Game theory, the study of systems where competitors’ behaviors impact each other in both cooperative and competitive environments, plays a crucial role in understanding and designing decentralized systems like blockchain. The core principle of game theory is to analyze how the behaviors of different parties—whether cooperative or competitive—affect the overall outcome of the system. In the context of blockchain ecosystems, game theory helps model the interactions of various actors, ensuring the system’s integrity even when these actors are primarily motivated by self interest.
In blockchain, the behaviors of actors are often shaped by the consensus mechanism in place. Whether using Proof of Work (PoW) or Proof of Stake (PoS), the goal is to design a system where, even if all participants act to maximize their personal incentives, the system still functions correctly. This requires ensuring that even when actors attempt to exploit vulnerabilities—through fraud or dishonesty—the blockchain remains secure and stable.
For example, in PoW systems, the assumption is that if at least two thirds (or 51%) of the validators are honest, the blockchain will function as intended. However, if dishonest validators control 51% of the network, they could potentially compromise the blockchain. Economically, a 51% attack is costly, as it requires significant computational resources. Thus, the cost of such an attack generally discourages dishonest behavior. Political motives might drive entities like governments to execute a 51% attack to disrupt cryptocurrencies in favor of their national currencies. In such a scenario, apart from economic security, social security is also required to prevent such an authority from taking over. This is where game theory comes in.
Game theory offers a framework to analyze and design mechanisms that promote behaviors leading to the system’s stability, not just from an economic standpoint but also from a social security perspective. Community trust and external validation, such as through Decentralized Autonomous Organizations (DAOs) or social media platforms, play a critical role in reinforcing the integrity of blockchain networks.
In game theory, the analysis of players’ behaviors and the strategies they adopt helps determine whether the system operates in a cooperative or competitive manner. To understand this better, have a look at the prisoner’s dilemma. The ultimate aim is to find the Nash equilibrium—a state where the strategies of all players align with the optimal outcome for the system. By applying game theory to blockchain design, we can create systems that encourage cooperation and ensure long term stability, even in the face of self interested actors.
Game Theory in Security Audits
When auditing systems—particularly those involving economic interactions—game theory principles are invaluable. As a security auditing company, it is essential to account for all potential attack vectors during the design and evaluation of systems. This approach not only prevents collusion but also helps strengthen protocol designs.
At BlockApex, the token engineering team applies game theory principles to ensure robust security during audits. These principles are particularly relevant when designing blockchains, protocols, and decentralized financial systems.
Types of Games in Economic Systems
Game theory categorizes systems into different types of games based on participant behaviors and outcomes:
-
Zero Sum Games:
In zero sum games, the gain of one participant is exactly balanced by the loss of another. For example, economic trades often follow this model, where one party profits and the other incurs a loss.
-
Cooperative Games:
Unlike zero sum games, cooperative games allow all participants to benefit simultaneously. An example would be a race with multiple winners, where each participant can achieve a position of merit (e.g., 1st, 2nd, or 3rd place).
-
Multi Dimensional Games:
Some games extend beyond a single goal. Participants may succeed in one category while falling short in another. Designing systems with these multi dimensional objectives in mind requires modeling all potential dimensions to achieve fairness and utility for all involved parties.
Application of Game Theory in Security Audits
Game theory’s ability to analyze behaviors extends to security audits. By understanding the dynamics of participant interactions, systems can be designed to withstand collusion, market manipulation, and other vulnerabilities. This proactive modeling ensures a secure and balanced ecosystem, meeting the expectations of fairness and trust.
-
Incentive Compatibility of Consensus
Incentive compatibility is a cornerstone principle in the design and security of blockchain protocols. It ensures that all participants—whether they are validators, liquidity providers, or arbitrageurs—act in ways aligned with the protocol’s intended goals, even when pursuing their self interest. This alignment is critical for maintaining the integrity, usability, and attractiveness of a blockchain ecosystem.
At the heart of consensus mechanisms, particularly in proof of stake (PoS) systems, lies the challenge of ensuring validators remain committed to the network. Unlike proof of work (PoW) systems, where infrastructure investments create long term validator loyalty, PoS validators can unstake assets and move to competing chains with ease. This mobility introduces a greater risk of disloyalty and destabilization, necessitating carefully crafted incentive structures.
