🚀 Audit Portfolio Dashboard is Live
Security
Explore Audit
Portfolio

🚀 Audit Portfolio Dashboard is Live

Cross-chain bridges achieve interoperability between different blockchain networks. Ensuring the security of these bridges is essential to protecting against vulnerabilities and exploits. BlockApex offers comprehensive cross-chain bridge audit services designed to secure your bridge infrastructure and protect your digital assets.

















NFT platforms using cross-chain bridges to facilitate the transfer of NFTs across various blockchains need audits to ensure the security and integrity of these transactions.



Our Cross-Chain Bridge Audit Process
Our cross chain bridge auditors conduct a thorough review of your bridge’s code, identifying vulnerabilities and logic flaws. This ensures your bridge’s codebase is secure and reliable.
Our smart contract auditors conduct a comprehensive review of the smart contracts involved in your cross-chain bridge operations, identifying vulnerabilities and logic flaws to ensure their security and reliability.
We evaluate your network and infrastructure for potential vulnerabilities and resilience against attacks. This includes reviewing your hosting environment and network configurations for overall security.
We conduct penetration testing by performing simulated attacks to assess your bridge’s defenses against external threats. This process identifies potential vulnerabilities and ensures your bridge is robust enough to withstand real-world attacks.
Our auditors assess your bridge’s performance, identifying and addressing any inefficiencies. This includes evaluating scalability, load times, and overall responsiveness to optimize user experience.
We provide a comprehensive final report detailing our findings, risk assessments, and actionable recommendations. This report guides you through the remediation process and ensures your bridge's security and efficiency.
Frequently asked Questions
A cross-chain bridge audit is a thorough examination of the code and infrastructure of a cross-chain bridge to identify and fix any security vulnerabilities.
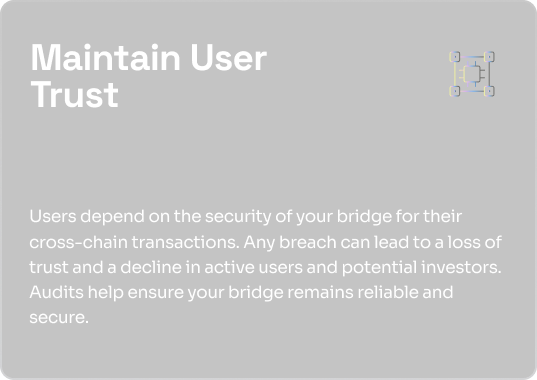
A bridge audit protects digital assets from security threats, ensures compliance with industry standards, and builds trust with users.
The audit covers code review, transaction flow analysis, smart contract audit, network and infrastructure audit, penetration testing, and performance assessment.
Potential security risks include code vulnerabilities, unauthorized access, transaction errors, and overall system weaknesses that could be exploited by malicious actors.
While Web3 projects can conduct their own audits, but using a professional cross chain audit company is recommended to ensure a thorough and unbiased assessment, leveraging expert knowledge and experience.
The duration of a bridge audit is generally 2 - 4 weeks but can vary depending on the complexity and size of the project. Contact us with specific project details for a detailed timeline.
We believe in transparent pricing to accommodate various budgets. The cost for a typical audit is around $7000-$15000 but can vary depending on the complexity and size of the project. Contact us for a tailored quote based on your project's needs and complexity.