Blockchain technology operates on the principles of transparency and trust, where cryptography serves as the fundamental tool for ensuring security and integrity. While basic encryption techniques like hashing and digital signatures establish the foundation, advanced cryptographic methods provide enhanced capabilities to protect transactions, secure data, and empower users within decentralized networks.
Multi-Signature Schemes
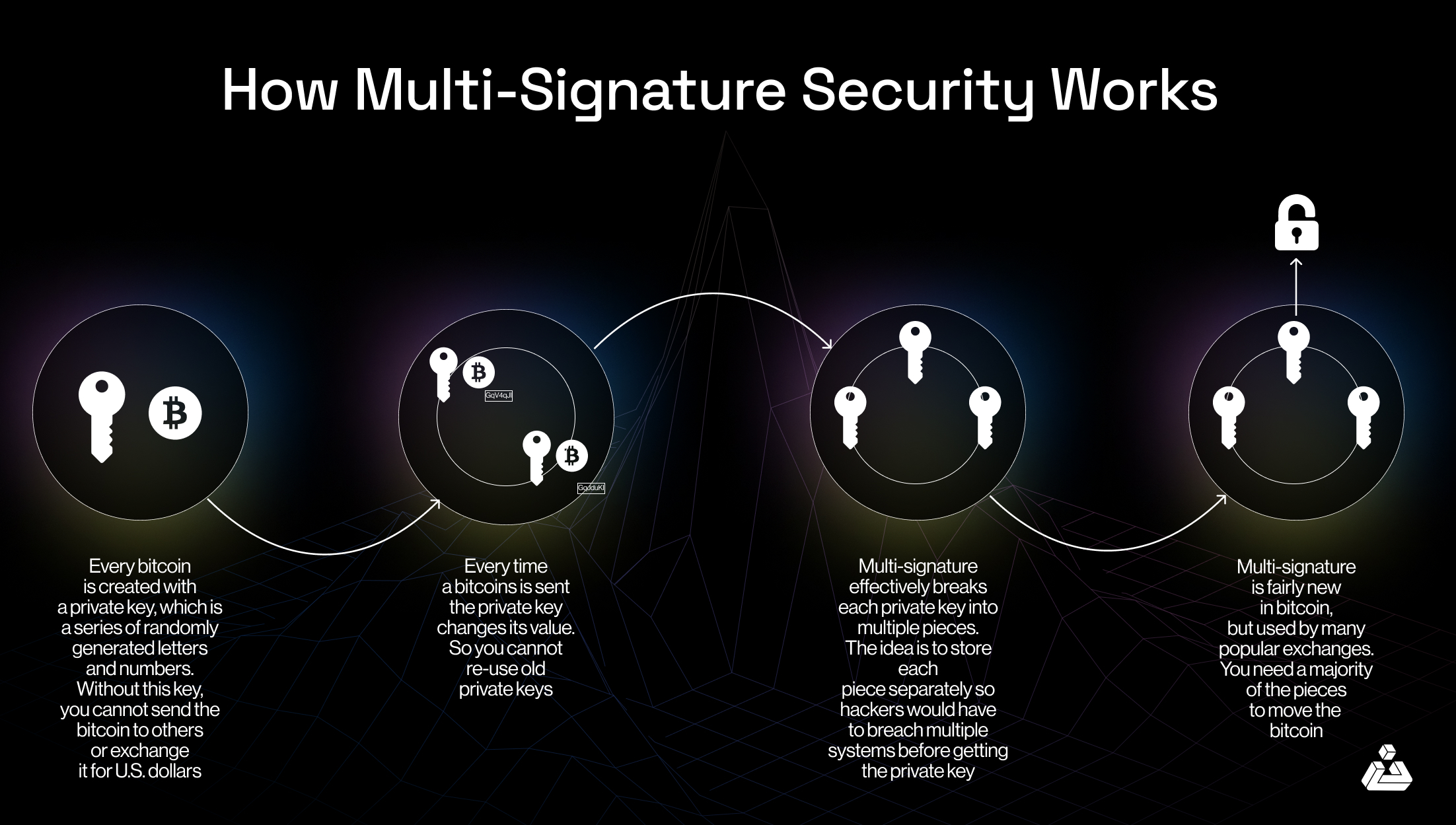
Multi-signature (multi-sig) schemes require multiple private keys to authorize a transaction. Unlike traditional signatures, where one key is sufficient, multi-sig mandates signatures from a set of keys.