1- Liquidity Providers and Yield Farming
In automated market makers (AMMs), liquidity providers (LPs) face unique challenges. Without sufficient rewards, LPs are prone to hop between protocols offering higher incentives. This behavior, observed during the DeFi summer of 2019, underscores the inherent incentive incompatibility of many AMM models. Traditional transaction fees often fail to compensate LPs adequately, especially when accounting for losses to arbitrageurs—known as impermanent loss.
To counteract this, yield farming emerged as a solution. By offering additional token rewards, protocols aim to retain LPs by fostering loyalty and compensating for economic inefficiencies. However, these measures are not without their costs; protocols like SushiSwap have spent millions annually to attract and maintain liquidity. The Vampire attack by Sushiswap was quite a rage back then.
The frontier lies in creating systems that are naturally incentive compatible without relying excessively on yield farming or similar mechanisms. For example, Osmosis, a decentralized exchange (DEX), minimizes losses by enabling the protocol to capture arbitrage profits internally. By controlling the first transaction of each block, the protocol ensures these profits are retained within the ecosystem, reducing dependence on external incentives.
The incentive structure of a protocol has direct security implications. If a protocol fails to retain liquidity or validators, its reliability is compromised. For example, diminished liquidity can lead to price manipulation within AMMs, eroding user trust and jeopardizing the protocol’s legitimacy. Security auditors must therefore evaluate not just the code but also the economic models underpinning the system, using tools like game theory to simulate potential vulnerabilities.
2- Incentive Compatibility in Ethereum
In Ethereum’s PoS model, validators are rewarded proportionally to their staked Ether, creating a direct incentive to act honestly. This design ensures that validators prioritize the network’s stability, as any malicious behavior could devalue their holdings. Inflation mechanisms, such as token issuance for block rewards, play a crucial role in sustaining validator participation. However, these mechanisms must be carefully managed to avoid hyperinflation, which could undermine the token’s value and destabilize the network.
The implementation of Ethereum Improvement Proposal (EIP-1559) introduced a deflationary mechanism by burning a portion of transaction fees. This balanced inflationary rewards with deflationary pressures, maintaining Ether’s value while incentivizing validator participation. However, the effectiveness of such mechanisms diminishes in Ethereum’s emerging roll up centric model.
Ethereum’s roll up centric architecture represents a shift toward application specific chains, where much of the computational load is handled off the main blockchain. While this improves scalability, it reduces the demand for Ether on the base layer. Transactions occur less frequently on the main chain, except for high value operations, leading to a significant drop in network activity. This lower demand for Ether, combined with existing inflationary pressures, threatens the economic stability of the blockchain.
The current roll up centric model raises concerns about whether it remains incentive compatible. For validators, whose rewards rely on network demand and inflationary rewards, a decline in Ether demand undermines their economic incentives. This misalignment could impact Ethereum’s long term sustainability and the effectiveness of its PoS mechanism.
Economic security audits play a critical role in addressing these challenges for Ethereum. Auditors must evaluate the soundness of inflation schedules, tokenomics, and incentive mechanisms to ensure they align with Ethereum’s design objectives. For example, protocols operating on Ethereum often establish predefined inflation schedules to reward users, but these schedules require rigorous simulation and analysis to justify their parameters. Failing to consider factors such as Ether demand, adoption rates, and market dynamics can lead to vulnerabilities or inefficiencies, as seen in historical cases where poorly designed inflation rates resulted in economic exploitation. In addition to inflation schedules, parameters like interest rates and realization rates must be carefully modeled. Misconfigurations in these areas can create opportunities for exploitation or destabilize Ethereum based protocols.
3- Economic Lessons from Meme Coins
Interestingly, meme coins provide a contrasting perspective. Their value lies less in economic incentives and more in shared belief and social consensus. However, even in meme driven systems, subtle economic incentives can exist. But mainly we don’t see farming in projects targeting this domain.
So we can drive the conclusion that incentive alignment is the backbone of any blockchain project.
Selfish mining; block withholding
One of the most discussed concepts in blockchain economics is selfish mining. Introduced as a potential attack on the fairness of Proof of Work (PoW) systems, selfish mining revolves around a miner withholding newly mined blocks from the network. Instead of broadcasting the block, the selfish miner secretly mines on top of it, creating a private chain.
