their accounts or wallets.
Non-repudiation
The fifth and final dimension, known as non-repudiation, involves substantial proof that data was sent, accessed, and received by users, preventing any party from denying this claim’s validity. In the blockchain, digital signatures typically implement this, unlocking transactions for authenticated users. By this property, any user that has signed some information or transaction cannot at a later time deny having done so.
Relationship Between Cybersecurity and Blockchain Security
As discussed in the section above, parts of blockchain’s fundamental features indeed guarantee the five dimensions of security to some extent. Elements of the basic design of this technology such as cryptography, hashing algorithms, and digital signatures reiterate the fact that it was built with a focus on security in mind.
However, this does not mean that there is no room for improvement. Businesses employing blockchains, like other systems, must adopt cybersecurity measures and standards to defend themselves from external threats.
Cillian Leonowicz, Senior Manager at Deloitte Ireland further stresses the importance of this, stating that, “blockchain’s characteristics do not provide an impenetrable panacea to all cyber ills, to think the same would be naïve at best. Instead, as with other technologies, blockchain implementations and rollouts must include typical system and network cybersecurity controls, due diligence, practice, and procedures”.
Discussions also extensively cover the converse relationship, where blockchain is seen as a potential force in strengthening existing platforms’ cybersecurity. Proposed ideas involve secure private messaging, a decentralized DNS, and blockchain use for securing IoT devices, though current implementations of these use cases are minimal.
The Blockchain Trilemma
The blockchain trilemma is a concept coined by Vitalik Buterin, one of the founders of Ethereum. It refers to a 3-way tradeoff between decentralization, scalability, and security that developers working in blockchain technology experience. Below are the concepts explained individually:
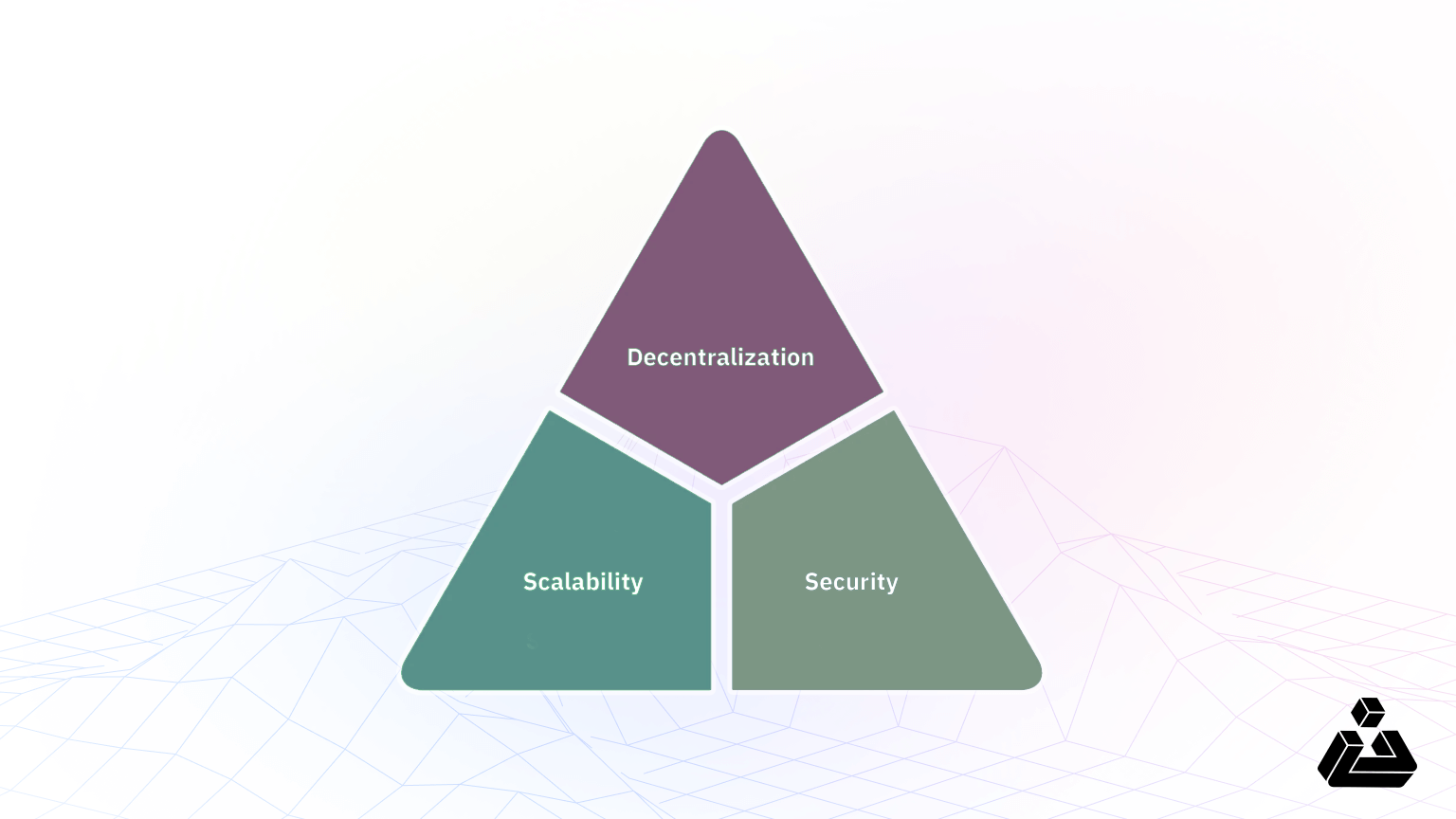
Decentralization: creating a blockchain system that does not rely on a singular point of control.
Scalability: the ability of a blockchain system to handle an increasing amount of transactions.
Security: the ability of a blockchain system to defend itself from malicious attacks, bugs, and any other unforeseen issues.