Multi-sig wallets require multiple signatures to approve a transaction, which helps prevent unauthorized access. For example, in a 2-of-3 multi-sig wallet, at least two of the three authorized parties must sign off for a transaction to be valid.
Organizations can implement multi-sig to ensure that corporate decisions or transactions are approved by multiple stakeholders, enhancing accountability and reducing the risk of fraud.
Zero-Knowledge Proofs (ZKPs)
Zero-knowledge proofs (ZKPs) enable one party (the prover) to prove to another party (the verifier) that they know a value or fact without revealing the actual information. In the context of blockchain, ZKPs provide a powerful tool for maintaining privacy while ensuring data validity and security.
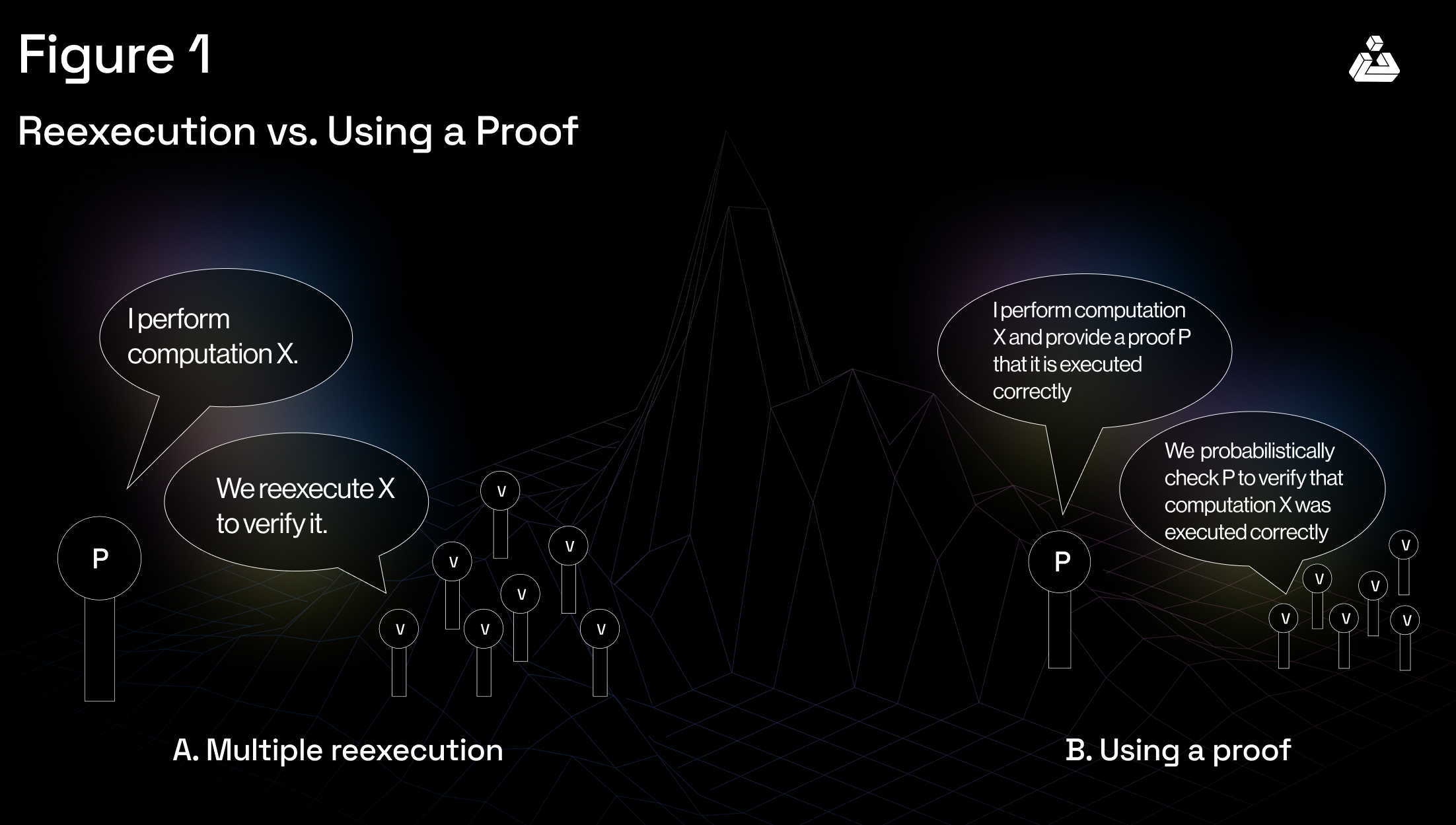
Using ZKPs, a blockchain participant can demonstrate they have the necessary means or data to perform a transaction without exposing any sensitive information. For instance, a user can prove they have enough cryptocurrency to make a transaction without revealing their actual balance.