1- How Selfish Mining Works
In a typical PoW scenario, miners compete to solve cryptographic puzzles to add blocks to the blockchain. Upon mining a block, they broadcast it to the network, ensuring all participants mine on the same chain.
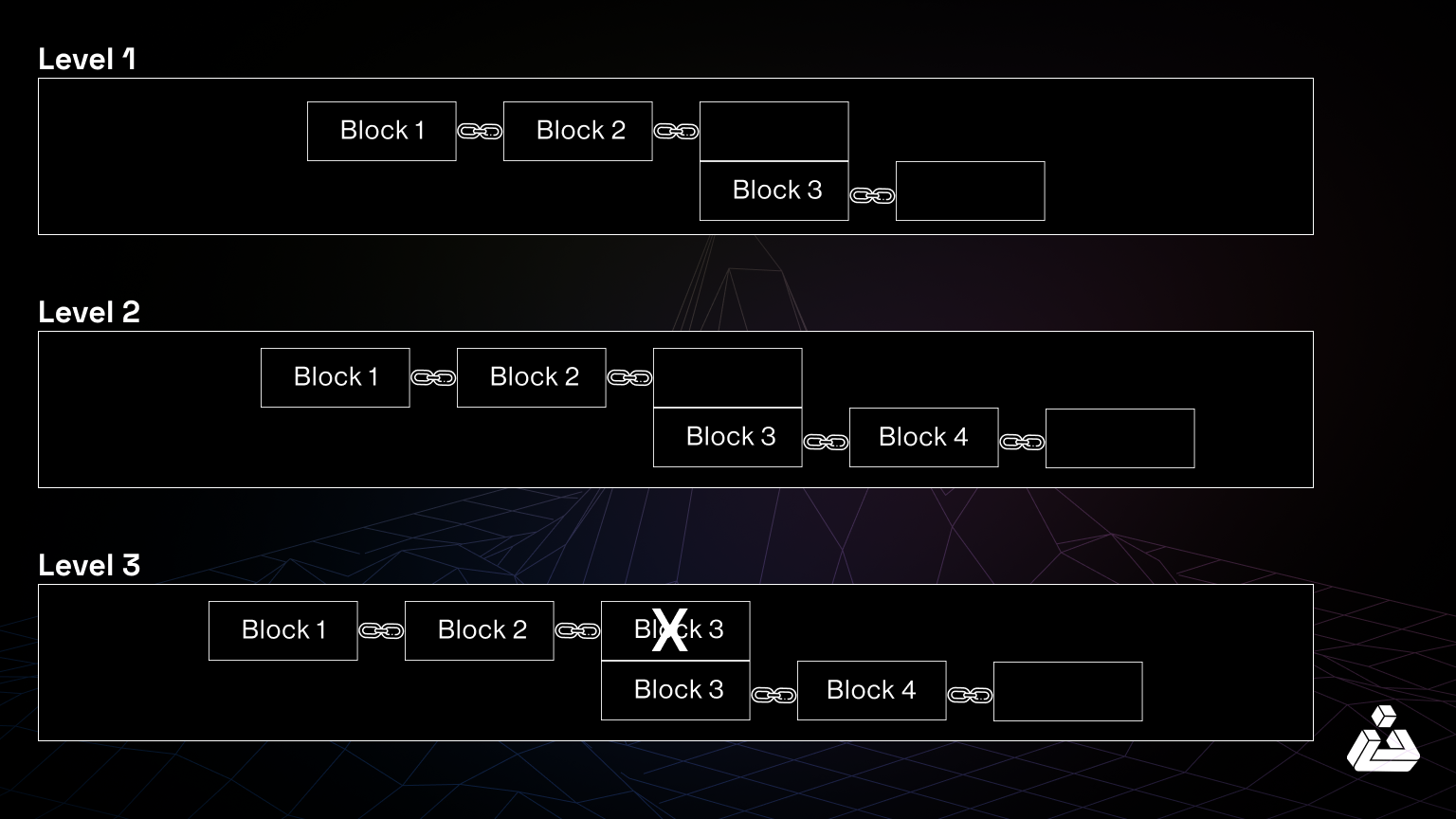
However, selfish miners exploit the inherent block propagation delays. By withholding a block:
- Network Duplication: The rest of the network continues mining on the older block, unaware of the withheld block.
