Super Sushi Samurai is an innovative on-chain idle game set in the immersive world of Mizu-Edo, powered by the Blast Network. The game uniquely combines social strategy elements with idle gaming mechanics, offering various play modes such as AFK, Megawar, Boss, The Last Samurai, Showdown, and Lucky Coin. Despite its promising gameplay and vibrant community, Super Sushi Samurai fell victim to a significant security breach shortly after its launch, resulting in a loss of $4.8 million. In this analysis, we will delve into the details of this hacking incident, its impacts, the attack methodology, and recommendations for enhanced security.
Hack Impact
On March 21, 2024, Super Sushi Samurai suffered a devastating security breach, leading to a total loss of $4.8 million from its liquidity pools. The attack exploited a flaw in the game’s token contract, which allowed users to double their token balances by transferring their entire balance to their own address. This vulnerability was catastrophic for the project, causing a 99.9% drop in the token’s value and shaking the confidence of its user base.
Super Sushi Samurai Hack Explained
Step 1: Token Contract Vulnerability
The exploit was initiated through a flaw in the Super Sushi Samurai token contract’s transfer function. The contract was designed to subtract the transferred amount from the sender’s balance before adding it to the recipient’s balance. However, if the sender and recipient were the same address, the contract failed to properly account for the deduction, causing the balance to double instead.
Step 2: Exploitation of the Double-Spending Glitch
The attacker repeatedly exploited this vulnerability by transferring their entire token balance to their own address. When the from and to addresses were the same, the _postCheck function incorrectly added the amount of tokens to the “to” address, effectively doubling the attacker’s token balance. After this, the function attempted to subtract the transferred amount from the “from” address, but since the “from” and “to” addresses were identical, the contract re-assigned the newly doubled balance to the attacker. This allowed the attacker to inflate their holdings significantly in a short period.
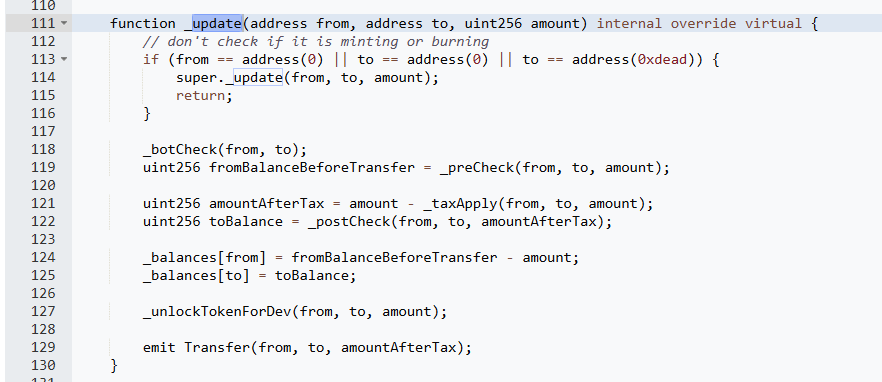
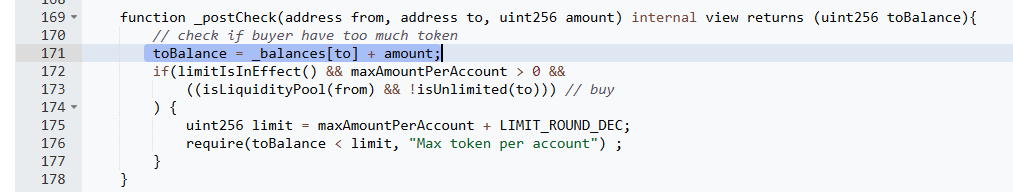
Step 3: Liquidity Pool Drain
With the inflated token balance, the attacker then proceeded to sell the tokens into the liquidity pool (LP), draining $4.8 million in the process. The rapid sell-off not only emptied the liquidity pools but also caused the token’s price to plummet by 99.9%.
Isn’t it astounding that the attacker managed to turn $35 into $4.6 million in just an hour?