ZKPs can confirm identity attributes (like age or citizenship) without exposing personal data, thereby enhancing privacy in identity management systems.
Homomorphic Encryption
Homomorphic encryption allows computations to be performed on ciphertexts, generating an encrypted result that, when decrypted, matches the result of operations performed on the plaintext.
Financial services can analyze encrypted transaction data to detect fraud or analyze spending patterns without accessing the raw data. This allows secure processing and analysis without compromising user privacy.
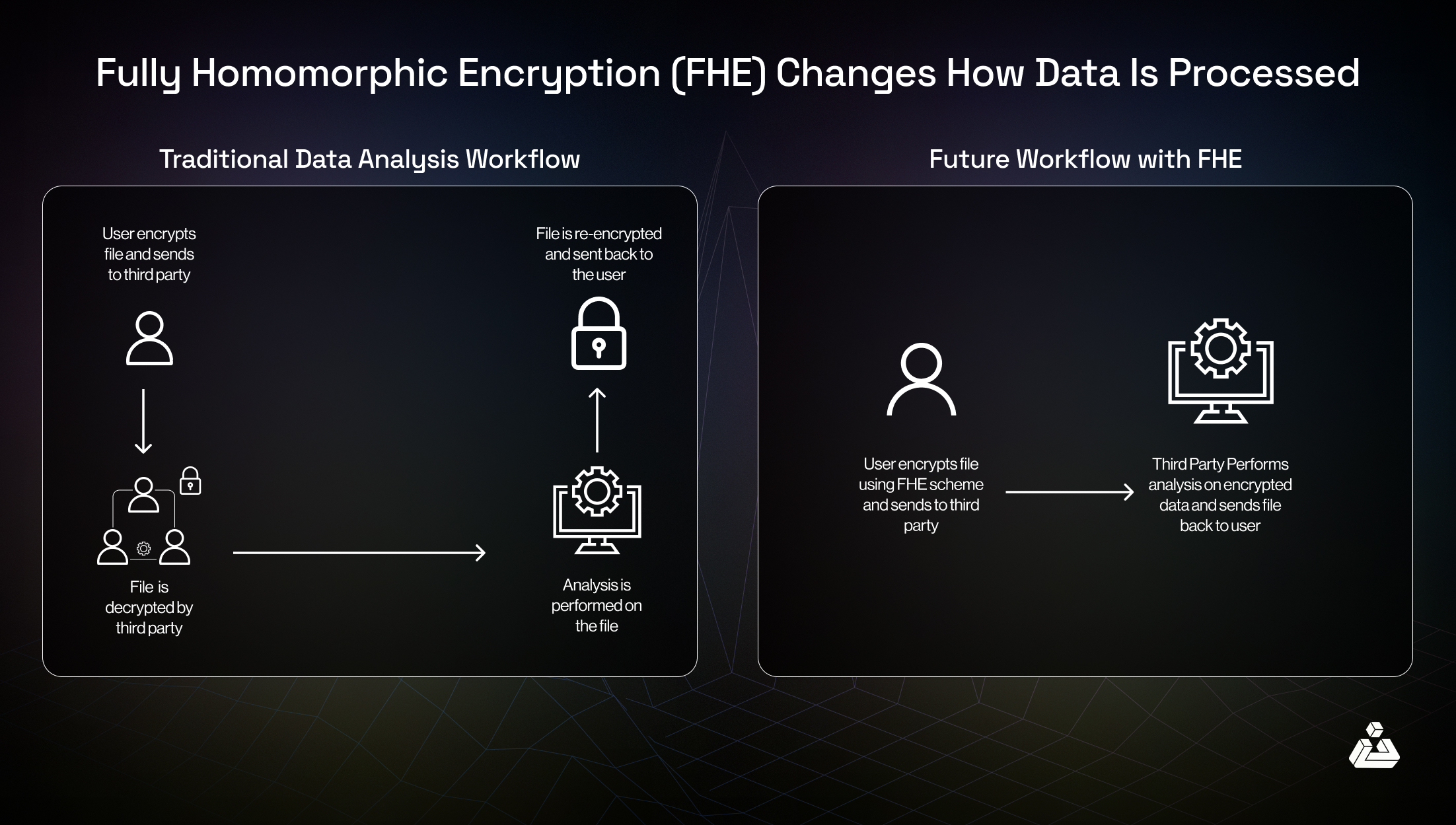
Voters can submit encrypted votes that can be tallied without decrypting individual votes, ensuring privacy and integrity in blockchain-based voting systems.
