On September 3, 2024, Onyx DAO, a protocol derived from Compound Finance, suffered a severe breach. This incident led to a loss of approximately $3.8 million in various cryptocurrencies, primarily affecting the VUSD stablecoin. The breach was facilitated by an old precision issue known in the forked Compound V2 code base that Onyx DAO utilized.
Hack Details
The attackers deployed a malicious contract to manipulate the protocol’s market calculations, taking advantage of the precision loss vulnerability that was known but not addressed adequately in Onyx’s implementation. Security firms Cyvers and PeckShield first noticed suspicious activities, pinpointing the exact methods by which the digital assets were illicitly extracted.
Execution of the Hack
- Vulnerability Exploitation: The precision loss issue allowed the attacker to create transactions that manipulated the market’s exchange rates drastically. This manipulation enabled the withdrawal of 4.1 million VUSD and other digital currencies like XCN, DAI, WBTC, and USDT.
- Attack Mechanism: By initiating transactions that exaggerated the value of small deposits, the attackers were able to withdraw amounts far exceeding their original stakes.
Immediate Consequences
The aftermath of the exploit was not just financial but also reputational. The value of Onyx’s tokens plummeted, undermining investor confidence and destabilizing the protocol’s market position. The attackers converted some of their loot to ETH, but a large portion of the stolen assets remained unswapped, suggesting a calculated move to avoid immediate traceability.
Onyx’s Response
Upon detecting the breach, Onyx DAO promptly acknowledged the incident and began an investigation. They have since been working on measures to tighten their security protocols and restore trust among their user base.
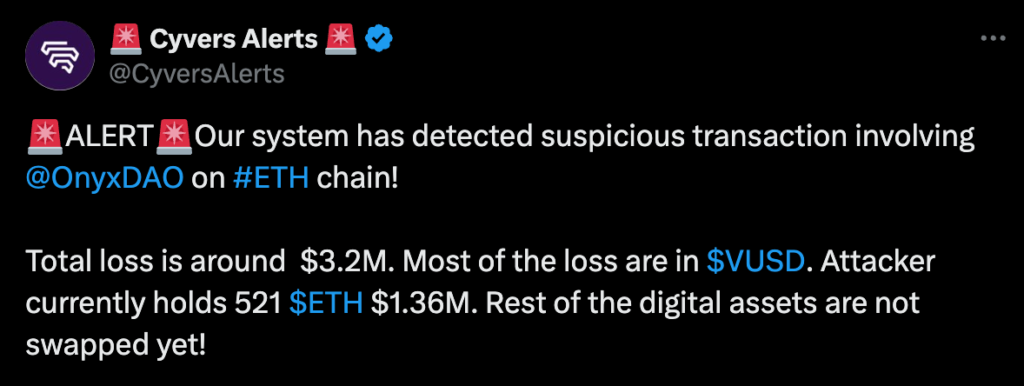
“Our system has detected a suspicious transaction involving OnyxDAO on the ETH chain! The total loss is around $3.2 million [at the time]. Most of the losses are in VUSD. Attacker currently holds 521 ETH ($1.36 million). The rest of the digital assets are not swapped yet,”
Simulate the Attack
To better understand the Onyx DAO exploit, you can replicate the attack using a proof of concept (PoC). Here is a link, you can create one by analyzing the specific vulnerability in the OnyxDAO smart contract. Here is the breakdown of tx
Initial Setup:
- Contract Deployment: A malicious contract is deployed to Ethereum, crafted to exploit this identified vulnerability.
Exploitation of Vulnerability:
- Targeted Contract: The attack focuses on a specific function in the Onyx DAO’s contract that handles market exchange rates. This function, due to inheriting from the Compound V2 codebase, contains a precision error when calculating exchange values.
- Malicious Execution: The attacker invokes this vulnerable function using their deployed malicious contract. The contract is tricked into miscalculating by inputting values that exploit the rounding error.
Manipulation of Transactions:
- Inflating Values: By executing several transactions that deliberately manipulate input data, the attacker inflates the value of their holdings within the protocol.
- Minting Excess Tokens: Utilizing the miscalculated exchange rates, the attacker mints an excessive amount of the protocol’s native tokens (e.g., VUSD) beyond their legitimate entitlement.