Despite each being equally important, achieving all three within one system is extremely difficult. Some even go as far as to say that this trilemma is the result of an inherent flaw in the design of blockchain technology. Although this model cannot be considered fact, it contributes to the idea that blockchain technology lacks inherent superior safety mechanisms. Securing these systems might be more difficult and, therefore, more necessary than others.
The Most Pressing Security Problems in Blockchain
There are some features within blockchain-based systems that contribute to the most risk. Below are some of the key areas we have identified in our research.
The Absence Of Unlinkability
Anonymity is often quoted as being one of the key principles of blockchain technology, allowing any user to participate in the space without revealing their true identity. However, because the nature of blockchain is such that it is a public ledger, it can be very easy for anyone to formulate ideas about a particular user’s identity based on their transaction history. This failure to provide protection of unlinkability for users’ transactions is one of this field’s major problem areas, leading to a host of issues in terms of the security and privacy of users.
Source: Bitquery Coinpath Archives
The absence of unlinkability in blockchain can be further understood with the help of visualization tools. Blockchain data company Bitquery has created a set of blockchain money tracing APIs known as Coinpath, which can be used to display information about transactions such as the creation of clusters, transaction flows, the account balance of a specific wallet, as well as all the source and destination addresses that sent or received transactions from any address. Cryptocurrency exchange platform Coinbase has created a similar tool by the name of Coinbase Analytics, which connects transactions to real-world entities while also monitoring risk on millions of addresses.
Poor Confidentiality of Transactions
Blockchain systems like Ethereum use smart contracts to implement complex transactions. These require both the data of the smart contract as well as the code it runs on to be public, along with the condition that every miner must emulate executing each contract. This can lead to the leakage of user information. Similarly, in Bitcoin, the content of transactions such as transaction amount as well as addresses is entirely public. This may further increase the risk of linkage, where a pseudonym provided to the blockchain is mapped onto a user’s true identity, a problem that poses a further risk in the case of sensitive transactions and private data.
