Bedrock is a multi-asset liquidity re-hypothecation protocol that allows the collateralization of assets like wBTC, ETH, and IoTeX through its non-custodial platform. It was developed in collaboration with RockX and supports re-hypothecation/collateralization for multiple digital assets, such as uniBTC (wrapped BTC), uniETH, and uniIOTX, offering unique opportunities for users to earn rewards on their staked assets.
Despite its promising architecture, the protocol suffered a devastating exploit on the Ethereum chain that resulted in a significant financial loss. This hack led to a total profit of 649.6 WETH, equivalent to approximately $1.7 million, for the attacker. In this report, we will analyze the attack methodology, and the technical flaws that were exploited, and provide recommendations for enhancing the protocol’s security
Hack Impact
On October 7, 2024, the Bedrock Protocol experienced a breach that led to the extraction of 649.6 WETH from the system by the attacker, who exploited a flaw in the uniBTC minting mechanism. The attack leveraged a miscalculation in the exchange rate between WETH and uniBTC, which caused the system to mint uniBTC at a drastically incorrect ratio of 1:1 (ETH to BTC), despite the large difference in value between the two. As a result, the attacker was able to inflate their holdings significantly and drain the project’s liquidity.
UniBtc Protocol Hack Explained
Step 1: Flashloan Borrowing
The attack began with the attacker borrowing 30.8 WETH via a flashloan through Balancer. Flashloans allow users to borrow assets without collateral as long as the loan is repaid within the same transaction. This capital would serve as the initial fuel for executing the exploit.
Step 2: Minting uniBTC with Incorrect Exchange Rate
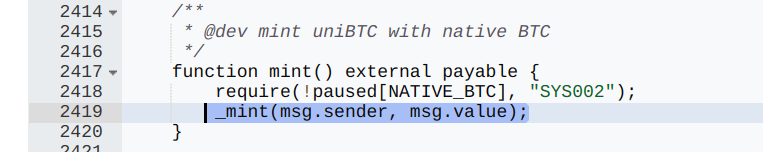
Next, the attacker exploited a flaw in Bedrock’s mint function. By calling the mint function in the Bedrock Vault contract, the attacker transferred the borrowed 30.8 ETH to the Vault, triggering the following line of code:
The mint function internally calls the _mint function:
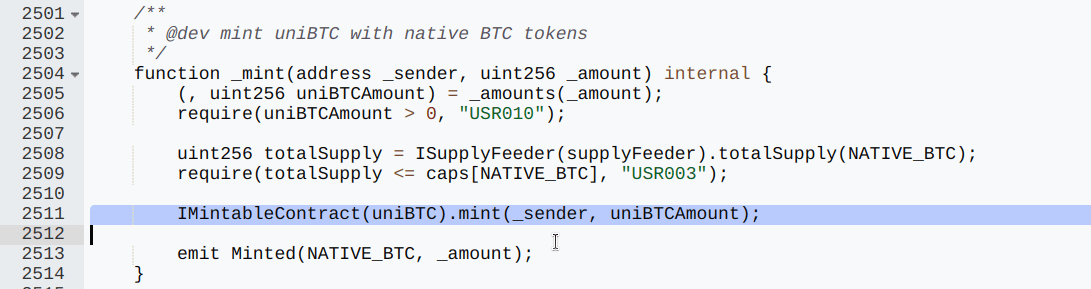
In this mint function, Bedrock’s internal logic failed to handle the exchange rate between WETH and uniBTC correctly. Here’s how:
- The _mint function calculated the amount of uniBTC to mint by calling the _amounts function:
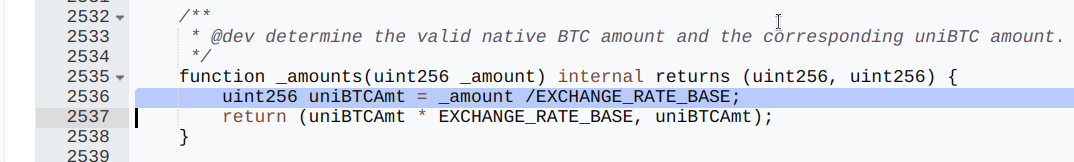
- EXCHANGE_RATE_BASE is set to 1e10.
- The calculation uniBTCAmt = _amount / EXCHANGE_RATE_BASE incorrectly assumes an exchange rate of 1 ETH : 1 uniBTC.
- Since uniBTC has 8 decimals and ETH has 18 decimals, the function fails to account for the actual value difference between ETH and BTC.
Resulting Exploit:
- The attacker sent 30.8 ETH to the mint function.