Extraction of Assets:
- Conversion to Stablecoins and Crypto: The excessively minted tokens are quickly converted into various cryptocurrencies, primarily into stablecoins like USDT and DAI, and other values like ETH and WBTC.
Liquidation:
- Cashing Out: The attacker begins the process of cashing out the assets through different exchanges, converting them into ETH or other less traceable cryptocurrencies.
- Slow Liquidation: To avoid detection and enhance anonymity, the attacker employs a slow liquidation strategy, spreading out the conversion over time and through multiple decentralized exchanges.
Transaction Analysis
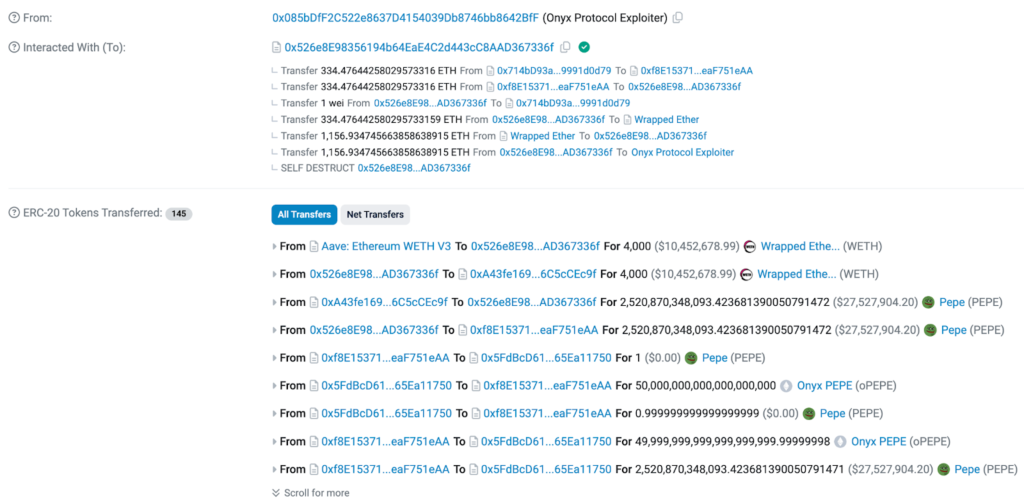
The following are key details of the malicious transactions:
Attacker’s Address: 0x085bdff2c522e8637d4154039db8746bb8642bff
Malicious Contract: 0x526e8e98356194b64eae4c2d443cc8aad367336f
Vulnerable Smart Contract Address: 0x5fdbcd61bc9bd4b6d3fd1f49a5d253165ea11750
Attack Transaction Hash: 0xf7c21600452939a81b599017ee24ee0dfd92aaaccd0a55d02819a7658a6ef635
Funds Flow
The attackers executed a sophisticated attack by manipulating the protocol’s exchange rate calculations through minting small shares and performing substantial transactions, which leveraged the precision loss to withdraw large amounts of assets.
Recommendation for Enhanced Security
To prevent such vulnerabilities in the future, it is critical to implement several security measures:
- Order of Operations: To prevent precision loss, always perform multiplication operations before division. This sequence helps maintain the integrity of the numerical values throughout the calculation process.
- Handling of Results and Operands: Store the results of multiplication and division operations in integers that have a larger bit size to ensure accuracy. Additionally, ensure that the operands involved in these operations are also integers of the same size to avoid computational errors.
- Proper Handling of Edge Cases: The contract should account for all edge cases, such as transfers where the sender and recipient are the same, to avoid exploits like double-spending.
- Comprehensive Audits: Conduct thorough and continuous audits of smart contracts, focusing on both logic and edge case testing, to identify and fix potential vulnerabilities before deployment.
Conclusion
The Onyx DAO hack underscores the critical importance of robust security measures and thorough audits in the DeFi space. Despite the protocol’s innovative features, this incident revealed that even well-established platforms are vulnerable if security isn’t prioritized. It serves as a reminder that every project, regardless of its potential, is at risk without a strong security foundation.
Organizations like BlockApex, with their specialized expertise in smart contract auditing, are instrumental in identifying and addressing vulnerabilities before they can be exploited. This hack serves as a clear reminder of the importance of maintaining stringent security protocols to build trust and support the sustained growth of DeFi platforms.