The risk of storing private data on-chain is one of the biggest limitations of blockchain today. Many even argue that this same problem is what is stopping Web3 from going mainstream. It is possible that a model of need-to-know-based sharing (rather than the current one in place in which anything and everything is publicly viewable) would be much safer for users in the long run. Until then, it is critical to design and implement stronger protection mechanisms for privacy-preserving smart contracts.
Immutability of The Blockchain
One of the core features of blockchain technology is its immutability. This means that once data is added to the blockchain, it is there forever, and cannot be altered or changed in any way. Although this property is beneficial in preventing the manipulation of data or when mitigating double-spending attacks, it does bring forth some issues as well.
Since data on-chain cannot be altered or deleted, it can lead to mass redundancy which can slow down processing on the network. Mistakes are also difficult to correct, such as in the case of faulty code in smart contracts, leading to bigger problems of security.
We know that Web2 generates an immense amount of data, with estimates pointing to over 2.5 quintillion bytes each day. If blockchain-powered Web3 were to generate the same amount of data, it would theoretically become immutable, potentially leading to many practical issues.
Key Management Risk
On the blockchain, ownership of any digital asset is synonymous with the possession of keys. If someone were to steal the private key of a user, the ownership of assets connected to that key would be taken away from them, making it so that the asset is no longer theirs. Stolen digital assets may become unrecoverable in most cases, especially if there is no administrator or system controller.
Oftentimes attackers find the best approach to gain keys is to attack the weakest link in the chain, which in this case is personal or cellular computers that are utilized by most users of the space. Hence, it is critical for cybersecurity engineers to follow the best practices in the use of wallets and key management to mitigate this problem.
Integrity and Availability Issues In Off-chain Solutions
Off-chain solutions help solve existing problems of scalability and speed that exist in on-chain solutions. They typically tend to be cheaper, faster, and more private, and give users control over what information they want to be made publicly available.
However, despite its advantages, off-chain solutions possess risks for users in terms of data integrity. Because it is difficult to modify data without being noticed by the rest of the network, integrity is ensured by default in layer 1 blockchain solutions. When data is stored outside of the blockchain, however, this capability is removed because the storage is handled by a third party. If for any reason this third party system or process fails to provide the necessary service, then the whole process of integration between on-chain and off-chain fails, which would eventually result in loss of data for the users
Compromisable Areas In Existing Blockchain Systems
Wallet Hacking
Cryptocurrency owners store their assets in crypto wallets. To ensure the security of these assets, each wallet generates a seed phrase that users can use to recover it if misplaced, damaged, or deleted. As long as the seed phrase is protected, the user’s funds remain secure.
If a person’s seed phrase were to become stolen, however, it would mean that the assets in the wallet connected to that seed phrase are also not safe. An attacker can easily capitalize on a leaked seed phrase to take control of a user’s funds. A recent phishing attack on the Discord space of popular NFT collectible Cryptopunks achieved exactly this, manipulating a user into entering their seed phrase for the chance to win “ten super unique NFT avatars”. Within seconds, the user’s wallet was wiped clean.
Some apps on Web2 have also made this simple mistake, with one application asking users to input their seed phrases as a way to login into the application, as shown in the image above. Many pointed this out as being not only highly irresponsible, but also dangerous as seed phrases are the root of a person’s digital identity.
Securing Keys Of Centralized Bridges
Blockchain bridges have been introduced as a solution to the blockchain interoperability problem. These bridges link two independently functioning blockchains together. Users can then use this technology to achieve a variety of tasks, including the transfer of assets, cross-chain lending, and execution of dapps on many platforms instead of just one.
However, it is important to note that almost all blockchain bridges have a central server through which they operate, such as AWS or Hostinger. Hence, their private key storage mechanism must be scrutinized to ensure there is no leakage or compromising in any way, as trusting the private keys of bridges to third-party services is itself irresponsible.
Data Traceability in Centralized Exchanges
Another compromisable area is in the case of centralized exchanges such as OpenSea. These entities store an extreme amount of users’ data, with some exchanges like Binance even requiring pictures of a user’s identity cards as well as verification of addresses to register onto the platform.