- Received 30.8 uniBTC, incorrectly valuing ETH equal to BTC.
- This allowed the attacker to obtain high-value uniBTC tokens at a fraction of their actual cost.
Step 3: Exploiting the Miscalculated Exchange Ratio
With the exchange rate being completely skewed (ETH being worth much less than BTC), the attacker minted 30.8 uniBTC by depositing 30.8 WETH. The ratio should have been far higher, but the vulnerability allowed the attacker to receive one uniBTC for each WETH they deposited.
Step 4: Converting uniBTC to WETH for Profit
Once the attacker had 30.8 uniBTC, they quickly exchanged it through Uniswap. First, they swapped 30.8 uniBTC for 27.8 WBTC (wrapped Bitcoin), using Uniswap’s pools. Then, they swapped the 27.8 WBTC for 680.4 WETH. After repaying the original 30.8 WETH flashloan, the attacker walked away with 649.6 WETH in profit, which is approximately $1.7 million.
Simulate the Attack
To gain a deeper understanding of the uniBTC exploit, you can replicate the attack by following the proof of concept (PoC) available here . The PoC includes detailed, step-by-step instructions on how the vulnerability in the uniBTC Vault contract was exploited. By simulating the attack, you can observe the exploit process and gain insights into the attack dynamics and its impact.
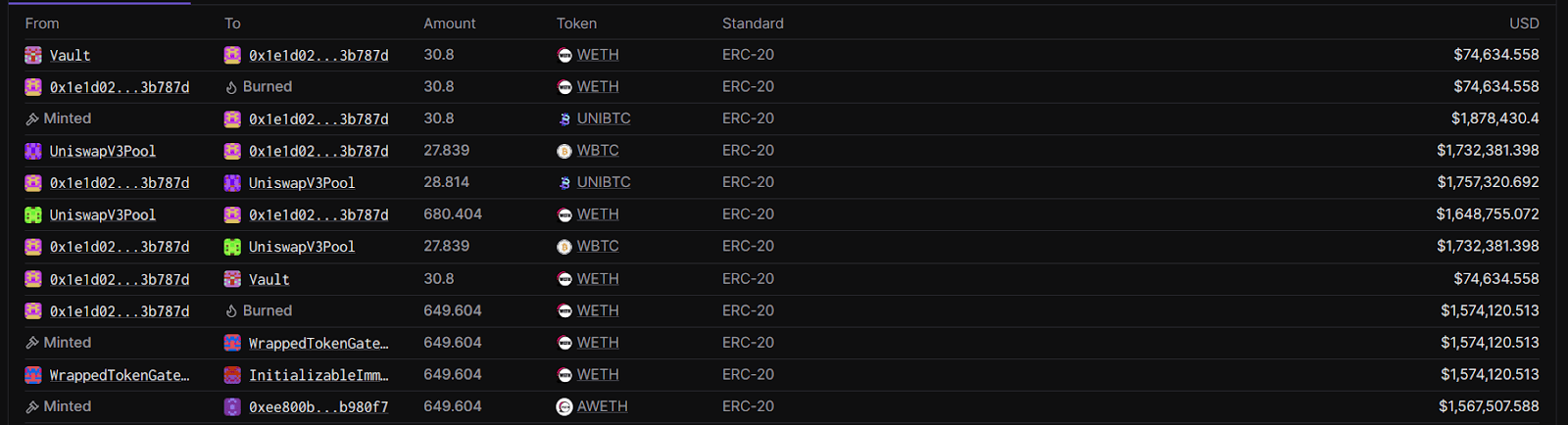
Transaction Analysis
The exploit involving the uniBTC protocol resulted in the theft of significant funds, primarily involving token swaps on Uniswap V3. The attacker executed the following key transactions:
- Exploiter Address: 0x2bFB373017349820dda2Da8230E6b66739BE9F96 – This address initiated the attack, swapping 28.8142 uniBTC for 27.8393 WBTC and subsequently exchanging 27.8393 WBTC for 680.4041 ETH.
- Vault Address: 0x047D41F2544B7F63A8e991aF2068a363d210d6Da – This address received 30.8 ETH directly from Wrapped Ether as part of the exploit.
- Vulnerable Implementation: 0x702696b2aa47fd1d4feaaf03ce273009dc47d901 – The smart contract exploited to facilitate the theft.
- Withdrawal Address: 0xEE800b1b63893Ca1E1b0FA8fEfDc10fAc9B980f7 – The ETH withdrawn from the exploit was subsequently transferred to this address and further dispersed to various other wallets.