Threshold Cryptography
Threshold cryptography divides a secret into multiple parts and distributes them among participants. A minimum number of parts (the threshold) is required to reconstruct the secret.
Private keys can be split among multiple parties. Only a subset of these parties (meeting the threshold) can reconstruct the key and authorize a transaction, which mitigates the risk of key compromise.
Participants can collaboratively compute a function over their inputs while keeping those inputs private, which is useful in scenarios like collective decision-making or secure auctions.
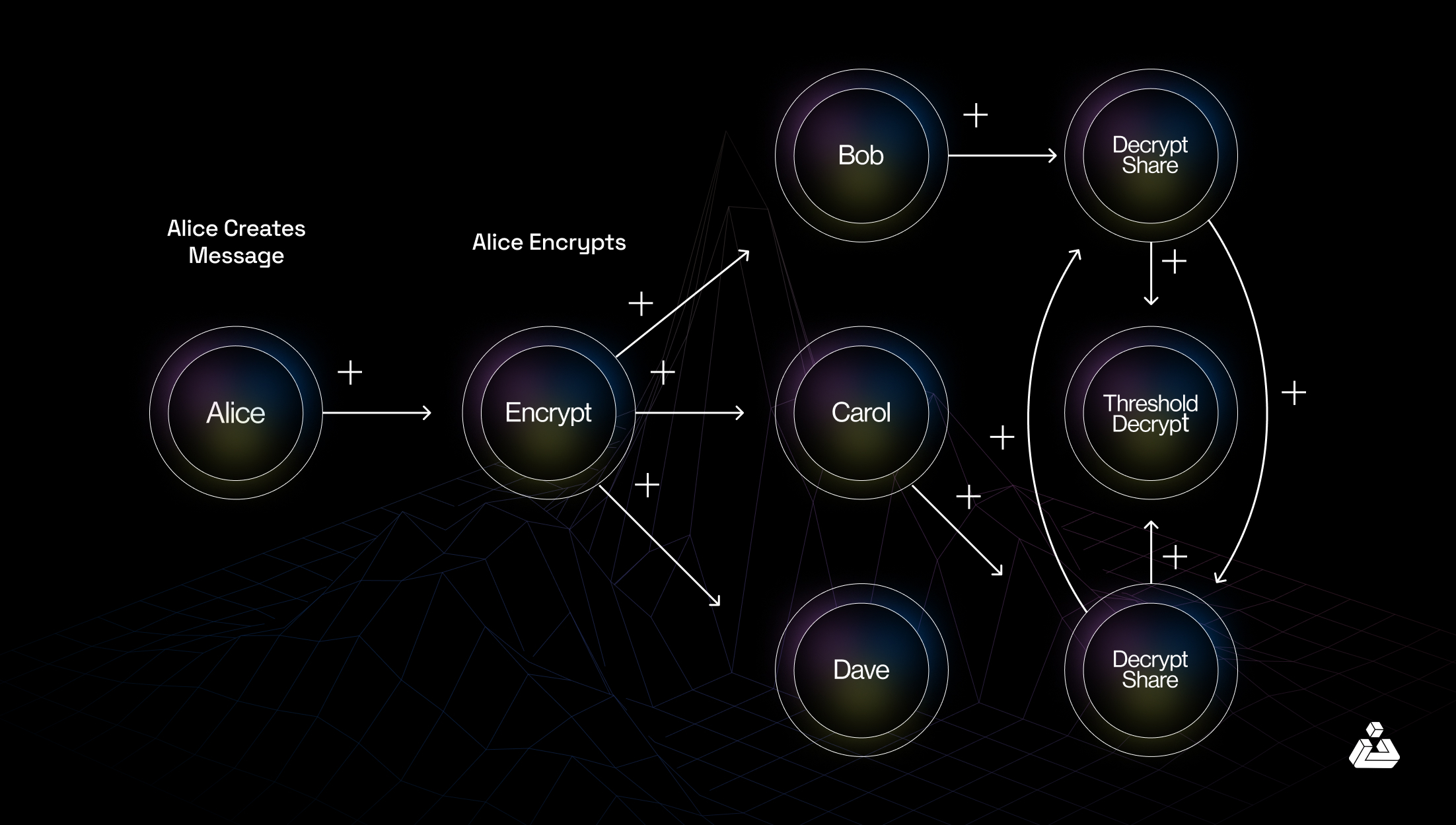
A diagram showing the process of breaking a key into several parts. The system then requires a threshold number (2 out of 3) to reconstruct the key.