- Private Chain Advantage: The selfish miner uses this time to mine subsequent blocks on their private chain, gaining a head start.
- Blockchain Forking: If the private chain becomes longer than the public chain, the selfish miner publishes it, invalidating the work done by other miners and claiming the rewards.
2- Economic Implications
Initially, it was assumed selfish mining might break the system’s fairness by allowing miners with as little as 30% of the network’s hash power to earn disproportionately higher rewards. Yet, Satoshi Nakamoto’s design cleverly countered this threat. The majority of the network, holding over 50% of the computational power, is statistically favored to extend the longest valid chain. Consequently, selfish miners find their gains diminishing unless they control a significant portion of the hash power.
3- Mitigating Selfish Mining
While Bitcoin’s original design mitigates selfish mining effectively, ongoing research and modifications to protocol parameters (e.g., block propagation speeds and fork resolution rules) continue to strengthen defenses. Innovative ideas such as penalties for frequent forks or alternate consensus algorithms like Proof of Stake (PoS) also address these challenges.
Verifiers Dilemma
Another significant challenge in blockchain ecosystems is the Verifier’s Dilemma. In decentralized networks, nodes validate transactions in blocks to ensure correctness before propagation. However, only the block producer receives rewards, leaving other validators with no direct incentive to verify transactions. Without proper incentives, non producer nodes may skip transaction verification, trusting the block producer implicitly. This blind trust creates vulnerabilities, including potential acceptance of malicious blocks, double spending attacks, or state corruption.
To address the Verifier’s Dilemma, some approaches propose distributing rewards among validators as well as producers. For instance:
- Reward Sharing: A portion of the block reward could be allocated to nodes that verify transactions within a quorum.
- Optimized Quorum Size: Limiting the number of verifying nodes to a small percentage of the network ensures efficiency without compromising security.