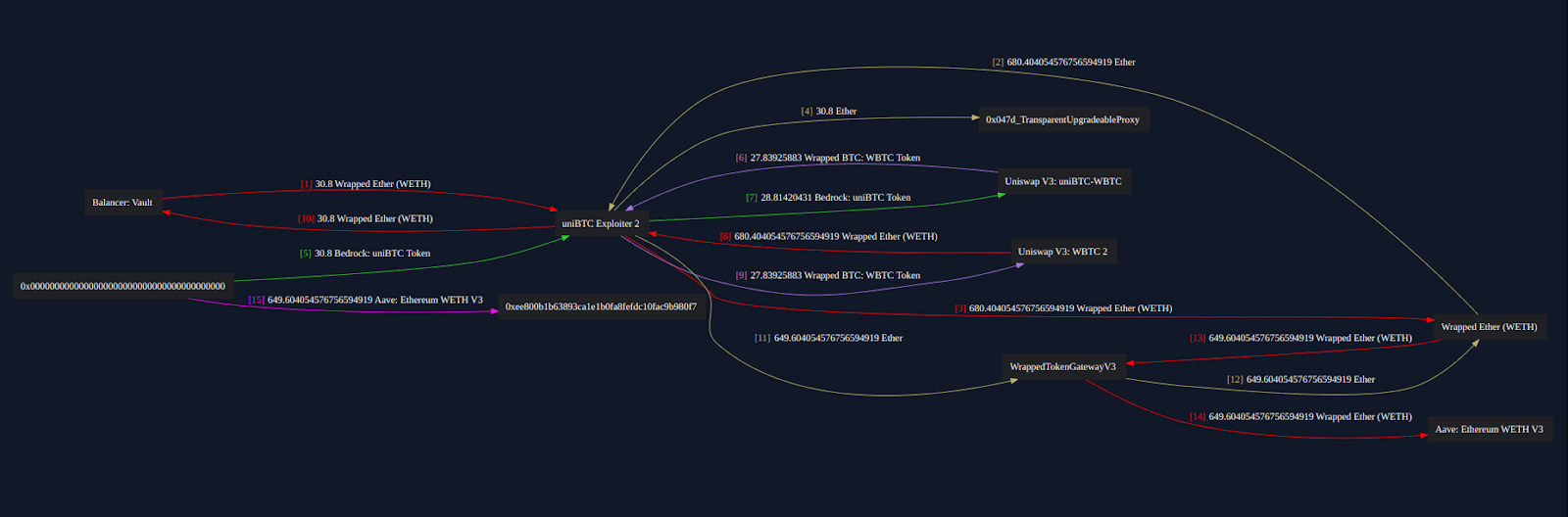
Funds Flow
The attacker borrowed 30.8 WETH via flashloan and used it to exploit the uniBTC minting mechanism, ultimately exchanging their minted uniBTC for WETH. After repaying the original flashloan, the attacker ended up with 649.6 WETH. The rapid conversion and liquidation of uniBTC and WBTC into WETH allowed the attacker to drain Bedrock’s liquidity without leaving a trace of the compromised assets in the system.
Recommendations for Enhanced Security
- Exchange Rate Validation:
The most critical flaw was in how the exchange rate between WETH and uniBTC was handled. Ensure that the exchange ratios between assets are properly calculated and validated to prevent price distortions. - Input Validation in Smart Contracts:
Implement strict validation checks for inputs like asset amounts. In this case, the _amounts function should have enforced realistic conversion ratios based on the value of ETH versus BTC. - Audits of Critical Functions:
Ensure that all critical functions, especially those involved in minting or asset exchanges, undergo thorough security audits. Auditors should simulate edge cases to identify potential vulnerabilities. - Flashloan Protections:
Integrate safeguards against flashloan attacks by limiting how and when certain operations (like minting) can occur, particularly when large amounts of assets are being transferred.
Conclusion
The Bedrock Protocol hack underscores the critical importance of implementing stringent security measures and thorough audits within DeFi platforms. While designed to enable innovative financial operations, the protocol’s vulnerabilities were exploited, leading to significant financial losses. This incident highlights that even advanced and well-structured systems can be compromised if security isn’t prioritized.
As DeFi continues to grow, safeguarding smart contracts and ensuring that proper validation mechanisms are in place must remain at the forefront. Rigorous input validation, meticulous handling of exchange rates, and regular, comprehensive audits are essential for protecting user assets and maintaining trust within the ecosystem.
Organizations specializing in smart contract audits, such as BlockApex, play a crucial role in identifying and mitigating vulnerabilities before they can be exploited. The Bedrock Protocol hack serves as a powerful reminder of the need for constant vigilance and robust security protocols to ensure the ongoing stability and success of decentralized financial systems.