Stealth Addresses
Stealth addresses allow the creation of one-time addresses for transactions, making it difficult to link transactions to a single user.
Cryptocurrencies like Monero use stealth addresses to enhance privacy by ensuring that each transaction is unlinkable. This prevents tracking of user activity and balances.
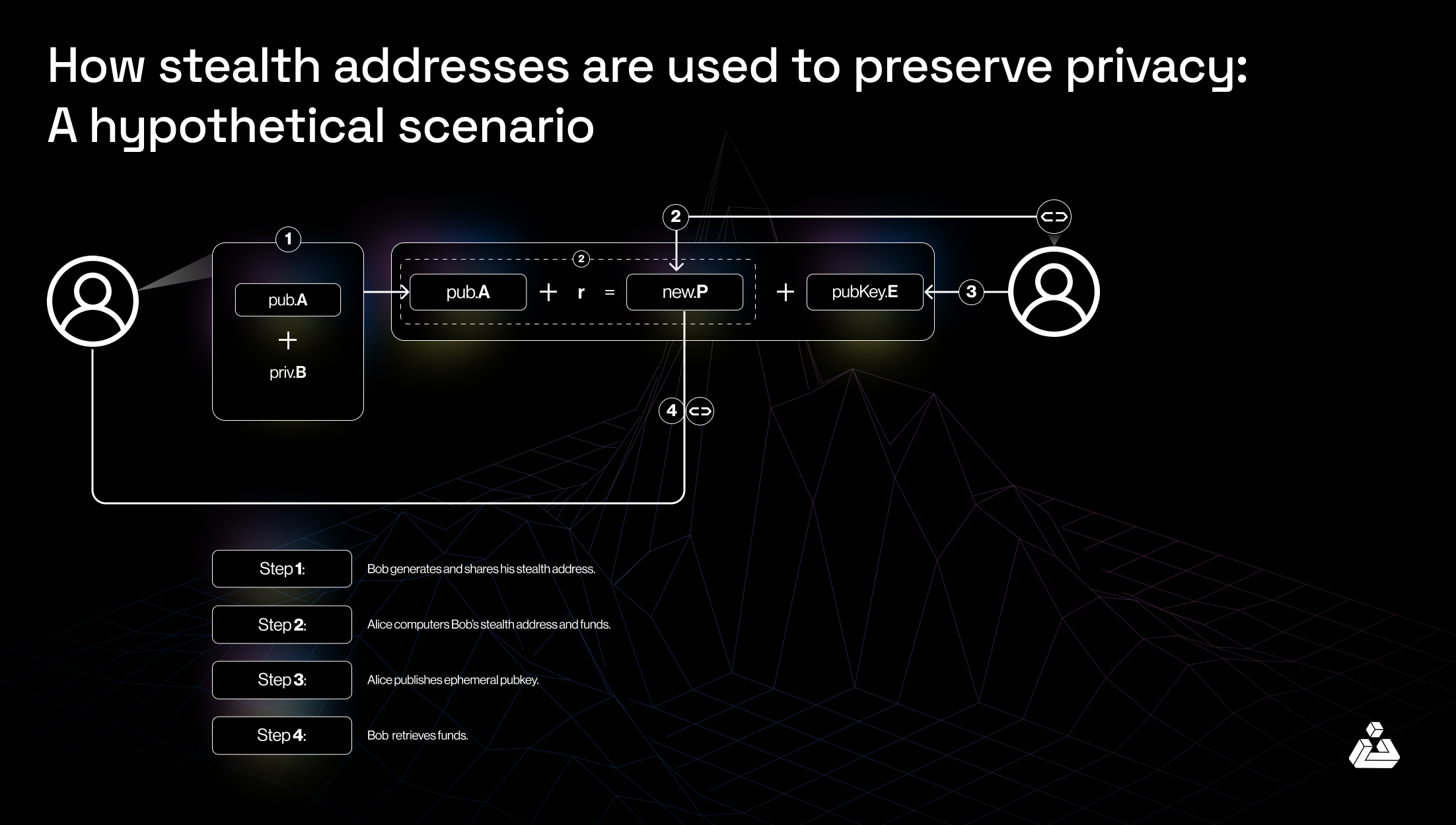
Charitable organizations can receive donations without revealing donor identities, protecting the privacy of contributors.