- Dynamic Incentive Models: Introducing a tiered reward system ensures block producers remain highly incentivized while validators are adequately compensated.
By ensuring the validation process is economically viable for all participants, the Verifier’s Dilemma can be mitigated without compromising network security or decentralization.
Transaction Quality Trilemma
Blockchain systems face a fundamental challenge often referred to as the Transaction Quality Trilemma. This trilemma highlights the difficulty of simultaneously achieving three critical goals:
- Low Fees: Minimizing transaction costs.
- Censorship Resistance: Ensuring inclusivity and decentralization.
- Spam Prevention: Avoiding network congestion through spam transactions.
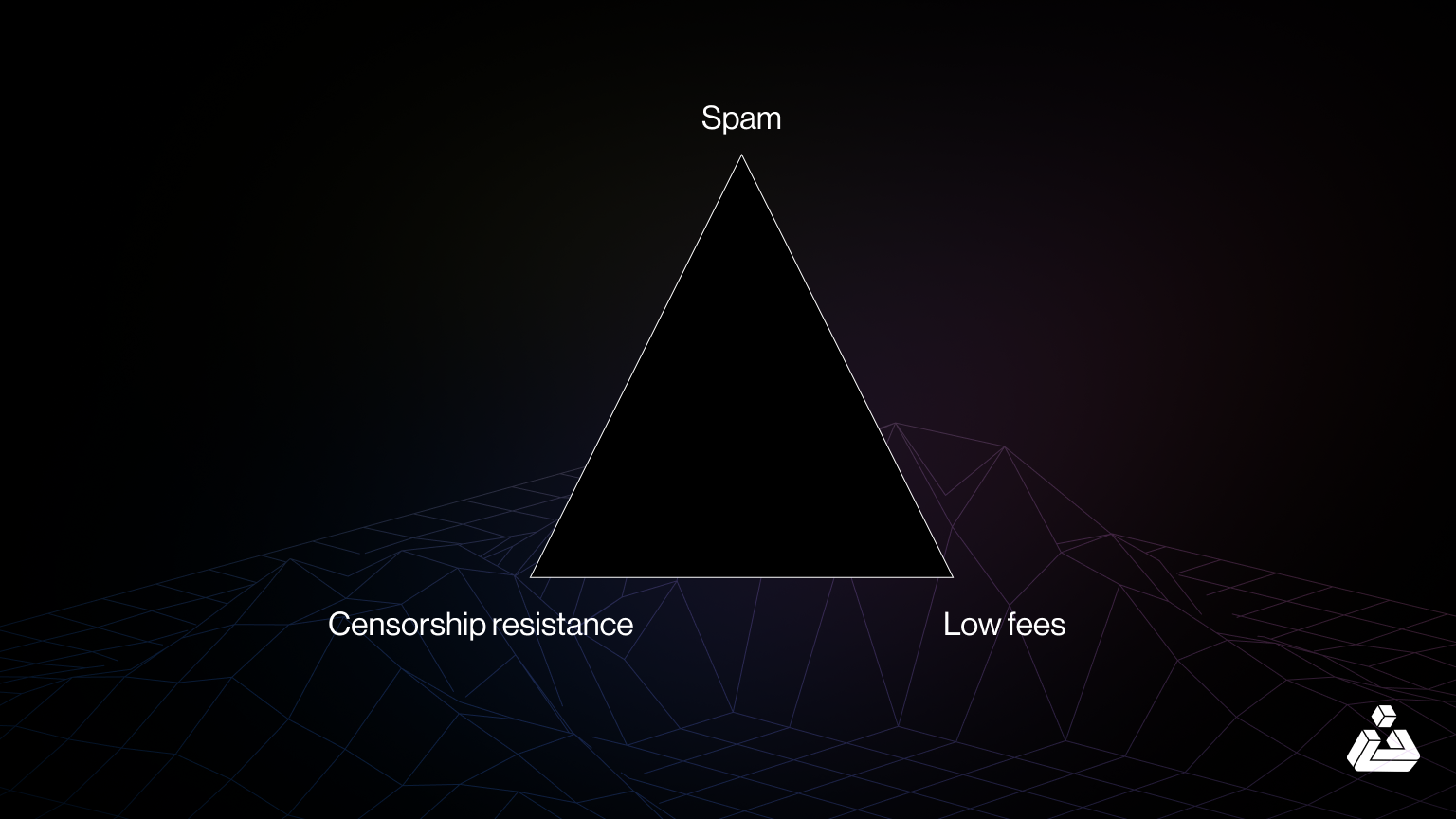
Blockchain systems approach the trilemma differently based on their priorities. For example, Ethereum addresses spam prevention with its gas fee model, but during events like the 2016 DoS attack, low-cost storage updates allowed attackers to overwhelm the network. Adjusting gas fees resolved this issue, showing the need for dynamic recalibrations.
Bitcoin emphasizes censorship resistance and security, sacrificing low fees, which can make smaller transactions less viable. Meanwhile, EOS uses a resource staking model to limit spam, introducing censorship risks and marginalizing smaller participants.
Solving the trilemma requires understanding user behavior and designing incentives using game theoretic principles. Fee structures should reflect the costs of computation, storage, and bandwidth while preventing spam without deterring legitimate users. For example, mechanisms like EIP-4844 allow Ethereum to dynamically adjust blob fees to prevent abuse while maintaining network usability.
Non-Determinism
In blockchain systems, particularly in consensus mechanisms like Ethereum, deterministic behavior is crucial. This means that if a certain list of transactions is processed on multiple nodes, each node should reach the same final state for the system to achieve consensus. However, non determinism can creep in, causing different nodes to produce different outputs even when they run the same code with identical inputs.