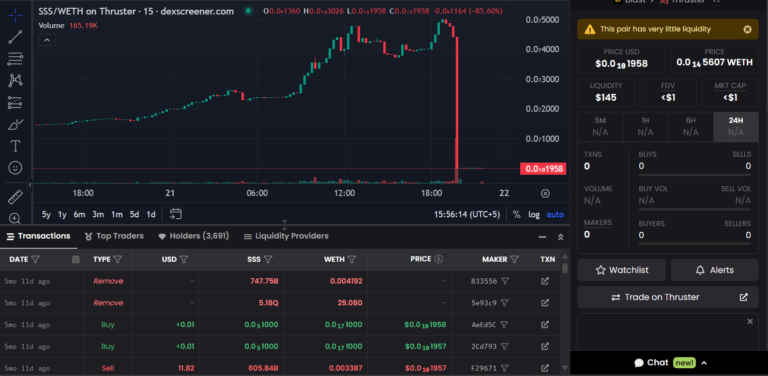
Simulate the Attack
To gain a deeper understanding of the Super Sushi Samurai exploit, you can replicate the attack by following the proof of concept (PoC) available in this GitHub repository: Super Sushi Samurai Hack Analysis PoC. The PoC provides detailed, step-by-step instructions on how the vulnerability was exploited, enabling you to simulate the process and observe how the attack unfolded.
Transaction Analysis
The following are key details of the malicious transactions:
- Attacker Contract: 0xDed85d83Bf06069c0bD5AA792234b5015D5410A9
- Attacker Address: 0x6a89a8c67b5066d59bf4d81d59f70c3976facd0a
- Attack Transaction 1: 0x80012bf784b83baaf28f5549a9f233cae5f70be7afcd8f594dc757d431ed93c4
- Attack Transaction 2: 0x62e6b906bb5aafdc57c72cd13e20a18d2de3a4a757cd2f24fde6003ce5c9f2c6
- Attack Transaction 3: 0xac3400e3d536ac23c10fdd2c06e1faf8d5de5b797df8433e9b5ab74b102a4e35
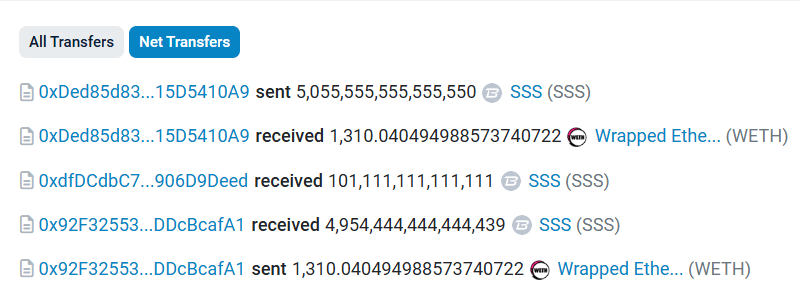
Funds Flow
The attacker initiated the exploit with a mere $35 and, within an hour, managed to turn it into $4.6 million by exploiting the double-spending glitch. The rapid accumulation and subsequent liquidation of tokens into the liquidity pools resulted in the complete drainage of $4.8 million, leaving the project in financial ruin.
Recommendation for Enhanced Security
To prevent such vulnerabilities in the future, it is critical to implement several security measures:
- Input Validation: Ensure that the smart contract validates inputs, especially in critical functions like transfers, to prevent unintended behaviors.
- Proper Handling of Edge Cases: The contract should account for all edge cases, such as transfers where the sender and recipient are the same, to avoid exploits like double-spending.
- Comprehensive Audits: Conduct thorough and continuous audits of smart contracts, focusing on both logic and edge case testing, to identify and fix potential vulnerabilities before deployment.
- Access Controls: Implement strict access controls and modifiers on critical contract functions to prevent unauthorized manipulations.
Conclusion
The Super Sushi Samurai hack highlights the urgent need for robust security measures and comprehensive audits in the GameFi space. Despite the platform’s innovative features, it wasn’t immune to significant vulnerabilities. This incident emphasizes that every project, no matter how promising, faces potential risks if security is not a primary focus.
Given the rapid evolution of GameFi, ensuring the security of smart contracts must be paramount. Adopting strong security practices, conducting regular audits, and maintaining open communication with the community are crucial to safeguarding both the platform and its users.
Organizations like BlockApex, with their specialized expertise in smart contract auditing, are instrumental in identifying and addressing vulnerabilities before they can be exploited. This hack serves as a clear reminder of the importance of maintaining stringent security protocols to build trust and support the sustained growth of GameFi platforms.