Ring Signatures
Ring signatures allow a message to be signed by any member of a group, without revealing which member signed it.
In privacy-focused cryptocurrencies like Monero, ring signatures ensure that the identity of the sender in a transaction is concealed within a group of possible senders, making it impossible to trace the transaction back to a single user.
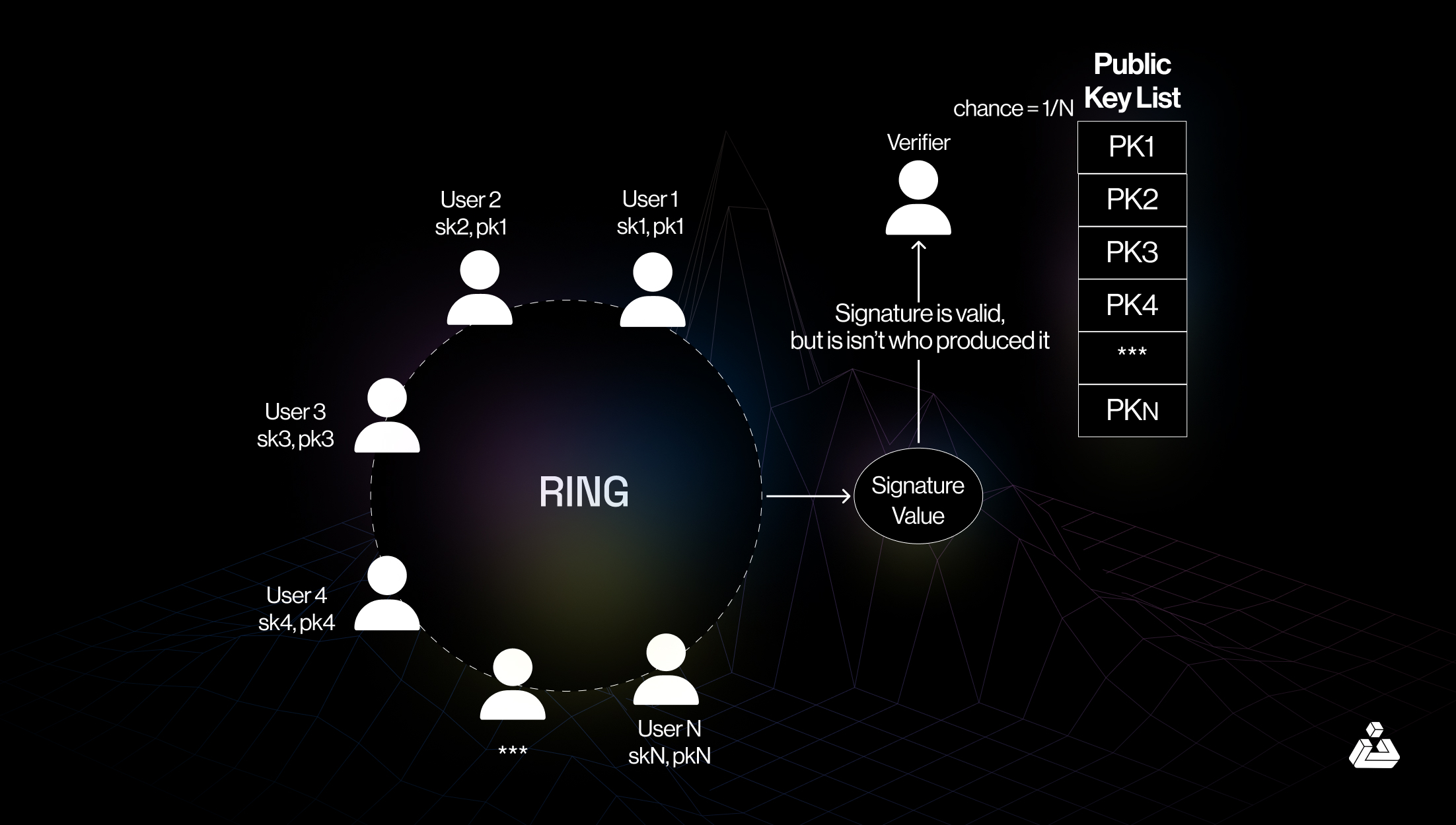
Useful in scenarios where actions need to be taken on behalf of a group without revealing the individual who authorized the action.