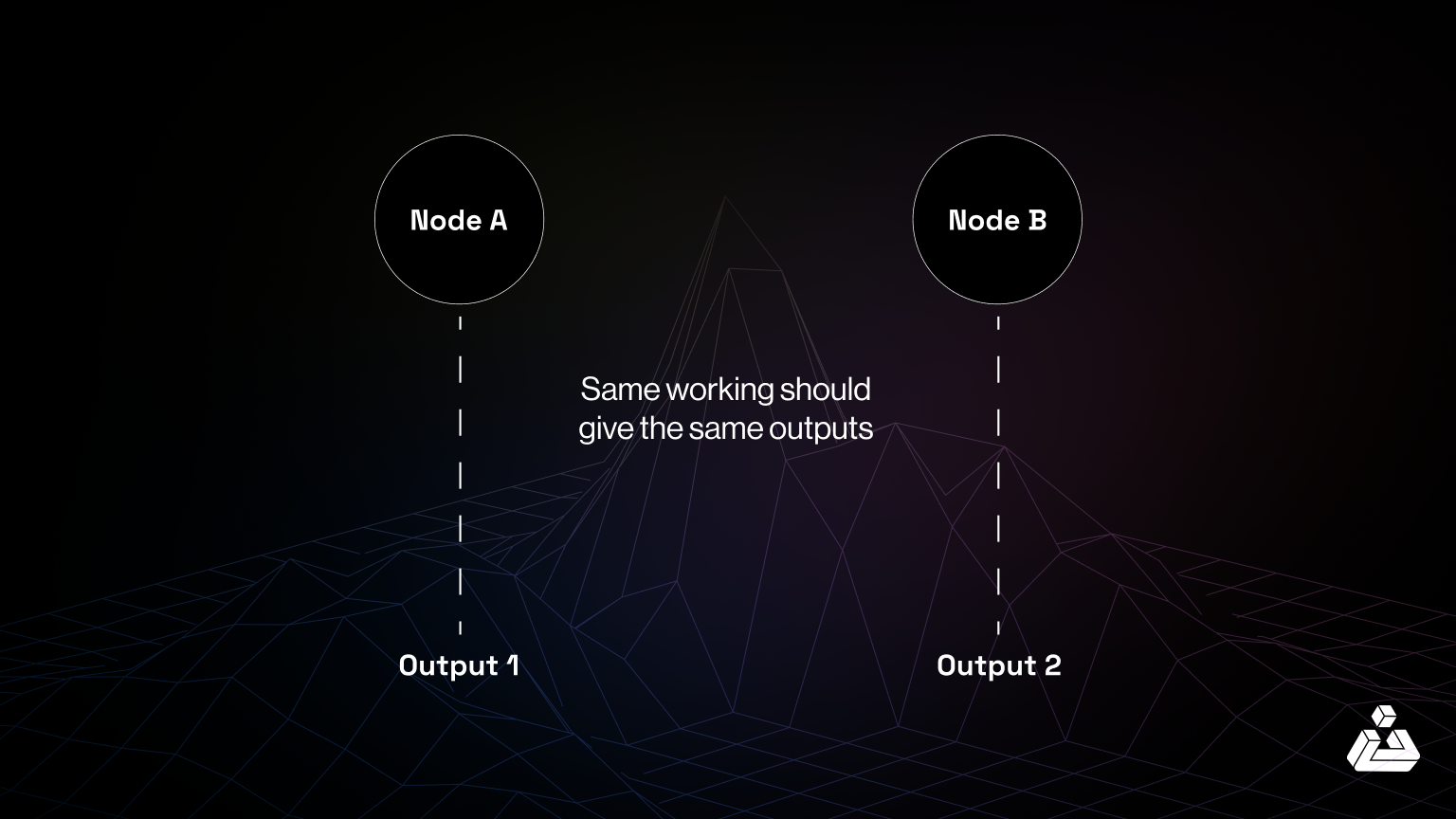
Non-determinism in blockchain can arise due to subtle issues in the code. For instance:
- Hash Tables/Maps: In languages like Go or Rust, hash tables (maps) can introduce non determinism because the order of keys and values may differ with each execution due to how memory is allocated on the heap. This unpredictability can result in different machines processing the same list of transactions in a different order, leading to inconsistent states across nodes.
- Timestamps: Another common cause of non determinism is the use of timestamps. Since timestamps are generated by individual machines and may not always be synchronized perfectly, they can lead to discrepancies in the output of the same transactions when executed on different nodes.
This behavior is problematic because, for a blockchain to function properly, every node must agree on the order and state of transactions. Any divergence in the execution flow jeopardizes the consensus and can halt the blockchain entirely.
Game theory is used to study and predict the behavior of participants in a decentralized system, like a blockchain network. In this case, understanding the incentives behind non determinism is critical.