Though justified as a measure to keep bad actors away from the space, it cannot be denied that such actions can increase data traceability, further exacerbating the unlikability problem discussed previously.
Reliance Of Dapps On Third-Party Services
Despite being decentralized by name, it is true that the majority of dapps depend on third-party services like Infura, Alchemy, or Truffle to function. Working very similarly to centralized Web2 servers, these companies promise to provide developers on Ethereum with the tools and infrastructure they need to take their app from testing to deployment- making them a very lucrative option.
The easiness provided by these platforms results in them being relied on by most Ethereum developers. Michael Wuehler, the co-founder of Infura, has explained why this can be potentially dangerous, stating, “If every single dapp in the world is pointed to Infura, and we decided to turn that off, then we could, and the dapps would stop working. That’s the concern and that’s a valid concern.”
In addition, a situation like this would mean that if any of these services were to become compromised in any way, every dapp associated with them would also be unsafe.
Conclusion
The pressing need to provide security to blockchain-based systems has become even more apparent in the past few years. As the number of blockchain solutions skyrockets, so does the audience of potential users, leading to a greater attack surface and more dangerous repercussions if something were to go wrong.
In this publication, we have attempted to outline the current problems blockchain-based systems face in achieving the security of their platforms. We have discussed several major points, including the importance of securing blockchains, the most pressing security concerns, and compromisable areas in existing systems that implement this technology.
A remark by Sheila Warren, Platform Head at the World Economic Forum, best summarizes the current state of affairs:
“Blockchain technology can’t solve for the human factor. If someone inputs garbage data onto a blockchain, that garbage is recorded forever and can inadvertently become a flawed source of truth. Thus, an analysis of data hygiene is a critical precursor to any blockchain deployment.” – Sheila Warren, Platform Head – Blockchain, Digital Currency, and Data Policy, World Economic Forum
In the future, we will explore the solutions to the problems addressed in this piece. In this way, we hope to educate cybersecurity engineers and security professionals to ensure our systems remain as secure as possible.
References
Chainalysis. (n.d.). 2022 Crypto Crime Report. Retrieved February 18, 2022, from
https://go.chainalysis.com/rs/503-FAP-074/images/Crypto-Crime-Report-2022.pdf
Gimenez-Aguilar, M., de Fuentes, J. M., Gonzalez-Manzano, L., & Arroyo, D. (2021). Achieving
cybersecurity in Blockchain-based systems: A survey. Future Generation Computer Systems, 124, 91–118. https://doi.org/10.1016/j.future.2021.05.007
Liu, L., Zhang, R., & Xue, R. (2019). Security and Privacy in Blockchain. ACM Comput. Surv.,
https://doi.org/https://doi.org/10.1145/3316481
Lumb, R. (2016, September 9). Downside of bitcoin: A ledger that can’t be corrected. The New York Times. Retrieved March 3, 2022, from https://www.nytimes.com/2016/09/10/business/dealbook/downside-of-virtual-currencies-a-ledger-that-cant-be-corrected.html
Molina, F. (2021). Constructing privacy-aware blockchain solutions: Design guidelines and threat analysis techniques (thesis). Universidad De La Republica Del Uruguay.
Tovanich, N., Heulot, N., Fekete, J.-D., & Isenberg, P. (2021). Visualization of blockchain data: A
systematic review. IEEE Transactions on Visualization and Computer Graphics, 27(7), 3135–3152. https://doi.org/10.1109/tvcg.2019.2963018
WEF Blockchain Toolkit: Data Integrity. World Economic Forum | Data Integrity. (n.d.). Retrieved February 25, 2022, from https://widgets.weforum.org/blockchain-toolkit/data-integrity/index.html
Also read :
GameFi: Future of Gaming or Short-lived Gimmick?