Real-World Applications of Advanced Cryptography
Apart from being a prominent part of blockchain technology in general, we can already see multiple uses of cryptography in applications.
Supply Chain Management
Ensures transparency and authenticity throughout the supply chain. Multi-signature schemes verify product transfers, while zero-knowledge proofs validate product authenticity without revealing sensitive details. Homomorphic encryption secures pricing and trade secrets.
Identity Management
Protects personal information in blockchain-based identity systems. Zero-knowledge proofs facilitate identity verification without exposing unnecessary data, while threshold cryptography ensures secure key distribution and management.
Financial Transactions
Secures cryptocurrency wallets and transactions through multi-signature schemes. Zero-knowledge proofs enable anonymous transactions while maintaining regulatory compliance. Homomorphic encryption safeguards financial data integrity and confidentiality.
If you strive to build secure, scalable, and future-proof blockchain solutions that drive real-world value, BlockApex can be your trusted partner in navigating these complexities with our 5+ years of expertise in blockchain technology.
Future Trends
As blockchain is getting more and more adoption, one main concern we can clearly see is that of privacy. To collide with this head-on some of the most prominent emerging future trends are:
Lightweight Cryptography
Traditional cryptographic techniques can be computationally expensive. Lightweight cryptography explores new algorithms and approaches that require less processing power. This is crucial for scaling blockchain applications to handle a larger user base and enable wider adoption on devices with limited resources.
Post-Quantum Cryptography
Current cryptographic algorithms rely on mathematical problems like integer factorization, which could be broken by future quantum computers. Post-quantum cryptography focuses on developing new algorithms resistant to these potential attacks, ensuring the long-term security of blockchain systems.
Conclusion
Advanced cryptographic techniques play a pivotal role in advancing blockchain technology beyond its foundational principles. By enhancing security, preserving privacy, and enabling innovative applications across industries, these techniques contribute to building a more secure, transparent, and trustworthy decentralized ecosystem. As blockchain continues to evolve, ongoing research and innovation in cryptography will be essential to addressing emerging challenges and unlocking new possibilities for decentralized applications.
Ready to secure your blockchain solutions with cutting-edge cryptographic techniques? Contact BlockApex today to learn how we can help you build a future-proof, secure blockchain system.
FAQs
- What is advanced cryptography?
Advanced cryptography involves sophisticated techniques and algorithms to enhance security, privacy, and integrity in digital communications and data storage. These methods go beyond basic encryption to provide robust solutions for secure data exchange, authentication, and privacy protection.
- What type of cryptography is used in blockchain?
Blockchain uses a variety of cryptographic techniques, including hashing (e.g., SHA-256), public key cryptography (e.g., ECDSA), and advanced methods like zero-knowledge proofs, multi-signature schemes, and homomorphic encryption.
- What are the 3 main types of cryptographic algorithms?
The three main types of cryptographic algorithms are symmetric-key algorithms (e.g., AES), asymmetric-key algorithms (e.g., RSA), and hashing algorithms (e.g., SHA-256).
- Is AES used in blockchain?
AES (Advanced Encryption Standard) is primarily used for encrypting data and is not typically used for core blockchain operations. However, it can be employed in blockchain applications to secure stored data and communication channels.
- What is Fault Tolerance?
The fault-tolerance of a system simply refers to the system’s ability to continue operating despite failures or malfunctions.