1- Protocol Designers’ Incentives
Developers of blockchain systems may have incentives to introduce bugs or manipulate consensus. For example, in cases like the Terra/Luna ecosystem, developers may have intentionally induced flaws in smart contracts or systems (e.g., bugs in Anchor Protocol) that allowed them to profit or manipulate outcomes. Game theory helps in evaluating these incentives and understanding how the behavior of developers or malicious actors can impact the protocol.
2- Fraud Committers and Verifiers
In the context of rollups (Layer 2 solutions), fraud committers can exploit inefficient verification mechanisms. For example, if a fraud commit is detected, the mechanism should rollback the state of the blockchain to a point before the fraud occurred. However, if the fraud submitter can manipulate the system by submitting an increasing number of pending transactions or states to be deleted, it could create an unbounded loop, preventing the block producer from meeting the 12 second block time limit. This inefficiency in handling fraud can lead to a situation where the fraud is not punished, and instead, the validating node (or fraud verifier) gets slashed for failing to produce the block in time.
Nothing at Stake
The “Nothing at Stake” problem is a significant issue in Proof of Stake (PoS) consensus mechanisms, where validators are incentivized to support multiple competing chains because the risk of misbehavior is low. This scenario often occurs when validators, seeing no substantial penalty for validating conflicting blocks, may attempt to “game” the system by supporting both chains to maximize their chances of earning rewards.
An example of this occurs in Ethereum’s early PoS systems, where validators might stake on multiple forks of the chain, knowing that the penalties for such actions weren’t always well defined. This creates a situation where malicious validators have “nothing at stake” since the cost of malicious behavior is not significant, and they can continue to profit by supporting multiple chains. In game theory terms, this is a situation where the Nash equilibrium is unstable, as validators have incentives to act in ways that undermine the integrity of the network.
To address this, Ethereum’s implementation of penalties for dishonest behavior—particularly slashing—aims to discourage validators from participating in competing chains. However, the problem persists in systems that lack stringent economic penalties or have ineffective verification mechanisms.
Governance
In blockchain governance, particularly within decentralized autonomous organizations (DAOs), the challenge is ensuring that decisions made through voting are in the best interests of the entire network. The concentration of voting power in the hands of large token holders is a prominent issue, as these actors can disproportionately influence governance decisions, often in ways that benefit their own interests.
An example of this occurred during the rise of DeFi protocols like Compound and MakerDAO, where governance power was largely controlled by a small number of large stakeholders, giving them outsized influence over protocol upgrades or changes. In these scenarios, smaller token holders had little to no impact on the governance process, which undermined the decentralization principle that is central to blockchain systems.
Game theory can help address this by applying quadratic voting models, where voting power increases at a diminishing rate with the number of tokens held. For instance, using quadratic voting, if a token holder wanted to increase their voting power, they would need to expend exponentially more tokens to do so. This reduces the risk of centralization and creates a more balanced governance system.
Misuse Of refunds
In the Near ecosystem, users are required to pay upfront for storage when creating accounts. This differs from Ethereum, where users don’t directly pay for storage at the point of account creation. However, Near’s approach introduces a refund mechanism—if a user deletes their account within the paid duration, they can reclaim the storage fees.
A potential vulnerability arises in the case where a smart contract subsidizes the storage fees on behalf of the user. In such cases, if the user deletes their account, the refund should ideally go back to the smart contract. However, if the refund is given to the user, it could lead to an exploitation scenario where the user drains the contract’s funds by repeatedly registering and deleting accounts. This highlights the need for protocol designers to be mindful of how fees are passed to users and how refunds are handled to avoid such exploits.
Final Thoughts
By applying game theory to design protocols with stronger incentives for honest behavior, blockchain developers and auditors can create systems that are resilient to attacks, collusion, and market manipulation. At BlockApex, we leverage game theory principles to enhance the security of blockchain protocols through comprehensive audits that examine both technical vulnerabilities and the economic incentives that drive participant behavior. By evaluating the dynamics of consensus mechanisms, incentive structures, and potential attack vectors, we help ensure that blockchain systems remain secure, fair, and resilient against malicious actors. Contact us today to secure your blockchain protocols with our expert audits and innovative approach!































